Recently I've updated to OS X Lion (10.7) and started testing my incident response scripts on the system. I started looking through new default folders created for users and ran across a folder called "Saved Application State." I began researching this folder and determined that it's used to store settings for a new feature called Users Interface Preservation.
According to Apple, this "saves the state of your application's windows and restores them during subsequent launches of your application." By default this is turned on in Lion, but you can permanently disable it by going to system preferences -> general and uncheck "Restore when quitting and re-opening apps." According to this article , there are several other ways to prevent saving the information. This includes using option+command+Q each time you quit the application.
Overview of Files
When you start Word 2011, it creates the initial folder located under the current user's home directory in /Library/Saved Application State/.
#ls /Users/webb/Library/Saved Application State drwx------ 7 webb staff 238 Sep 15 15:25 com.microsoft.Word.savedState ...(Truncated)....
The content under each folder varies but generally you will have at least one data.data and a windows.plist file for every application.
#ls -al ./com.microsoft.Word.savedState drwx------ 7 webb staff 238 Sep 15 15:25 . drwx------@ 28 webb staff 952 Sep 15 16:43 .. -rw------- 1 webb staff 109280 Sep 15 16:24 data.data -rw-------@ 1 webb staff 6240 Sep 12 14:01 window_1.data -rw-------@ 1 webb staff 116496 Sep 15 15:25 window_38.data -rw-------@ 1 webb staff 124720 Sep 14 10:47 window_8.data -rw-r--r-- 1 webb staff 580 Sep 15 16:24 windows.plist
MAC Time analysis
To gain a better understanding of what we can glean from the saved application state, I deleted the com.microsoft.Word.savedState folder and then started Word 2011.
The directory created time tells us the first time the application was used. Each time you start the application, the file system updates all time stamps for the directory. Macrobber will not give you the original folder creation date. You can look at the meta-data for the folder in finder or use the command line tool stat. This tool shows you file MAC times plus the original creation date, which is the last column in double quotes (e.g. Sep 16 11:40:11 2011).
#stat com.microsoft.Word.savedState
234881028 1348049 drwx—— 6 webb staff 0 204 "Sep 16 13:26:51 2011" "Sep 16 12:56:51 2011" "Sep 16 12:56:51 2011" "Sep 16 11:40:11 2011" 4096 0 0 com.microsoft.Word.savedState
If the window_ .date file has a different modify time then the windows.plist., the window_.data is the last time the user started the application. The windows.plist modified time is when the user closed the application.
In the example below Word was started at 12:56 and was closed at 14:51.
drwx------ 6 webb staff 204 Sep 16 12:56 . drwx------@ 31 webb staff 1054 Sep 16 14:41 .. -rw------- 1 webb staff 9216 Sep 16 14:48 data.data -rw-------@ 1 webb staff 6240<strong> Sep 16 12:56 window_1.data</strong> -rw-------@ 1 webb staff 112976 Sep 16 12:56 window_2.data -rw-r--r-- 1 webb staff 454 <strong>Sep 16 14:51 windows.plist</strong>
When you start Word back up, it will update all the files in the folder to be the same.
Fri Sep 16 2011 14:51:38 204 m.c. drwx------ 502 20 0 /Users/webb/.../com.microsoft.Word.savedState
3584 mac. -rw------- 502 20 0 /Users/webb/.../com.microsoft.Word.savedState/data.data
6240 mac. -rw------- 502 20 0 /Users/webb/.../com.microsoft.Word.savedState/window_1.data
112976 mac. -rw------- 502 20 0 /Users/webb/.../com.microsoft.Word.savedState/window_2.data
454 mac. -rw-r--r-- 502 20 0 /Users/webb/.../com.microsoft.Word.savedState/windows.plist
Fri Sep 16 2011 14:51:39 204 .a.. drwx------ 502 20 0 /Users/webb/.../com.microsoft.Word.savedState
Plist analysis
To use the GUI Plist viewer, right click on the windows.plist and select open. If you want to analyze the plist from the console, you will need to use plutil to convert the binary plist to xml format. The perl library Mac::PropertyList generates an error when trying to parse the file, so plutil is the best command line option right now.
The command below takes the windows.plist and creates a new plist in XML format named /tmp/plist. Then you can look at it using any command line text utility you want.
#plutil -convert xml1 -o /tmp/plist ./com.apple.Terminal.savedState/windows.plist
Word 2011 windows.plist
The NStitle, name, and NSRepresentedURL attributes seems to be the most useful until we have a better understanding of the file.
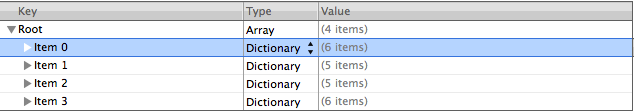
There are four different elements within this file. As you expand it, you will see attributes for the file.
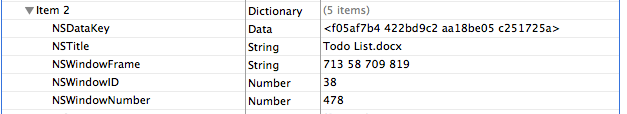
NSTitle includes the name of the Word document I was editing(Todo List.docx) when the application was closed.
Additional Plist Examples
The terminal windows.plist may show you the last file path the user was working under NSRepresentedURL.
Or it may show you the last ssh connection the user had
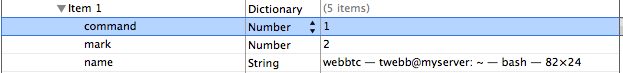
Below is the text version of the out put showing the portion of the Outlook 2011 window.plist. NSTitle show the subjects of an email that were open when the application was closed.
key>NSTitle < /keystring> Mandiant MIRcon Conference - Hotel room block offer ends Monday, Sept. 19 - Inbox < /string
Data File analysis
You may be able to determine what is in the .data files if you use some Cocoa code for creating archives. I took a quick look at this, but I'm not familiar with the language. Hopefully I'll get a little time to play with this, but it looks like a fun project if someone from the community would like to pick it up.
Wrapping it up
Information you can get from the saved application state can be very helpful in certain instances.
- You can tell the first time the application was run based on the original create date of the specific folder.
- You can tell the last time the application was run and how long it was open.
- In certain cases, you can tell what file they had open. This can be very useful if the file is located on portable media
—
Tom Webb has over 11 years of experience in IT Administration and Security. He is currently employed as an Information Security Architect where his primary roles include: system design, lead incident handler and forensic investigations. He holds various certifications including: GCIH,GCFA,GCIA and GREM.





