To view the recap blog for the Cyber Camp which occurred December 29-30 go here.
Hello to all of our Cyber Campers!
We have created this blog to make it easier for the presenters to share notes, links and any content that might be important for you. So check out the blog after each talk if you are interested in accessing this material.
Stream Cyber Camp on YouTube here: SANS Cyber Camp - Day 2
Please note, the recordings of both days of camp will be available in 2 to 3 weeks on the SANS Institute YouTube Channel.
Take a look at the Camp Agenda: downloadable from here.
Also, check out the Challenges we have at the Cyber Start page! Click the picture to learn how to access them!
You can go to https://go.joincyberstart.com to play some free challenges! These are great for beginners. If you want to try the bigger and harder CTF you can head to https://www.tomahawque.com, create an account and then click join event. The event code is new-fork.
For CTF support related questions: refer to this.
Learn from the most trusted source for information security training, certification and research
Here’s a great starting point for cybersecurity training and education from SANS: https://www.sans.org/course/introduction-cyber-security. Even if you don’t take the course, review the info in the syllabus and learn on your own. Also this course: https://www.sans.org/course/security-essentials-bootcamp-style
ANSWERS TO CYBER CAMP GAMES: https://sansorg.egnyte.com/dl/r9eNGFR3E6/
SANS SCHOLARSHIP PROGRAMS: https://www.sans.org/work-study/
FREE RESOURCES: https://www.sans.org/free
Thank you again for attending!
------------------------------------------------------------------------------------------
Tuesday, August 11th
James Lyne & Marilu Duque: Cybersecurity for Good!
James Lyne kicked us off providing amazing ways to show you how you can learn and challenge your self by telling you about these geek challenge links:
For Beginners
- https://go.cyberstart.com/ its a web platform where you can try some of the challenges from easy to hard in a fun way! You will be able to use google to progress!
- Other super fun ways to learn https://www.tomahawque.com/ where you can play and capture the flag, get progress badges and you can play i=until august 13th for free! So GO GO GO and enter the event code: new-fork
If you want to find out about how any awesome jobs you can be doing in cybersecurity, download the 10 coolest jobs poster SANS has available here
.jpg)
Marilu Duque tells you what you can do in cybersecurity to save the world from cybercriminals!
You can:
- Build Infrastructure
- Inform Policymaking
- Solve Complex Challenges
- Find Endless Opportunities
- and save the world!
How to get involved?
Attend conferences. 3 days to a week of learning. You get to learn how people are solving real-world problems and impacting their community.
Through Cyber Security You Can:
Build infrastructure, inform policymaking, solve complex challenges, find endless opportunities, and save the world!!
Cybercriminals are trying to find loopholes every day, so you have to be on your toes at all times to protect against the bad guys.
Roles in Cybersecurity :
A lot! Threat analyst, educators, forensic analyst, cybercrime investigator, etc. Private, public, non-profit sectors Different fields: medical, ICS, Banking, Defense, retail, software, TV, universities, etc. Diverse backgrounds. And everyone is working towards the same mission.
Cybersecurity is a very welcoming field!
What are security practitioners working on now?
Election security, educating protestors, educating Older Generations, security in classrooms, misinformation & privacy activism, finding missing people using OSINT, combat human trafficking & child exploitation, solving crimes.
Older generations who didn’t grow up with cybersecurity knowledge, are definitely being targeted. Therefore, they need to be educated the most.
OSINT = Open Source Intelligence
What can you do now?
- Learn: skills, strengths, ethics, stay updated
- Practice: CTFs, Bug Bounties, Create tools, Online classes.
- Get involved: start a club, connect, attend conferences
- Educate others “Everyone can be educated in cybersecurity, even if they aren’t in the cybersecurity field”
- Ask Questions!!
Important Links suggested by Marilu:
- Opportunities: https://dodstem.us/stem-programs/programs and https://seap.asee.org/
- Organizations to join: https://cybersecurityventures.com/cybersecurity-associations/
- Job stats: https://www.cyberseek.org/heatmap.html?fbclid=IwAR2jX7M_fLi7UUN5L4pmU7g6p-NgH8jamyrj8GFz3n4Y-shab3Ha9yxw17A
- Online CTF's:https://picoctf.com/https://www.hackthebox.eu/https://microcorruption.com/loginhttps://www.tracelabs.org
- How does the bug bounty website work?
Here are some resources to help you answer that question!:
- https://medium.com/inbughunters/getting-started-in-bug-bounty-7052da28445
- https://www.geeksforgeeks.org/how-to-get-started-with-bug-bounty/
- https://github.com/nahamsec/Resources-for-Beginner-Bug-Bounty-Hunters
- Q&A: What is the most fun thing about cybersecurity for Marilu?
- When she is able to bring in data and numbers from a cyber attack. She is into creating actionable data!
- Q&A: where to find internships: simply google internships! There are a lot of remote internships going on in today’s climate.
- Q&A: Big tip for applying to schools?
- Q&A: Is there a place I can find a list of internships you'd recommend?
- Connect with Marilu!
- Socials: @STEMLatina
- LinkedIn: /in/mariluduque/
- Email: STEMLatina@gmail.com
To view the full talk:
----------------------------------------------------------------------------------
1:30pm - Thinking Like a Forensic Examiner - Lodrina Cherne @hexplates
Lodrina, a forensic examiner by heart explained how your phones and computer track whatever you do and yes! forensics can get that information out of your devices, even if you delete things. Forensic Analysts can extract that information with special tools and by applying their training.
For example, your cell phone!
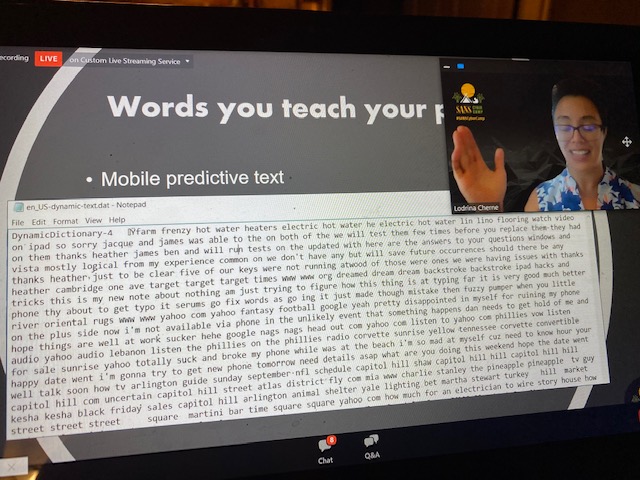
Cell phones remember some information we usually type to make our life easier. It can store our location, conversations, so think like a forensic examiner. Do you think you could get that information from your phone?
