I recently acquired a WiFi Pineapple Mark V to replace my Mark IV, and I've got a config script to help folks simplify the config and use of this amazing product.
For those of you unfamiliar with the WiFi Pineapple, it is a wireless attack platform in a box, excellent for penetration testers. It collects a variety of tools into a pen test specific device, a convenient single portable appliance for all kinds of wonderful Wifi hacks. The ability to impersonate a specific access point (AP) is present, as well as abusing client preferred network lists using Karma. You can do funny things like rick rolling, or nasty delivery of a meterpreterer with every page that the user browses to. There are configurable options to exclude specific devices from testing (a black list), or provide a list of devices that are within scope (a white list, which is a much safer way to ensure you don't end up attacking a bunch of nearby devices that aren't in scope of your pen test, which is kind of a big deal if you want to avoid lawsuits and/or jail time).
One guy I know turned on a device in the airport to check to be sure that it was working for a demonstration he was on his way to deliver, and he was frustrated that he wasn't able to get his client to connect. When he logged in to the console, he realized that the people sitting around him had automatically connected to his device. So, use your Wifi Pineapple with caution!
In this article, I'd like to share a modified WiFi Pineapple configuration script (wp4.sh) that I created, which should really help simplify and improve your configuration. This script will get your rolling with your WiFiPineapple quickly.

I'm a lazy person, and my tweaked wp4.sh config script is intended to make setup of the networking configuration easier for me by querying the system I'm setting up for reasonable default values. Sure, I could have just modified the script to the defaults for my computer, but that's not the right fix for the long term. I also optionally redirect http/https traffic to the Burp web application manipulation proxy via iptables.
In this case, my setup is a Linux system wired upstream of the Pineapple. I still like this configuration even though the Mark V now has two wireless antennas (an Atheros b/g/n and a Realtek b/g) that enable binding it to a nearby access point while maintaining the attack capability. I like the wired setup because it lets me observe and manipulate the traffic with my Linux host. (There are a number of cool ways to manipulate traffic on the Pineapple, too, via infusions. Check out the Pineapple Bar on your Pineapple if you haven't done so lately.)
I threw a few tweaks into my script that I'll discuss briefly:
Change 1
I use a system that has a wireless interface that is labeled eth1. The original wp4 script gives me the option to change it from the default but offers a naive default option, so I check for the eth1 interface, or wlan interfaces that are up:
proposedif=`ip link show | egrep "eth1|wlan[0-9]" | grep UP | cut -f2 -d":" | sed 's/ //g'`
Change 2
Similarly, I check the IP address of the computer, and offer the actual IP address as the default option on the IP address of the PineappleLAN interface. I don't check for that interface to be up, because I assume I have connected via a wired connection and I would at least be awake enough to remember to do that. YMMV.
proposedip=`ip addr show $pineapplelan| grep "inet " | sed 's/^ \{1,\}//' | cut -f2 -d" " | cut -f1 -d"/"`
Change 3
I often want to redirect port 80 and port 443 traffic into the fantastic Burp interception proxy in my testing. I'm a lazy guy, so I give myself the option to do so right within the startup script.
echo -n "Redirect 80/443 to 8080? (y/n) [N]: " read burp burp=`echo $burp | cut -c1` if [[ $burp == 'y' || $burp == 'Y' ]]; then burp=y #Thanks Samuel Adams fi ### and if [[ $burp == 'y' ]]; then ## HTTP TRAFFIC iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to -port 8080 ## HTTPS TRAFFIC iptables -t nat -A PREROUTING -p tcp --destination-port 443 -j REDIRECT --t o-port 8080 ## CHECK FOR BURP pgrep -fl burp 2>&1 > /dev/null || echo "Are you sure burp suite is running ?\nOr maybe you intend to use something else. I didn't check for that." fi
If I say "Y" the script will set my iptables rules to redirect client requests for HTTP and HTTPS connections into my burp suite.
