Ever need to get hold of a set of trusted tools to check processes on a live windows host and just don't have a disk with these on you?
Well, the answer is at hand. SysInternals have a "live site. On this site, they provide a simple list of all of their tools ready for a direct downloads where-ever you are (as long as you have Internet access of course). As the site states:
Sysinternals Live is a service that enables you to execute Sysinternals tools directly from the Web without hunting for and manually downloading them. Simply enter a tool's Sysinternals Live path into Windows Explorer or a command prompt as http://live.sysinternals.com/<toolname> or \live.sysinternals.com\tools\<toolname>.
One of these tools is pslist.
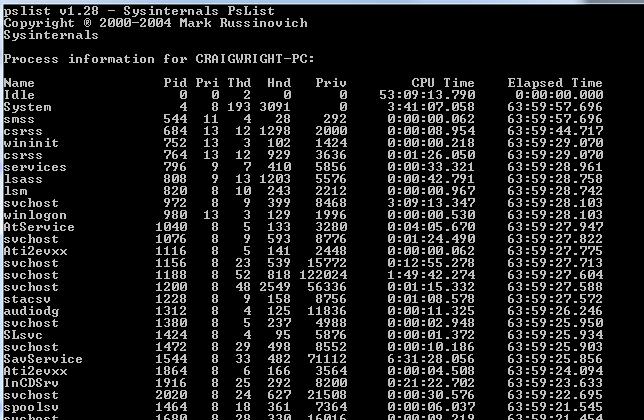
Pslist displays process, CPU and memory information or thread statistics for all processes that are presently running on the system. The information listed for each process includes the time the process has executed, the amount of time the process has executed in kernel and user modes, and the amount of physical memory that the OS has assigned the process. Command-line switches allow the viewing of memory-oriented process information, thread statistics, or all three types of data.
Syntax
pslist [-?] [-d] [-m] [-x][-t][-s [n] [-r n]][\computer [-u username] [-p password]] [name | pid]
Some common parameters
· -d Shows statistics for all active threads on the system, grouping threads with their owning process.
· -m Shows memory-oriented information for each process, rather than the default of CPU oriented information.
· -x Shows CPU, memory, and thread information for each of the processes specified.
· -t Shows the tree of processes.
This tool (and many others) can be downloaded from http://live.sysinternals.com/.
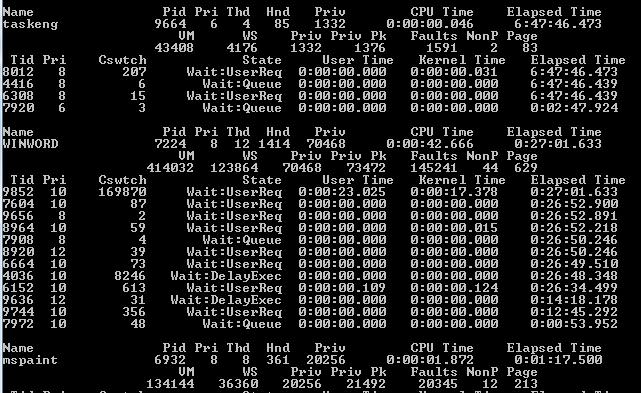
In its standard mode, this tool is similar to the UNIX ?ps' command. When run with a combination of the parameters, it can become a powerful tool that can greatly aid in locating malware on live systems. The ?-x' parameter groups processes with the information concerning the process allowing for a far more granular look at what is occurring on the system (as is displayed below).
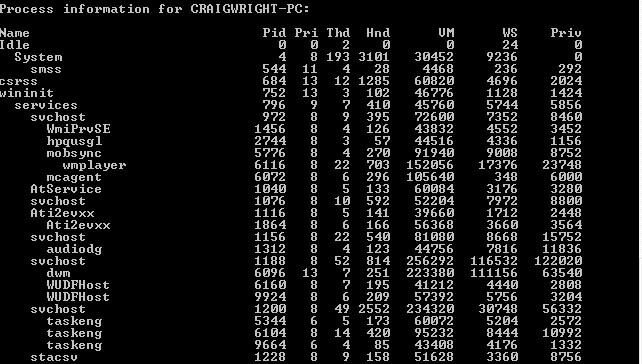
The ?-t' or tree option on the other hand displays the process hierarchy and the dependencies.
Best of all, these tools can now be run directly from the web.
Craig Wright is a Director with Information Defense in Australia. He holds both the GSE-Malware and GSE-Compliance certifications from GIAC. He is a perpetual student with numerous post graduate degrees including an LLM specializing in international commercial law and ecommerce law as well as working on his 4th IT focused Masters degree (Masters in System Development) from Charles Stuart University where he is helping to launch a Masters degree in digital forensics. He is engaged in his second doctorate, a PhD on the quantification of information system risk at CSU.