How about the predictive text? Does it make your life easier too? Your phone can remember important words and names you type. What other examples can you think about?
And those apps! When you switch between them your phone knows what was the last app or screen you were on your phone before the switch right?
So this is your mission if you choose to accept it.
.jpg)
Take your phone and put it on Airplane mode, turn off blue tooth and WiFi.
Can you see posts, see your last podcast or pictures on Facebook? How about YouTube videos? That is an indicator forensic examiners can get all that stored information from your phone!
How about on your computer? Can you find DFIR artifacts on your computer?
What can you find? Computers can tell you where you have been on the internet, even sometimes when you use an incognito web browser. When you ask yourself questions like this, you are now thinking as a forensic examiner!
Ready to start in digital forensics?
Check out these resources
To view the full talk, visit here.
----------------------------------------------------------------------
Jason Nickola: Need for Speed Cracking Hashes to Pwn Passwords
Why do we hack? Not to be evil but to make corporations more secure!
Let's think passwords!
.jpg)
Passwords are not supposed to be stored in your computer or cell phone, what these devices do is store a representation of your passwords with secure algorithms.
What is a hash? Not like encryption tools, hashes are not supposed to be encrypted. Hashes are unique to a file or a picture and they serve as a fingerprint of these artifacts. And guess what? Hashes always have the same length algorithm!
In forensics, hashes are very important because they can tell you where to find artifacts and also will let you know if these artifacts have been modified. That allows computer forensics to know if anybody has tampered with important evidence.
Want to see if you can crack some hashes?
Practice! Here is how....
- Download Hashcat
- Bookmark this: https://hashcat.net/wiki/doku.php?id=example_hashes
- Look at examples to crack: https://temp.hashes.org/left.php
- Some wordlists: https://github.com/danielmiessler/SecLists/tree/master/Passwords
- High-value masks:https://blog.korelogic.com/blog/2014/04/04/pathwell_topologies
To view the full talk, visit here.
____________________________________________________
2:30pm - Be Smarter Than the Smartphone (WORKSHOP) - Heather Mahalik @heathermahalik
Can you think of your phone as a crime scene? Heather helped us enter the word of a cellphone to decipher the truth.
Mobile forensics isn’t an easy career. Because there’s SO much information, it makes it hard. Think about the challenges: locked phones, destroyed phones, encryption, cloud data and syncing, applications (so many!), data that hides in locations. Heather worked a phone where someone ATE their SD card. Think about it, the data being stored changes regularly. For example, when you go on a walk, your phone is tracking your steps, and it’s tracking the weather that day. The data changes every single day.
What if these phones are locked? Cracking a password is difficult but possible. Forensic examiners use a variety of ways to get that password from different resources and to crack phones.
.jpg)
Remember, your phone never forgets! So Heather’s job can be made easier due to poor security, social media (easy to stalk people!), and location tracking by your phone. The background information is always running on your phone. Therefore, your phone is always listening, watching, and waiting.
Anything you put out on the internet is not fully safe.
Be SMARTER than your smartphone. How?
Read the permissions when you install. Everything you do on a phone can be recovered. What are your usernames? Make sure whatever it is, that it isn’t offensive. Do not reuse passwords! Encrypt when you can, and protect yourself. Create backups. Share your passwords with your parents, SERIOUSLY! And don’t talk to strangers.
Q&A: What do you do if the phone is locked? Crack the lock or use a jailbreak into bypassing security into getting an extraction of the data. You will need a Mac if it’s an iPhone, and if it’s an android you will need some expensive equipment.
Q&A: What’s the coolest thing you worked on? Osama Bin Laden’s devices.
Q&A: What’s your opinion on using TikTok given the current climate? Heather does not have TikTok on her personal device. She keeps it on a test device because of the security vulnerability.
Q&A: Is it possible to backup anyone else's iPhone if they have a passcode? No. You need the code to establish the “trust” with the device you’re trying to back it up to.
Connect with Heather!
- Email: hmahalik@sans.org
- Twitter: @heathermahalik
- Blog: http://www.smarterforensics.com
As Heather shows how to do phone backups, you can also try back ups here www.FOR585,com/books
To access Heather's homework/lab click here: for585.com/phonelab
To view the full talk, visit here.
-----------------------------------------------------------------------------------
3:30pm - The Hidden Information in Photos - Jason Jordaan @DFS_JASONJ
Think about this.... you see Jason presenting. Now, think of Jason as a file. You don’t know his age, where he lives, but the only information you have is what you see with your own eyes, or hearing him as he talks. If you want to know more about him, you can ask his name, you can go find his birth certificate to find his age, etc.
That information describes aspects of him. So if he is the file/the data, all of the information about him is metadata. It describes the data. ALL FILES have metadata.
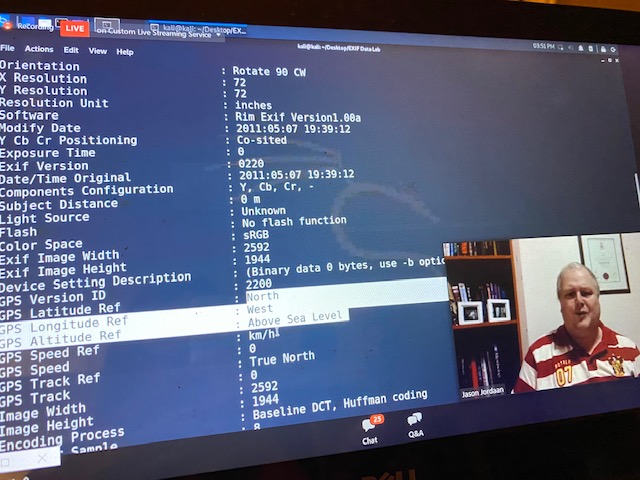
Digital files have their own type of metadata. Which is called EXIF Metadata. For example, when you see a photo, EXIF metadata is not the actual picture being shown, but the data embedded in the file that describes certain aspects of the file. So for example, it will tell you when the picture was taken, and the type of camera used. Most pictures will have geo coordinates or geotags telling you where in the world you actually were when that photo was taken. It can tell you the elevation you were at when the photo was taken, and even what direction you were facing.
