Due to my supervisor's reluctance to purchase more drive space (now it's a financial crisis), I recently embarked on a quest to put my disk images on a diet by switching from RAW to compressed AFF images. Arguably, I should have done this moons ago, but as I recently discovered, some things are easier with RAW images.
One obstacle appeared when I wanted to carve out a partition from a full disk image. My image file (P0wnedDisk.AFF) contained a Dell Utility partition and a Windows boot partition. For this case, I was only interested in the Windows partition, so I wanted to carve it out and save it to a separate compressed AFF file (P0wnedPartition.AFF). Unless I've missed something (it turns out, I had... read on), there's no way to do this with AFF Tools alone.
After many listserv posts, cries for help, and prayers to divine entities, I cobbled together the following solution from the numerous tips I received:
Create a mount point and mount the disk image using affuse:
# mkdir /mnt/p0wned # affuse P0wnedDisk.AFF /mnt/p0wned
Now that the AFF image is mounted, we have access to the RAW image file contained within. So we run mmls against the RAW image file to gather the partition information we need.
# ls /mnt/p0wned # mmls /mnt/p0wned/P0wnedDisk.aff.raw
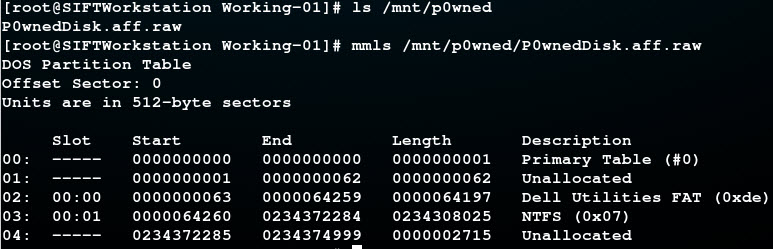
We see the Windows partition listed and are now armed with the information we need, to create our compressed partition image.
03: 00:01 0000064260 0234372284 0234308025 NTFS (0x07)
Next, we prepare aimage to receive the partition of interest by listening on a network port of our choice, and store it in the compressed AFF file P0wnedPartition.AFF.
# aimage listen:9999 -outfile=P0wnedPartition.aff
Now, we open another terminal window and use dd to pipe the raw image data through netcat to the port where aimage is listening:
# dd if=/mnt/p0wned/P0wnedDisk.aff.raw bs=512 skip=64260 count=234308025 | nc localhost 9999
When everything is running successfully, we see the following aimage output in the first terminal window, as the image is being received and written.
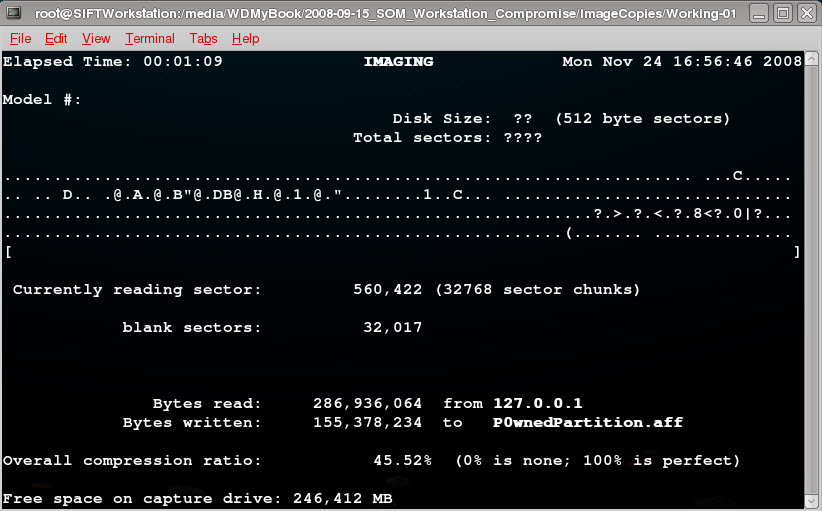
When all is done, you have a compressed AFF partition image extracted from a compressed AFF disk image, having never dirtied your storage with RAW images. Brilliant!
But wait! There's more! Shortly after drafting the first version of this post (everything above), I received new insight from the great and powerful listserv. An astute observer1 brought the "-" parameter to my attention. This parameter is short-hand that tells aimage to take its input from standard in (/dev/stdin). This option, which I initially overlooked, allows us to pipe input from dd directly to aimage as follows:
# dd if=/mnt/p0wned/P0wnedDisk.AFF.raw bs=512 skip=64260 count=234308025 | \ aimage - -outfile=P0wnedPartition.aff
Since we now have a single command line to execute in a single terminal window, this latter solution is clearly the more elegant if you're working with images on a stand-alone forensic workstation. But, in some ways, I'm disappointed. It's always fun to find another excuse to use netcat. And if you have any reason to send disk images across a network connection, the aimage "listen:" parameter is undeniably cool.
———————-
1. I attempted to contact this generous soul via email for permission to cite him publicly, but my query may have been lost to the great spam filter, as I haven't received a response.
Gregory Pendergast, GCFA #3639, is an information security analyst at Virginia Commonwealth University.