I typically use this sort of setup to inspect the connections coming from a device. This is useful for application assessments, as well as profiling client (the person) behavior. In the screenshot below case, I've used my Pineapple to grab traffic from a wireless client operated by a coffee snob looking for excellent espresso drinks.
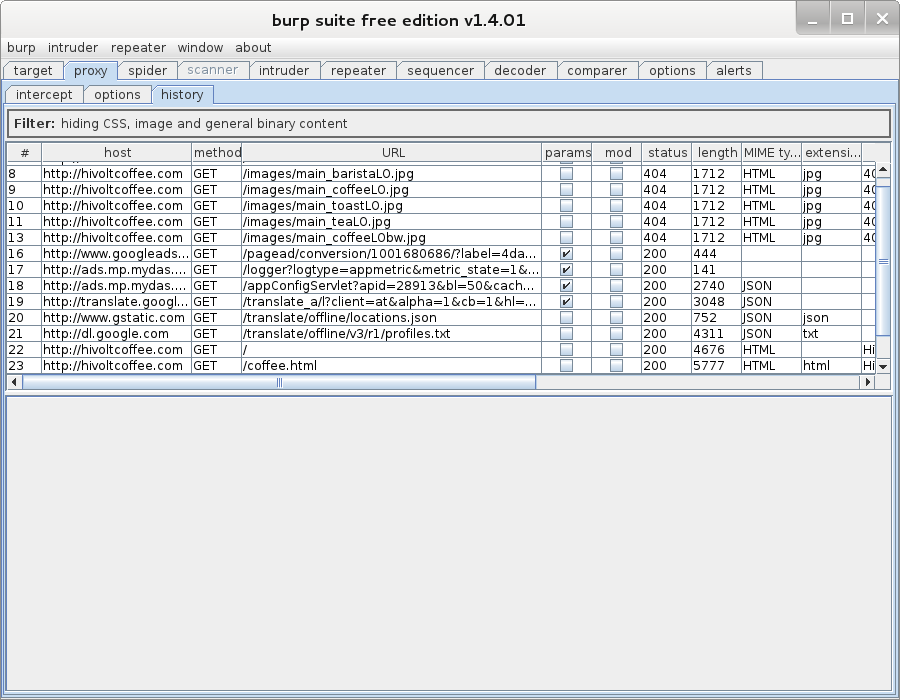
Of course, this will blow up on HTTPS connections because of cert mismatches. In the SANS SEC575 course on Mobile Device Security and Penetration Testing, we talk about some strategies for dealing with SSL certificate mismatches, including using the SSLStrip module that is built into WiFiPineapple via the Pineapple Bar addons section.
Change 4
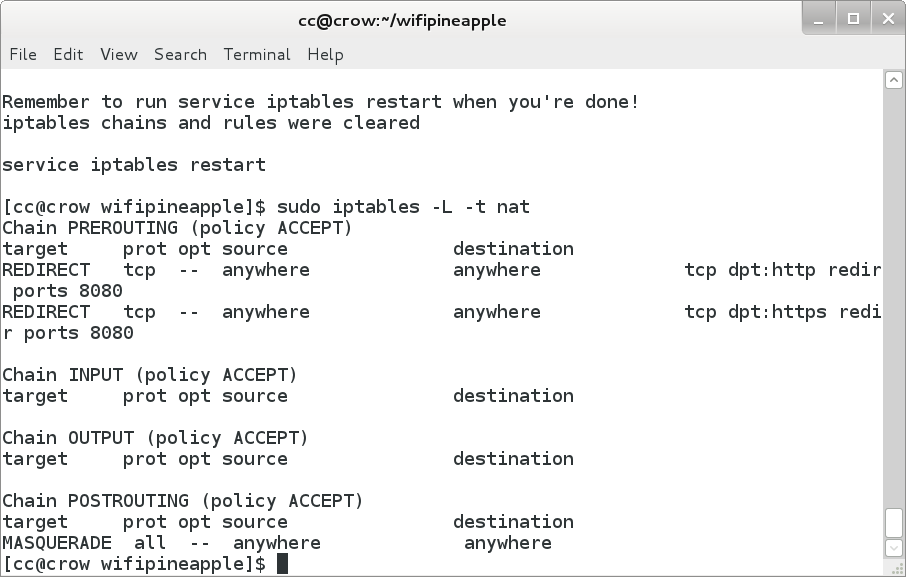
I was surprised when I checked my firewall the first time I ran the original wp4.sh to see that all the rules had been flushed! Yikes! So, I added a little warning to myself and a reminder that the firewall rules had all been flushed, and I would need to restart the firewall to put the default rules back.