Where in the world is Jason? See if you can find the metadata and find where exactly in the word he was when he took this photo!
.jpg)
.jpg)
Q&A: How often do people hide info in metadata? Jason has seen it done in previous anti-terrorism investigations. People were taking photo editing software and embedding info in the metadata.
Q&A: How many investigations have you done? “Oh wow, I have done thousands of investigations.”
Q&A: Can you detect if a photo has been photoshopped? “Sometimes." Beware, metadata can sometimes be changed! But that’s just part of the forensics challenge. There’s a whole field of digital forensics that focuses on photo manipulation.
Connect with Jason! Email: jjordaan@sans.org
To view the full talk, visit here.
________________________________________________
4:00pm - Introduction to Network Analysis (WORKSHOP) - Greg Scheidel @greg_scheidel
Here’s a copy to his slide deck! https://bit.ly/31xiYnC
What is Packet Capture and analysis?
.jpg)
It’s intercepting network communications, decoding it, and interpreting it.
Examples:
- Web client (e.g., browser) <-> web server
- Web application <-> database
- DNS Client <-> DNS Server
- Client (e.g., workstation) <-> file or print server
Why should you care about this? If you end up working in IT, IT Operations, or Info security, you’ll need a basic understanding of how communication works between hosts. If you can do that analysis and really know what the communication means in your network, you’ll be leaps and bounds beyond people who think this all happens because of “magic”. You’ll have an edge, and it’s COOL!
How do you intercept the data? If you are on a wired network (ex. ethernet) and two hosts communicate on other sides of the room, there is a cable connecting the two, you can put a tap on there. This means if you have control of that tap, the information will flow through it, and you can grab a copy of that information. Other ways to do it is using network switch mirror ports, tricking hosts or network gear into sending traffic, wireless monitoring, and local host intercept.
Greg recommends using core tools: tcpdump, wireshark, and tshark
Tcpdump is lightweight, easy to use, and does basic filtering. You especially want to be familiar with this tool because you’ll see it all over the place!
Q&A: where are you pulling these commands from? Do you remember them? A lot comes from experience, but there's no way to remember every command.
Q&A: How would you go about capturing wireless traffic? You need to have an interface and software understanding the information being fed to it. The aircrack suite and kismet set of tools are recommended.
