Scammers, intruders and other miscreants often aim to conceal their actions from forensic investigators. When analyzing an IT support scam, I interacted with the person posing as the help desk technician. He brought up a web page on my lab system to present payment form, so I'd supply my contact and credit card details. He did this in a surprising manner, designed to conceal the destination URL.
You can see the scammer bringing up the web page by watching this 17-second video of his actions. Rather than bringing up the web browser, the person launched the HTML Help application, which is built into Windows, by typing:
hh h
According to Microsoft, HTML help is "the standard help system for the Windows platform. Authors can use HTML Help to create online help for a software application or to create content for a multimedia title or Web site." To bring up the interface captured in the above video, it's sufficient to launch the application using the "hh" command and supply any string as a parameter.
Why would the miscreant launch this application? The goal is to use the "Jump to URL..." feature, which is available by clicking in the top left corner of the application:
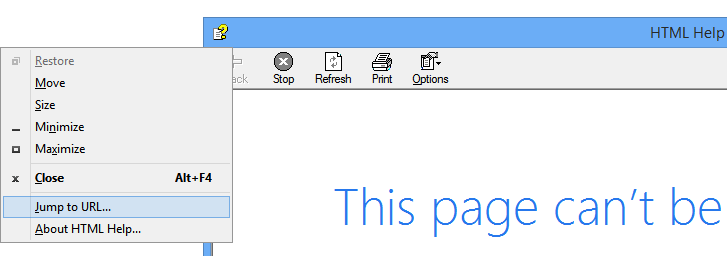
The "tech support" rep then pasted the desired URL from the clipboard into the Windows that popped up. Since the input field of the Window was relatively small, I (posing as the victim) could not see the full URL.
The web page rendered within the HTML Help window, the way it would show up within a browser, though there was no URL bar to display the address of the page:
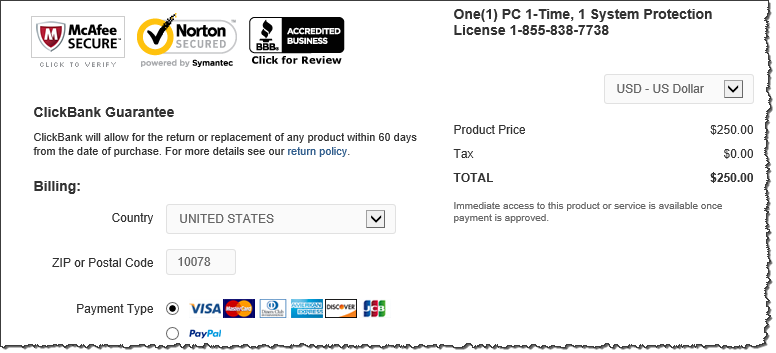
Examining the system after this incident, I could not find a reference to the ClickBank URL in the Internet Explorer history. I used ESEDatabaseView to examine the system's WebCache file; the tool found a cookie set by ClickBank, but showed no relevant URLs. I also used Redline to pull out browser artifacts from this system using memory forensics; this tool showed some URLs belonging to the clickbank.net domain, but not the address of the initial web page:

I was able to locate the URL by extracting all strings from the system's memory image that included "clickbank" in them. The same URL was also left by the adversary on the system's clipboard.
Based on this analysis, it appears the adversary used an unusual method of visiting the website from the victim's system to conceal the URL from the person's view and to make it hard for an investigator to locate the URL in the browser history. This is the first time I've seen such an approach, and wanted to share it with the community. If you've encountered similar techniques or would like to share your perspective on this situation, please leave a comment.
To learn more about this incident, take a look at my Conversation With a Tech Support Scammer article.
Lenny Zeltser teaches malware analysis at SANS Institute. He is active on Twitter and writes a security blog.