echo "iptables chains and rules cleared - your shields have been dropped" ### and echo "Remember to run service iptables restart when you're done!" echo "iptables chains and rules were cleared" echo "" echo "service iptables restart"
Putting all these changes together inside the whole wp4.sh script, here's are the results, suitable for copying and pasting:
#!/bin/bash #define variables echo "$(tput setaf 1) _ ___ _______ ____ _ __ " echo " | | / (_) ____(_) / __ \(_)___ ___ ____ _____ ____ / /__ " echo " | | /| / / / /_ / / / /_/ / / __ \/ _ \/ __ '/ __ \/ __ \/ / _ \" echo " | |/ |/ / / __/ / / / ____/ / / / / __/ /_/ / /_/ / /_/ / / __/" echo " |__/|__/_/_/ /_/ /_/ /_/_/ /_/\___/\__,_/ .___/ .___/_/\___/ " echo " $(tput sgr0) OWN the Network $(tput setaf 1)/_/ /_/$(tput sgr0) v2.1" echo "" echo -n "Pineapple Netmask [255.255.255.0]: " read pineapplenetmask if [[ $pineapplenetmask == '' ]]; then pineapplenetmask=255.255.255.0 #Default netmask for /24 network fi echo -n "Pineapple Network [172.16.42.0/24]: " read pineapplenet if [[ $pineapplenet == '' ]]; then pineapplenet=172.16.42.0/24 # Pineapple network. Default is 172.16.42.0/24 fi echo -n "Interface between PC and Pineapple [eth0]: " read pineapplelan if [[ $pineapplelan == '' ]]; then pineapplelan=eth0 # Interface of ethernet cable directly connected to Pineapple fi
And here's a script that just does the NAT firewall:
#!/bin/bash ## CHECK FOR ROOT wai=`whoami` if [[ "$wai" != "root" ]] then echo " You need to be uid 0. Re-run as: sudo $0 " exit fi ## SET SYSTEM TO PREROUTING IP PACKETS echo "1" > /proc/sys/net/ipv4/ip_forward ## HTTP TRAFFIC iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port 8080 ## HTTPS TRAFFIC iptables -t nat -A PREROUTING -p tcp --destination-port 443 -j REDIRECT --to-port 8080 ## CHECK FOR BURP pgrep -fl burp 2>&1 > /dev/null || echo "Are you sure burp suite is running?\nOr maybe you intend to use something else. I didn't check for that."
One last thing I needed to do on the Mark_V itself is to update the route.