Connect with Greg! Twitter: @greg_scheidel
To view the full talk, visit here.
------------------------------------------------------------------------------------------
Wednesday, August 12th
1:00pm - A Teenagers Perspective on Helping Your Parents Help You - Lance Spitzner & Alex Spitzner
From Lance’s perspective as a parent, he talks about the top 3 threats kids face. 1) Strangers, 2) Friends, and 3) Themselves. The most thought of threat of course, is strangers. And while this is an active threat, we cannot underestimate the other two threats. We may not think of Friends and Family as a threat, but cyber bullying is one of the most difficult threats to handle (and it’s very common!). It’s very public and it can be done by someone anonymous. Don’t let this get out of hand, talk to your parents!
The third threat is surprisingly kids themselves. Kids can be their own worst enemy, which is why parents setting expectations and rules is so important. You don’t want to be the bully. You don’t want to share inappropriate content. Try not to spend too much time online.
Keep in mind, you are growing up in an environment that your parents never experienced as kids, which sometimes leads to your parents being overwhelmed. So what can you do to help? Talk to your parents! Let them know what technology you’re using and let them know what you’re using to communicate with others.
The ultimate goal: help your parents help YOU.
Now from Lance’s son, Alex, his perspective on dealing with parents is that trust is key to being safe. Having too much or too little trust with your parents can be harmful. He knows everyone has a different relationship with their parents, but communication with them is so important.
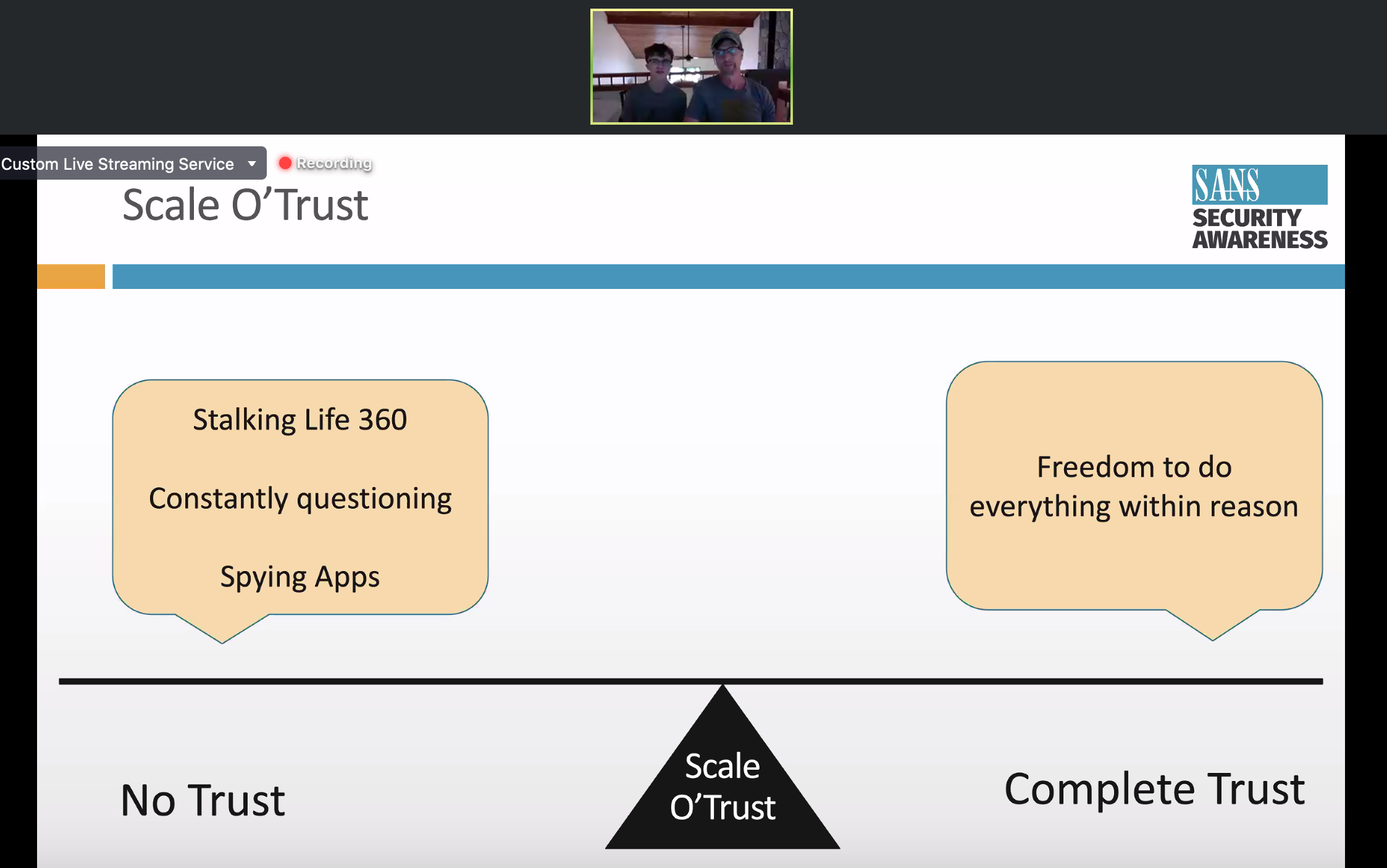
So why is it so hard for parents to understand something as simple as Snapchat for instance? They just don’t understand modern technology! Helping them understand will help you in the long run. So talk and get them involved, but don’t expect perfection right away.
Are you wanting to get more involved in cyber and technology? Alex suggests getting into robotics! You can do programming, coding, hacking, and designing the robot! Here’s a resource for you to check it out: https://www.firstinspires.org/ and check out @team3061 on Instagram, Twitter and YouTube.
Connect with Lance!
- Twitter: @lancespitzner
- Email: lspitzner@sans.org
Live Q&A: Some kids feel like they can’t talk to their parents, what should they do? According to Alex, if you’re around 14 or 15, you have got to have some sort of common interest. His friend with the burner phone has strict parents, but they could bond over trucks. So if you can find that common interest with your parents, that’s the best way to start a conversation saying you don’t like certain things. It might be awkward, but you can start exploring together.
