Some have called us log monkeys and claim our work is boring. Others recognize that what we do is a form of hunting. Computer Incident Response Team members watch security information event monitors (SIEMs) for indicators of compromise (IOCs). IOCs are like lycanthropes, they may be IDS/IPS alerts or blocks, or a system trying to connect to a resource it shouldn't be connecting to, or a user complaining of odd system behavior, or heaven forbid, a call from the Feds in the middle of the night.
Incident handlers may look for secondary IOCs to confirm an incident has occurred so they don't unnecessarily cause alarm or disrupt the organization. In the case of unsophisticated malware these secondary indicators can often be found by taking a quick look at the Windows Registry's run key. In many environments, this can be done remotely via:
reg query \\suspect.system.ip.address\HKLM\Software\Microsoft\Windows\CurrentVersion\Run
What comes back might look something like this:
HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\run
Windows Defender REG_EXPAND_SZ %ProgramFiles%\Windows Defender\MSASCui.exe -hide
RtHDVCpl REG_SZ RAVCpl64.exe
Skytel REG_SZ Skytel.exe
SMSERIAL REG_SZ C:\Program Files\Motorola\SMSERIAL\sm56hlpr.exe
SynTPEnh REG_SZ C:\Program Files\Synaptics\SynTP\SynTPEnh.exe
IgfxTray REG_SZ C:\Windows\system32\igfxtray.exe
HotKeysCmds REG_SZ C:\Windows\system32\hkcmd.exe
Persistence REG_SZ C:\Windows\system32\igfxpers.exe
SunJavaUpdateSched REG_SZ "C:\Program Files\Java\jre6\bin\jusched.exe"
MSSE REG_SZ "c:\Program Files\Microsoft Security Essentials\msseces.exe" -hide -runkey
xRqqzy REG_SZ c:\Windows\sysprot.exe
To an experienced incident responder, that last entry with the random looking name is clearly cause for concern.
Unfortunately, malware authors have moved on to less well known methods of maintaining persistence, many times the incident responder will find nothing in the Registry's run key. Unfortunately there are many places in the Registry that can be used as persistence mechanisms. But I have not seen a good list of Registry keys that could facilitate persistence despite the fact that there is a tool right under our noses that provides such a list.
If you're not familiar with AutoRuns it's a wonderful little utility from Microsoft Sysinternals that you can run on a system to see all the things that start running when your system starts up. Here's a screen shot of it in action on my Vista system:
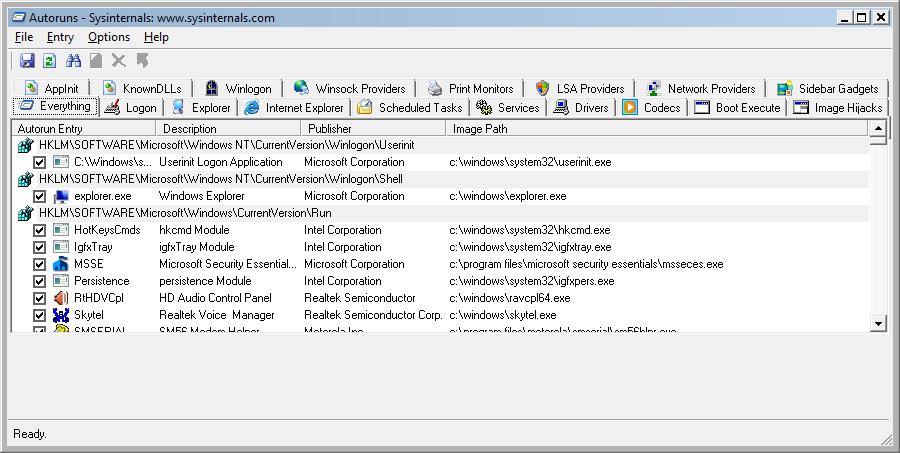
When I ran this on my XP system, I started counting the number of Registry keys (and other places) listed under the "Everything" tab in Autoruns. I stopped counting eventually, but there were around 130. I copied out all of the Registry entries and sorted them into two files, one for HKLM and one for HKCU. The reason for sorting them this way is because I'll be using them with the reg command for scripting and querying remote systems and unfortunately reg is unable to query HKCU on remote systems, which is a drag, but this can be overcome by pulling a shell on remote systems and then running the reg command.
For those who are interested, the two text files can be found here:
XPSP3_HKCU_Startup_Locations.txt
XPSP3_HKLM_Startup_Locations.txt
Over the next few days, I will post similar files for Vista and Windows 7 systems, but as I mentioned previously, the Registry is a complicated beast, there may be other keys that can be used for persistence, but this should be a decent start.
Dave Hull is a member of a Fortune 10K CIRT where he enjoys being the dumbest log monkey in the room. When he's not flinging poo at those outside the cage, he can be found at the command line doing forensics or in the classroom teaching Community events for SANS.




