Tags:
John Pescatore - SANS Director of Emerging Security Trends
This week's Drilldown will focus on one item (included below) from NewsBites Issue 5, which detailed a breach suffered by the European Medicines Agency (EMA). In this breach, attackers not only stole sensitive data, but also altered and reposted some of it on the so-called dark web so that malicious actors could use the bogus data to undermine confidence in COVID-19 vaccines.
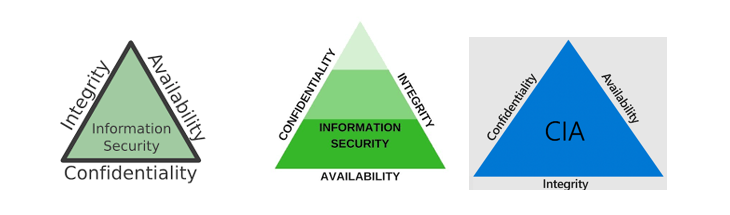
No one really knows when the Confidentiality, Integrity, Availability (CIA) triad was first created. I swear it was around the time I graduated college and went to work at NSA in 1978, but more likely it was first codified as a "triad" in the early 1990s. It is a really clever concept that demonstrates why all three are needed to enable secure business.
Confidentiality is the first term, but by itself that doesn't guarantee either integrity or availability. But, confidentiality is needed to prevent breaches and mechanisms such as encryption and can be used to provide integrity.
Availability is needed to thwart denial of service and most ransomware attacks, but those mechanisms don't provide any support for confidentiality. But, having safe backups is a simple way to restore integrity if data is accessed and modified.
Integrity has always been the most underlooked of the three security processes. Just adding digital signatures to everything or using file integrity monitoring seemed simple and attacks for financial gain by modifying data were harder to launch and thus not as common, though extremely damaging when they did occur.
Of the three graphics above, I like the one on the right that shows Integrity at the base of the triad--essentially the foundation. For digital signatures to work, trustable public and private key pairs need to be supported, which is key for encryption. For file integrity monitoring to work, the file has to be available!
The use of "disinformation" and "deep fakes" during the 2016 and 2020 U.S. presidential elections, and as evidenced by the attack against EMA, point out why integrity is so important. Focusing on integrity requires conquering many of the barriers that have impeded progress on encryption and backup/recovery adoption. Selling management on the essential hygiene elements of CIA as "must do" vs. "assess risk" type processes is key to actually getting closer to business-strength information security.
______________________________________________________________________________
Stolen COVID Data Were Altered Before They Were Leaked
(January 15 and 18, 2021)
The hackers who stole COVID-19-related data from the European Medicines Agency (EMA) altered it before posting it on the dark web. The data pertain to the BNT162b2 vaccine, which was jointly developed by Pfizer and BioNTech. According EMA's most recent update on the cyberattack, "some of the correspondence has been manipulated by the perpetrators prior to publication in a way which could undermine trust in vaccines." Amsterdam-based EMA evaluates applications for medicines to be marketed in the European Union.
[Editor Comments]
[Pescatore] The integrity of data has always been the most overlooked element of the Confidentiality, Integrity, Availability (CIA) triad, but there have been many attacks over the years (most aimed at stock price manipulation) that modified critical data. At a Cybersecurity Moonshot Initiative stakeholders' workshop in 2019, we highlighted fighting deep fakes and disinformation as top of the priority list. More focus on hardening the information is needed.
[Murray] Think digital signatures, hashes (Tripwire), and blockchain.
[Neely] Beyond encrypting data at rest and in transit, data integrity, particularly for official records, needs to be verifiable to detect tampering. Consider digitally signing official correspondence and records. Just as you check the digital signatures for software updates, the same capabilities need to exist for official formation.
Read more in:
Ars Technica: Hackers alter stolen regulatory data to sow mistrust in COVID-19 vaccine
BleepingComputer: Hackers leaked altered Pfizer data to sabotage trust in vaccines
ZDNet: Hackers 'manipulated' stolen COVID-19 vaccine data before leaking it online
www.zdnet.com/article/hackers-manipulated-stolen-vaccine-data-before-leaking-it-online/
EMA: Cyberattack on EMA - update 5
www.ema.europa.eu/en/news/cyberattack-ema-update-5