To view the full talk:
-----------------------------------------------------------------------------------
1:30pm - Introduction to Metasploit - Jeff McJunkin
Jeff talks about what real world hacks look like and talks about metasploit. Metasploit is a free open source meant for everyone. He also shares some hacking terminology:
- Password Guessing: attempting to log in to a system that validates the login (usually with a username and password). Account lockout is always a concern. “Online” attack.
- Examples: logging into gmail.com Logging into macOS, Linux
- Password Cracking: after compromising something built using a password (a “hash”) attackers on their own hardware can take unlimited guesses. “Offline” attack.
- Examples: WordPress user hashes
- Password Spraying: Specialized type of password guessing. Taking one (or a few) guesses per username, over lots of usernames, in order to minimize risk of account lockout.
- Credential Stuffing: password spraying, but re-using previously breached credentials
The more you know: MITRE’s terminology really standardized the world wide terminology we use when it comes to hacking.
So what does hacking look like start to finish? From start to finish, there are 4 things hackers need!
- Internal access (public websites have less stuff to hack than internal systems do)
- Privileges (not everyone can tweet as Elon Musk or read CreditCards.xlsx)
- Finding the valuable data (because there is no internal Google)
- Copying and stealing that valuable data (or deploying ransomware)
Jeff shared a “hypothetical” (maybe not so hypothetical...) example of hacking Twitter.
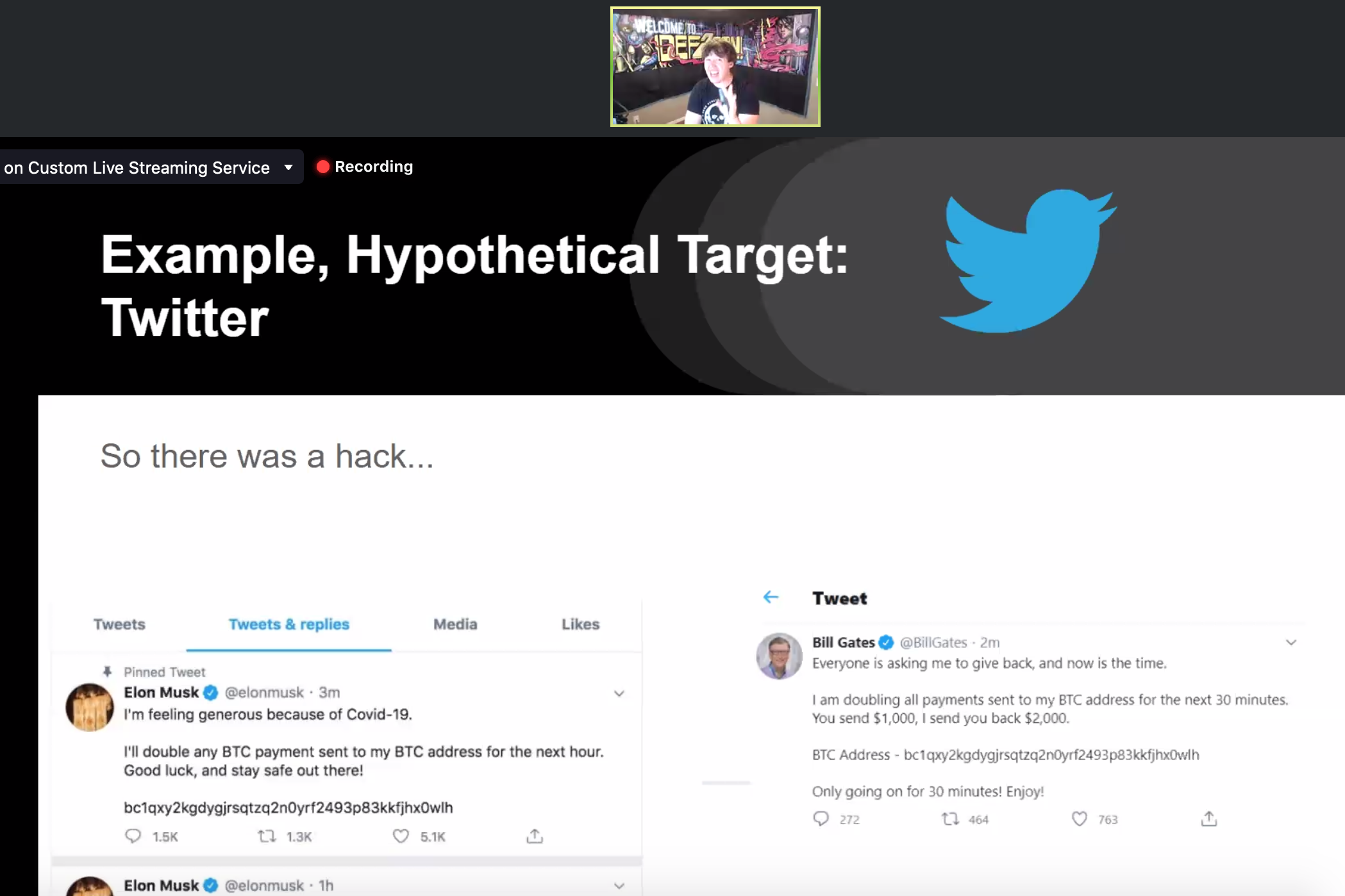
Jeff goes on to share Tim MalcomVetter’s hacking types:
- Hacking from the outside
- VPN/logging in from the outside
- Phishing
- Walking in
- Tricking them to accepting your stuff
The most common hacks are the first 3 in this list: hacking from the outside, VPN/logging in from the outside and phishing.
So what’s phishing? It’s a type of social engineering: “any act that influences a person to take an action that may or may not be in their best interest.”
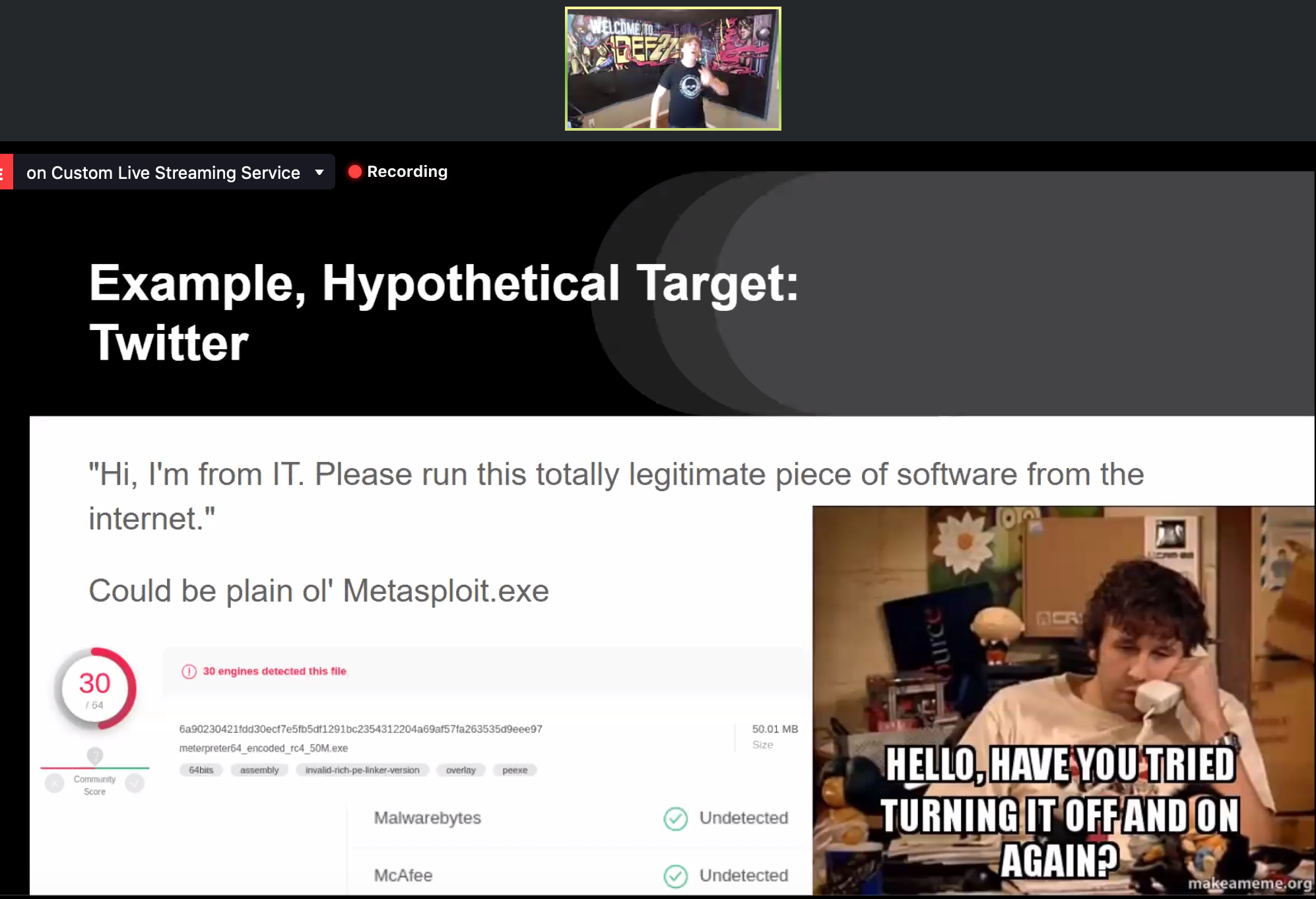
Using metasploit, you can use the network access (Twitter HQ wifi or whatever) through:
- A PHP meterpreter on a web server on the external DMZ and pivot to compromise an…,
- Internal windows server, then pivot on the internal network and compromise a…
- Restricted macOS system and use that to attack internal systems.
