With Memoryze 3.0, the folks at Mandiant hit their mid-summer goal to roll out memory analysis support for Windows 8 (x86 and x64) and Server 2012 (x64). While support has not yet been rolled into Redline collector scripts, data collected by Memoryze can be loaded and analyzed in the Redline interface. This is no real surprise since Memoryze is the back-end collection and analysis tool that Redline relies upon.
MemoryDD.bat -output E:\ Process.bat -input memory.img -handles true -sections true -ports true -imports true -exports true -injected true -strings true
To perform live memory analysis and take advantage of capabilities like digital signature, MD5, and MemD5 checks, run the Process.bat directly on a live system without the "-input" parameter
Process.bat -output E:\ -handles true -sections true -ports true -imports true -exports true -injected true -strings true -digsig true -MD5 true -MemD5 true
If you have used Redline before, these options should look familiar since Redline simply provides a GUI and builds a similar command line in the background.
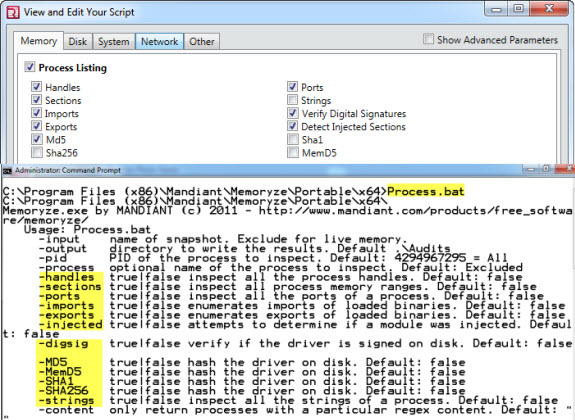
Redline vs. Memoryze Parameters
The results of Process.bat (stored in .\Audit by default) can be opened in Redline using the "From a Collector" option under "Analyze Data". Just point it to the folder with the Process.bat results.
To build the Memoryze collection scripts on a portable device you can use the method covered in the Memoryze user guide (below) or just install MemoryzeSetup.msi on your forensic system and copy the resulting x32 and x64 folders to your device.
msiexec /a MemoryzeSetup.msi /qb TARGETDIR=<path to="" device=""></path>
This entire process evokes some nostalgia, taking us back to the days when Redline was first released. Don't get too comfortable with it as my guess is native support within Redline is only a release away.
In addition to Win8 support, expect a big upgrade in network connection identification including IPv6 support and improved carving of closed network connections resident in memory. Download the update here. Thanks to Jamie Butler (@jamierbutler) for the heads up!
Chad Tilbury, GCFA, has spent over twelve years conducting computer crime investigations ranging from hacking to espionage to multi-million dollar fraud cases. He teaches FOR408 Windows Forensics and FOR508 Advanced Computer Forensic Analysis and Incident Response for the SANS Institute. Find him on Twitter @chadtilbury or at http://forensicmethods.com.