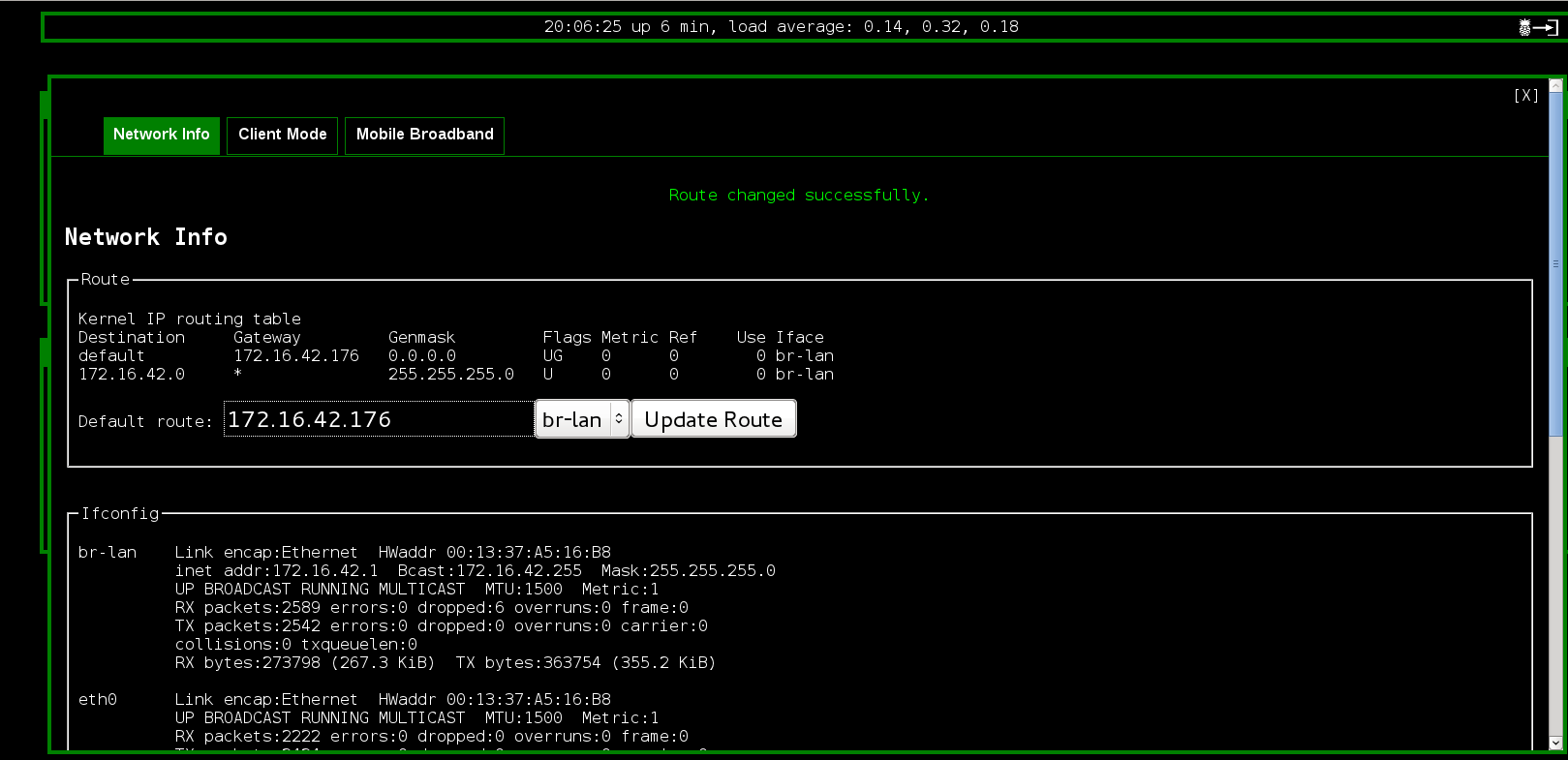
I use this set up for application assessment, client activity inspection, and client content manipulation, simplifying and streamlining my pen test work. I recently had my Pineapple Mark V on when some friends came over to my house. They quickly commented on the cert mismatches, and were surprised at the content replacement they saw. So, don't try this at home. Well, actually, the correct way to work on this at home and in your pen testing is to use the client whitelist feature of the Karma configuration to specifically include those devices which are appropriate for your testing.
There you have it. Enjoy pen testing with the Pineapple!
-Chris Crowley