Live Q&A: What’s Biggest misconception of hackers? It’s that hacks are very complicated. Remember Twitter was allegedly hacked by a 17 year old, and they just simply asked someone nicely for admin rights. So the biggest misconception is that it’s always complicated.
Suggested resources:
- https://github.com/iagox86/dns...
- https://www.digitalocean.com/
- https://www.vulnhub.com
- http://www.cis.syr.edu/~wedu/seed/all_labs.html)
Connect with Jeff!
- Twitter: @jeffmcjunkin
- Email: jeff@roguevalleyinfosec.com
To view the full talk, visit here.
-----------------------------------------------------------------------------------
2:30pm - Intro to Web Applications: What the Heck is a Web App? - Chris Elgee
Anything you deal with on the internet is a web application. Something as simple as a web page such as kittenwar.com. This is an example of a web app. This website is straight HTTP. It’s not secure in any way, but it’s a good website to observe. When we get a page from a web server, it comes to us as code. Try this: Right click on the webpage, click “view page source” and you can see the code coming in behind it. You’ll see HTML code, some java script code, CSS (cascading style sheets). So be aware that’s going on behind the scenes of your basic webpage.
Did you know? Those who have permission to hack = white hats
Chris talks about the The Holiday Hack Trail (similarly based on the Oregon Trail… anyone remember that??). This Holiday Hack Trail was built in a web browser. You, yes you, have permission to try and hack this! Hint: Hit F12 or control + shift + I to get the developer console. It’s for people developing web pages to figure out how things look and to test out web app purposes.
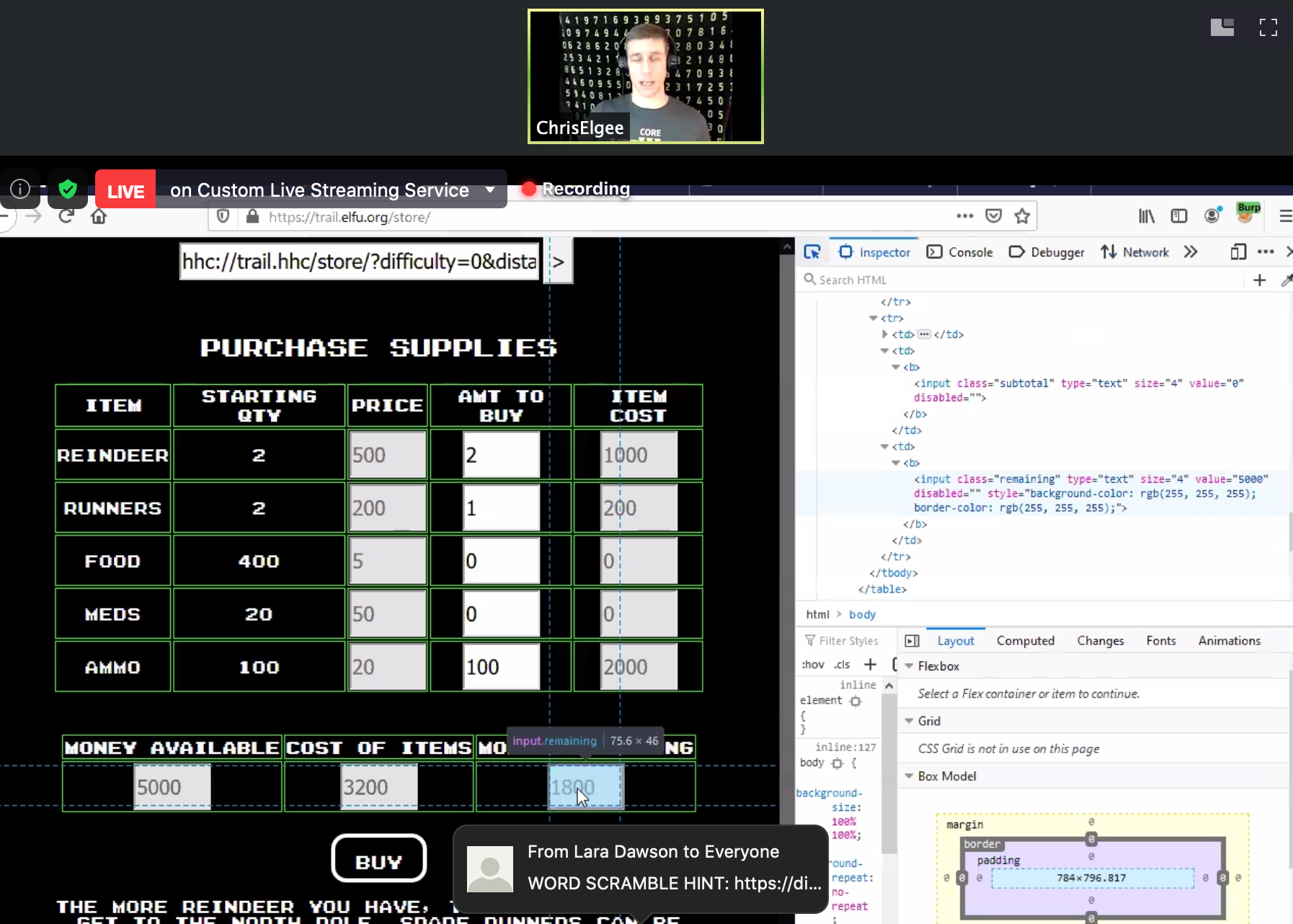
When it comes to hacking and pen testing -- the developer and pen tester (ethical hacker) work together. The pen tester will poke around what they built and find any flaws and let them know. Chris went on to show this live on his screen, poking around The Holiday Hack Trail.
If you play any of the challenges, go look through the past winning entries here: https://holidayhackchallenge.com/past-challenges/
References:
- www.Kittenwar.com
- Holiday Hack Trail: https://trail.elfu.org/
- More challenges: https://www.counterhack.com/h2matrix
Live Q&A: How do you get permission to tinker with URLs or sites? You get written permission from someone. You have contracts and lawyers involved. Find some free CTF sites like www.overthewire.org
Connect with Chris!
