The preparation of a malware analysis environment can often be a lengthy and repetitive process. I am not referring to setting up a virtual machine which contains all of your tools, but rather recognising that each sample you analyse may have very specific environmental requirements before it is willing to execute fully. For example, it may require a certain number of files to be present in the My Documents directory, or may check for a specific registry key.
If we consider how many analysts around the world were looking at the same major threats in 2016, it seems rather silly for each of them to have to manually setup their environments as required by the sample. One solution may be sharing of VMs, but this comes with issues such as operating system licensing and the shear size of the package to be exchanged, which got me thinking, there's got to be an easier way.
Accordingly, I have been developing an open source tool 'rapid_env' (as in, 'rapid environment') which allows for the instant, template based provisioning of a Windows environment. This can include elements such as files, registry keys, processes and mutex, all of which can alter the way that many of the current threats behave.
[View C++ Source Code]
[Download Binary]
Demonstration of 'rapid_env'
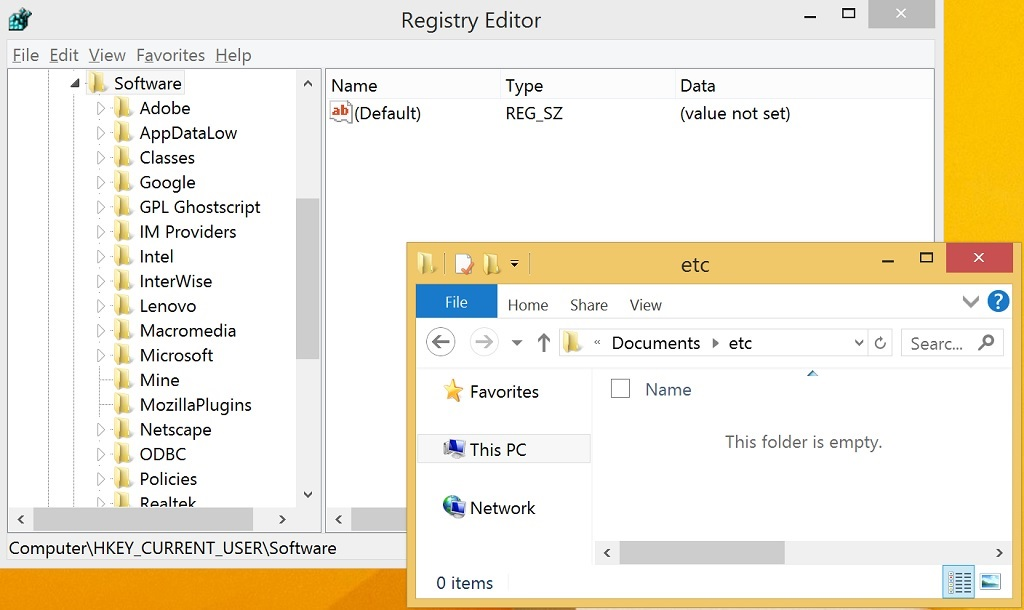
Let's explore the tool in action. At this point we have a clean Windows 8.1 build, which has all of my analysis tools ready to go. In Figure 1 below we can see part of the file system and registry, our interest in these elements will become clearer shortly.
Figure 1 - Clean system
Now let's imagine that we have received a new sample to analyse along with some information on how we need to set our system up to get it to run. This could include the need to create files, registry keys, mutex or launch processes.
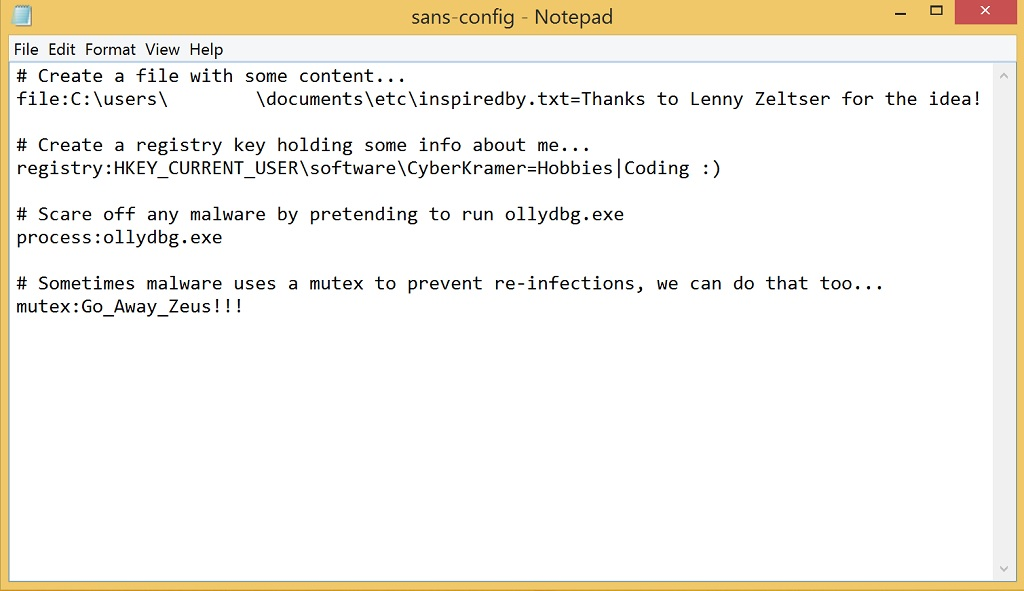
At this point, we need to work out how we need the system to look and prepare a configuration file. The format of this file is pretty basic and sample is shown in Figure 2. This will create a file, registry key, process and mutex (the lines beginning with a # are comments and will be ignored by the parser).
