Many malware reverse-engineers consider OllyDbg a valuable part of their toolkit. The latest version 1 release of this powerful debugger has been showing its age. Fortunately, version 2.01 seems to be sufficiently mature to start displacing its predecessor as part of the malware analysis workflow. Here's what you can expect when starting to experiment with OllyDbg version 2.01.
Comparing OllyDbg Version 2.01 to Version 1.10
Version 2 of OllyDbg has been around for a while, but the tool wasn't yet mature for mainstream use until version 2.01 came out and a healthy selection of plugins became available. There are many features and improvements in OllyDbg version 2.01 when compared to version 1.10. I will only mention a few that stood out in my testing.
OllyDbg version 2.01 addresses many of the deficiencies that malware authors misused in version 1.10, such as purposefully corrupting PE headers and misdirecting the debugger via fake memory breakpoints. This isn't surprising, given the many under-the-hood improvements the tool's author implemented when rewriting the debbugger.
One of the new features in version 2.01 is the ability to control how the debugger sets software breakpoints, so you can automatically bypass the attempts of the malicious code to detect INT3 breakpoints.
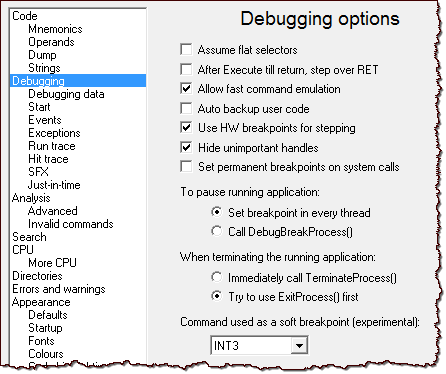
The latest version of the tool also tends to do a better job finding references to API calls if you examine a specimen whose IAT entries aren't quite perfect.
The biggest problem I came across in version 2.01 was related to the debugger failing to recognize common Windows API functions until the malicious program was about to call the function; version 1.10 was able to automatically insert the API call's name as a comment in cases where version 2.01 failed to do this.
Also, I didn't like that OllyDbg version 2.01 automatically enabled its SFX feature. Designed to automatically detect the end of the unpacker, this capability doesn't always work. I found it more useful to enable it selectively when I wanted to experiment with it, just like I did in version 1.10.
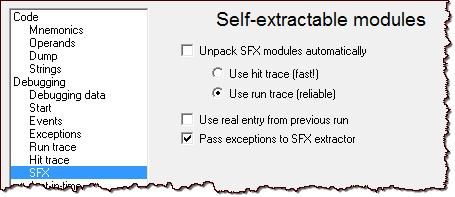
Overall, I was surprised to see OllyDbg version 2.01 properly handling some of the trickier code portions that would have been difficult to examine with version 1.10.
Plugins for OllyDbg Version 2.01
Plugins developed for version 1 of OllyDbg don't work with version 2. However, at this point there are quite a few plugins compatible with version 2.01 of the debugger. For a good listing of version 2.01 plugins, take a look at the Tuts 4 You listing and sort it by data in the descending order.
My favorite version 1.10 plugin was probably OllyDump version 3.00.110 by Gigapede. It was especially good at automatically rebuilding the IAT when dumping the debugged process.
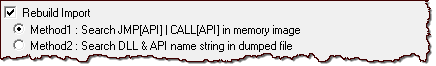
I looked at several process-dumping plugins compatible with OllyDbg version 2.01. My favorite one is OllyDumpEx by low_priority. It offers a lot of control over the dumping process, though it lacks the IAT-rebuilding capabilities present in OllyDump for OllyDbg version 1.10.
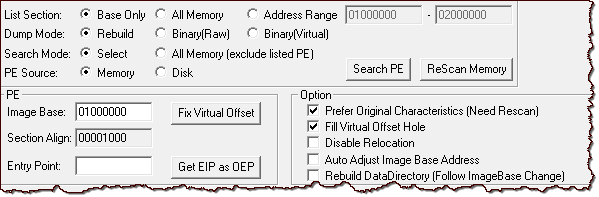
I also liked the OllyExt plugin by Ferrit for OllyDbg version 2.01 for concealing the debugger's presence. This is a good alternative to tools such as OllyAdvanced and HideOD compatible with OllyDbg version 1.10.
Is OllyDbg version 2.01 ready for prime-time? I think it's pretty close. I'm finding myself using it more and more, given the maturity of this release and the increasing availability of stable plugins for it. I still keep version 1.10 around, though, and alternate between the two tools when the need arises. A big thank you to Oleh Yuschuk for developing OllyDbg! His work and contributions to the community are truly amazing.
Lenny Zeltser teaches malware analysis at SANS Institute. He is active on Twitter and writes a security blog.