- Twitter: @chriselgee
To view the full talk, visit here.
-----------------------------------------------------------------------------------
3:00pm - Cyber Security Awareness or Online Safety - Courtney H. Jackson
Courtney is a cyber security business owner with over 20 years of IT and cyber experience. She is a military veteran and received her Master’s Degree in Information Security and Assurance. Currently, she serves on the Executive Boards for USF Cybersecurity Education and Women in Technology.
So what in the world is cyber security? By definition, it’s "a body of technologies, processes, and practices designed to protect networks, devices, programs, and data from attack, damage, or unauthorized access."
When surfing the web, Courtney emphasizes some things you should do:
- Make sure “HTTPS” is enabled on website that you enter your information
- Use Virtual Private Network (VPN) software when possible
- Communicate with your friends and people you know
- Keep your password and personal info private
- Read all agreements before you click accept
- Surf the web responsibly
Now what shouldn’t you do? Courtney suggests not to:
- Use random wifi spots
- Accept friend requests from strangers
- Post any of your personal info online
- Believe messages, posts, or websites that seem too good to be true
- Use easy to guess passwords
- Open emails from strangers
Courtney also emphasizes that when you post content to the internet, you should make sure the content is appropriate, because nothing is ever truly deleted (once you upload, it’s online forever), and only upload info about yourself; no one else. That picture you post of your friend on the internet might not be a photo of themselves that they want online!
It’s great to have fun on the web, but just remember to always be safe!
Connect with Courtney!
- Corporate HQ: 4809 E. Busch Blvd, Suite 202, Tampa, FL 33617
- Phone: 813-603-7233 (SAFE)
- Websites: www.courtneyhjackson.com (consumer) & www.paragoncybersolutions.com (corporate)
- Socials: @CyberCourtney & @ChooseParagon
Live Q&A: You mention using VPNs... if someone uses it, can they still have their actions tracked on line? It's still possible, it just depends on how sophisticated the hacker is. VPNs just add a layer of protection.
Live Q&A: How successful are the VPNs in being that extra level of protection you need? There are a lot of different vendors that sell VPNs, but nothing is 100%, it's about also putting certain security procedures in place to prevent attacks as well.
Live Q&A: If you receive an email from someone you don't know, is it still okay to open an email from that person you don't know? No, why risk it?
Live Q&A: If you come across someone doing something wrong online, how do you report them? If you see them doing something wrong on social media, most social media platforms have a report button option. If you see something inappropriate online, there are internet safety centers online where you can report someone.
To view the full talk, visit here.
-----------------------------------------------------------------------------------
3:30pm - Introduction to Programming (WORKSHOP) - Mark Baggett
Mark is the owner of Indepth Defense and he is an instructor for SANS. So how do you get started in information security? Well, it starts with an interest that can grow into a passion. Hacking and info security is a field that changes constantly, so it takes a lot of dedication to learn about it!
Every aspect of information security needs programmers.
What is programming? Where do Programmers work? How do they do their job?
Programmers create software. And remember, computers are a combination of software and hardware. Hardware includes such things as laptops, printers, computers, wireless access point, etc. But, hardware doesn’t do anything until you put software on it! Some examples of software include the operating system such as Microsoft Windows, games, web browsers and Microsoft Office. It’s the brains! Software is also the “smart” in your smart phone. Software is how self driving cars know how to drive! Programmers create programs to make it so people can do their jobs easier.
Think of it this way, programmers are like authors of a book. Authors take words, combine them into meaningful sentences, and use those sentences to tell a story. A “programming language” is made of only a few simple commands. Programmers combine those commands and create new commands called “procedures, functions and objects”. They then combine those new commands into a program.
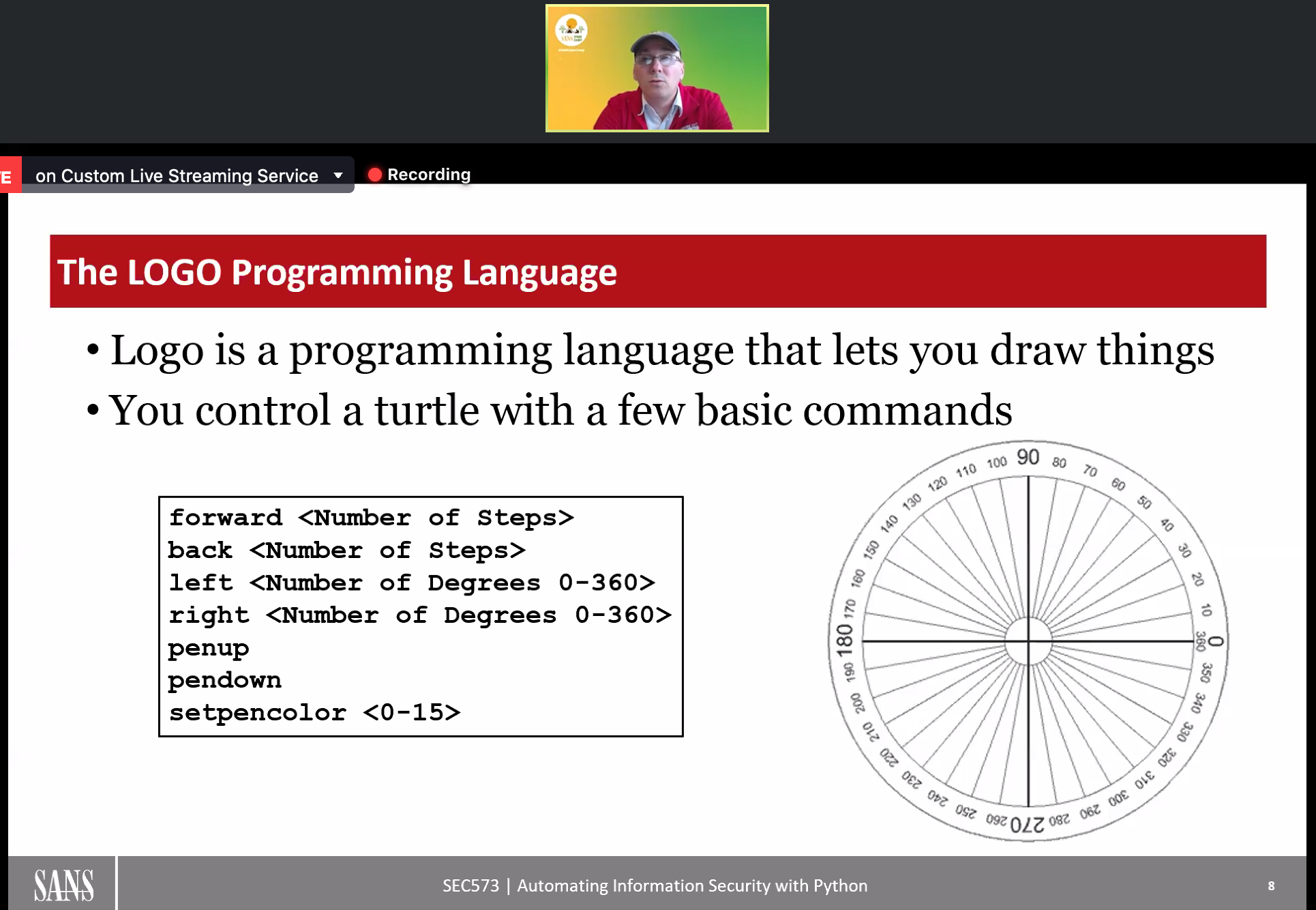
An example of a programming language is LOGO. This is a program that lets you draw things.