Figure 2 - rapid_env sample configuration file
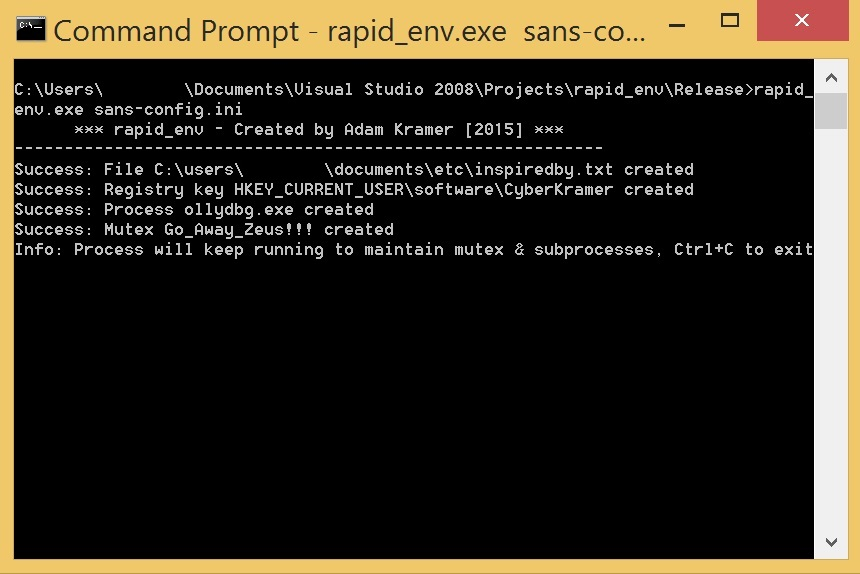
The program is launched by specifying the configuration file to action, and as we can see in Figure 3 below, the user is kept up to date with what changes are being made to the system and whether there was success or failure. In this case everything appears to have gone smoothly and the environment is now ready.
Figure 3 - rapid_env in action
If we go back to the file system and registry which we saw previously in Figure 1, we can see that the file has been created with the specified content and the registry has been modified with the requested value and data.
Figure 4 - System after running rapid_env
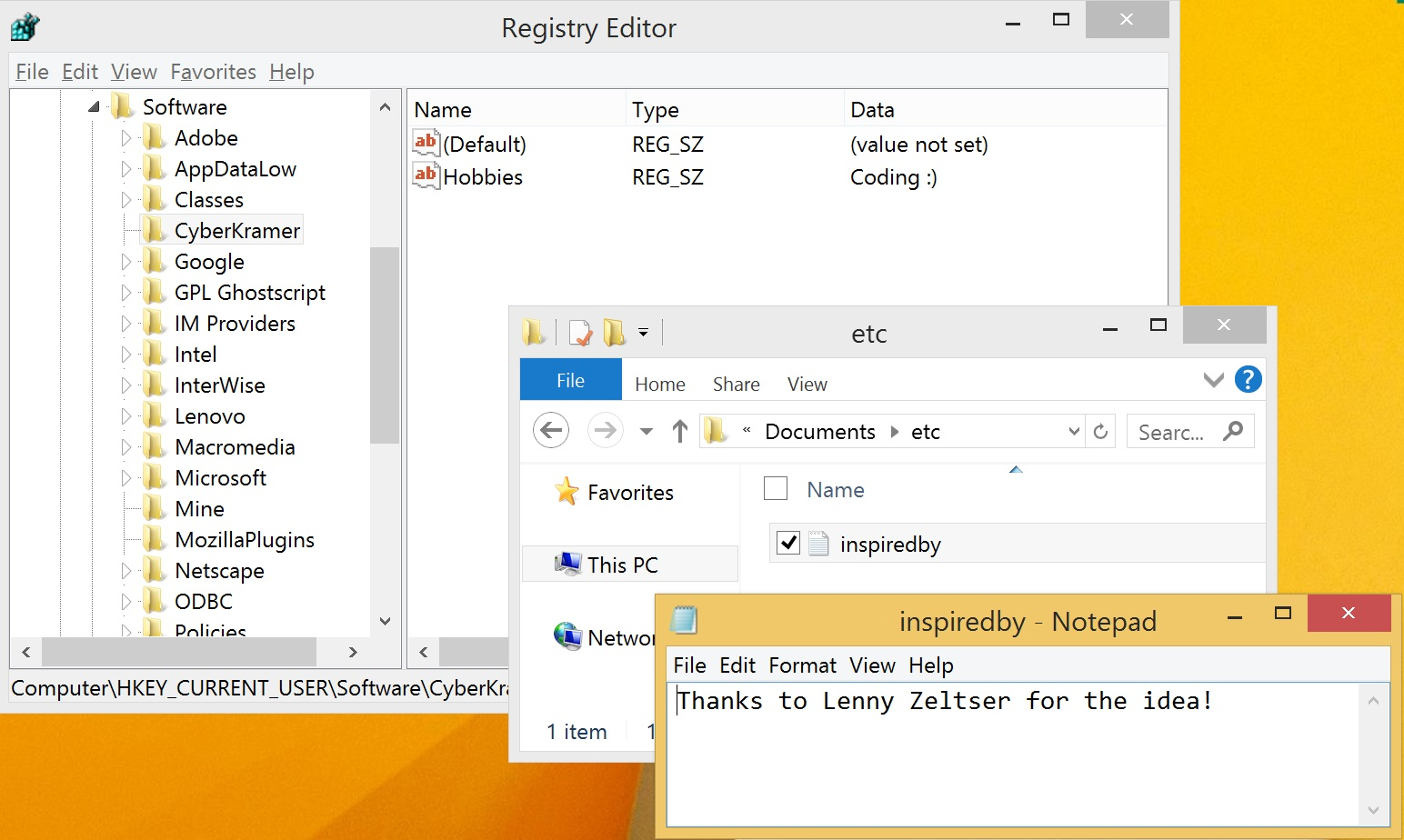
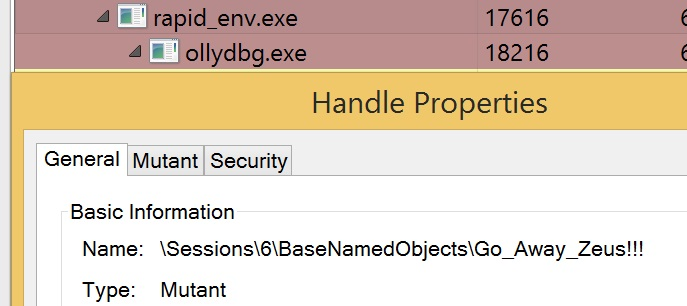
Figure 5 shows the running processes and associated mutex. I've chosen ollydbg.exe in this case which tends to put malware off (as it believes it's being analysed), although of course, this could be anything else.
Figure 5 - Viewing processes and mutex
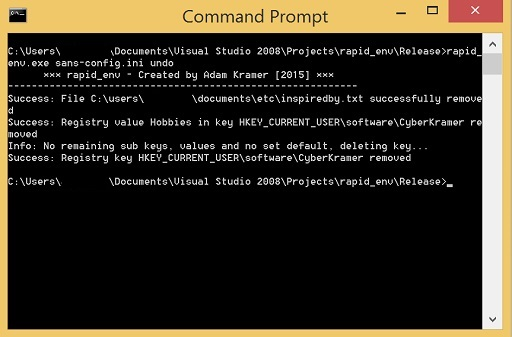
Once we have finished with what we were doing, we may not always want to revert to a snapshot. In these cases we can use the 'undo' functionality built in to restore the system based on the changes requested in the configuration file. As shown in Figure 6 the file and registry key which were added before have now been removed.
Figure 6 - rapid_env undo capability
This tool may also be useful in protecting environments from (re-)infection by setting up the system in such a way that when the sample runs it will presume the system is already compromised and move on, for example, if it looks for a mutex as an indicator of infection prior to installing itself!
This is very much in beta, any comments would be very welcome!
Happy reversing!
— Adam (Twitter: @CyberKramer)





