Understanding command and control (a.k.a. C2, CnC or C&C), is critical to effectively detect, analyze, and remediate malware incidents. The phrase "command and control", which has its origins in military terminology, refers to the approach an attacker uses to take command of and exercise control over a compromised system. In the world of malware, C2 is typically used to execute arbitrary commands on a victim system, report the status of a compromise to an attacker, or exfiltrate information. C2 channels may be used to commandeer an individual host or control a botnet of millions of machines.
Why C2 Matters to Malware Analysts
Consider the scenario where a suspicious file is detected on an enterprise workstation, perhaps the result of a host-based anomaly detection capability. As a malware analyst, one of your primary tasks is to determine if and how the suspect file is controlled by an external actor. During this exploration, discovery of a functional command and control channel is a milestone. Why? Because this finding could mean your organization has officially lost control of its network.
If someone has command and control of machines within your enterprise?whether it's an "advanced threat", a criminal, or amateur hacker?you have a problem, and a potentially serious one. Uncovering C2 channel(s) while performing malware analysis may involve intensive, systematic behavioral and code analysis to emulate the intended victim environment and establish the specific C2 protocol used. Code obfuscation and encryption routines make this more challenging, but it's doable with practice and persistence
Command and Control Protocols
Attackers use a variety of techniques and protocols for command and control. Internet Relay Chat (IRC), which facilitates group messaging via a client-server model, was a common C2 protocol for many years. However, IRC is rarely used in business environments, so it is easy for defenders to detect this potentially malicious traffic. As a result, attackers consider alternative protocols that allow them to better hide in plain sight. HTTP is an obvious choice because of its prevalence across the corporate enterprise.
Consider, for example, the Zeus/Zbot trojan. This well-documented banking trojan aims to steal banking login credentials of victim users. Upon execution, the sample analyzed for this post immediately initiated an HTTP request to a domain "warfacebest.ru.swtest.ru" for command and control. Below is an excerpt of the network traffic generated by this Zeus sample. The red highlighted text represents traffic from the infected host, while the blue highlighted text is an excerpt of the response. The response includes an encrypted configuration file that provides further direction for malicious activity, and this file can be updated at the attacker's discretion.
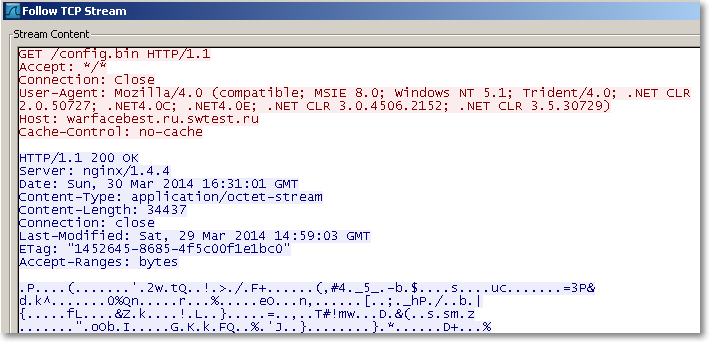
Command and Control channels can vary widely in their complexity. The control infrastructure can range from simple HTTP requests to a malicious domain to more complicated approaches involving the use of resilient peer-to-peer technologies that lack a centralized server and are consequently harder to dismantle. Even with HTTP C2, attackers may take advantage of popular web destinations like social networking sites to increase anonymity and reduce the costs associated with a persistent C2 infrastructure. While not yet common, there are documented cases of malware using services like Twitter, Facebook, and Google Docs to facilitate command and control.
Applying C2 Findings to Incident Response
By using the results of malware analysis to hone detection capabilities, an organization can begin remediating a malware incident. Any identified C2 channels serve as helpful indicators of compromise (IOCs) that can be used to detect other instances of the same or similar malware. IOCs related to C2 include domain names, IP addresses, protocols, and even patterns of bytes seen in network communications, which could represent commands or encoded data.
In the Zeus example mentioned above, the host "warfacebest.ru.swtest.ru" could be configured via IDS to alert on any traffic to that destination. Of course, the C2 servers could vary by sample and may be updated using the configuration file, but creating a signature like this could still be powerful in the context of a specific incident. With a thorough understanding of the C2 infrastructure and protocol, network owners might even consider taking control of infected machines as part of a takedown (law enforcement and other high tech companies have done this on occasion). Also, diligent documentation of C2 findings can help generate invaluable threat intelligence to correlate attacks and better understand threat actors targeting an organization.
If you would like to learn more about dissecting malware to discover C2, I encourage you to join me at an upcoming FOR610 course.
-Anuj Soni
Anuj Soni teaches FOR610 Reverse-Engineering Malware for the SANS Institute. He is also a Senior Incident Responder at Booz Allen Hamilton, where he focuses on hunting threats and double-clicking malware all day long. You can find him on twitter at @asoni.