Mark shows how to use LOGO, and you can try out LOGO too! So try and make your own shape here: http://www.logointerpreter.com/. If you need assistance, be sure to look at the Common Logo Commands section on the website.
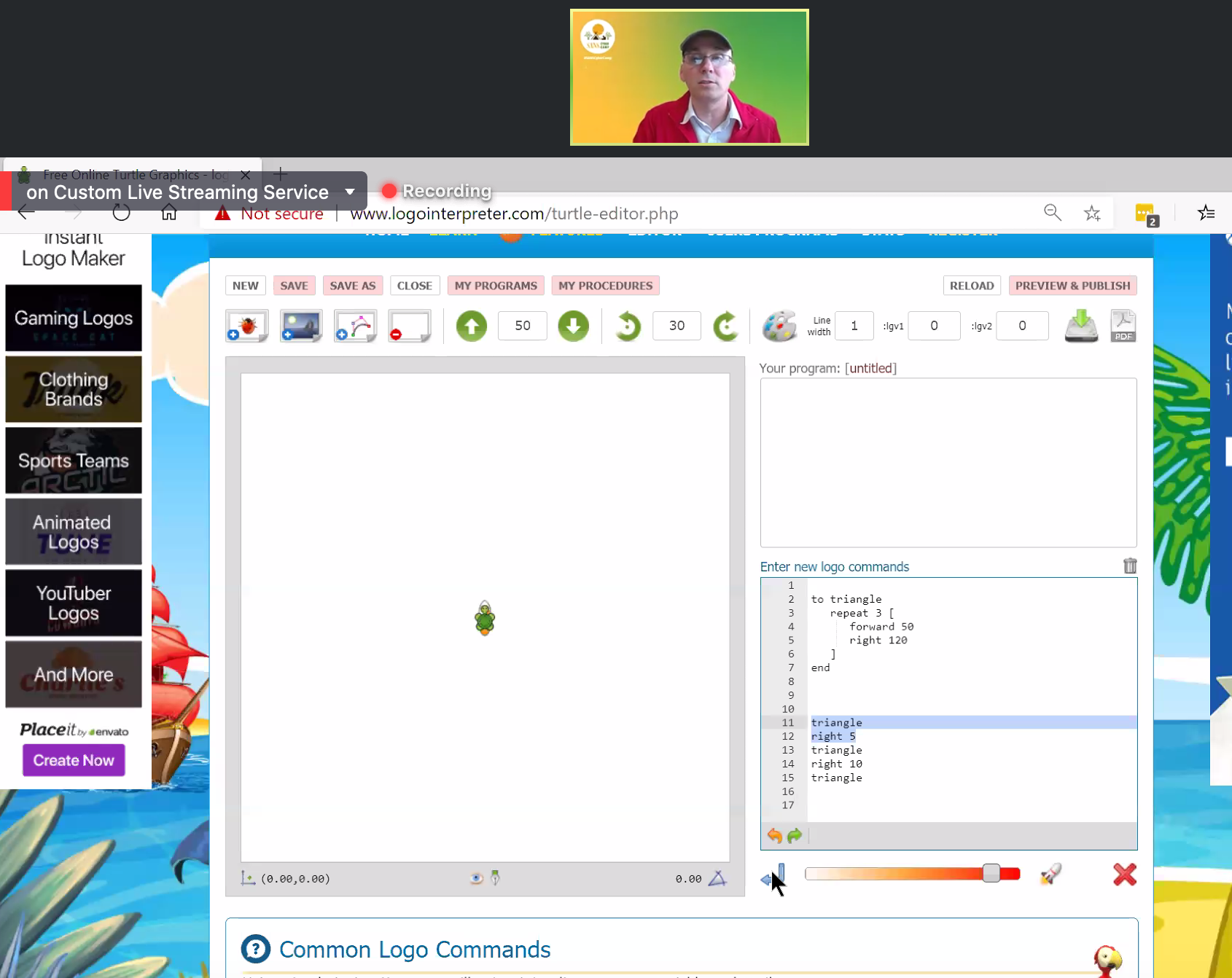
Live Q&A: Do you have to know python to be a good hacker? You really have to know a programming language to be a good hacker, so you need to know some programming. It doesn't have to be python, but python is the easiest language to learn.
Live Q&A: Where's the best place to learn a programming language? Mark's SANS course, of course!! Learn more about it here.
Some resources to learn some coding:
- www.codeacademy.com - Start here first!
- www.codingbat.com/python
- www.checkio.org
Connect with Mark!
- Twitter: @markbaggett
To view the full talk, visit here.