(Editor's Note: this blog was originally submitted for posting on March 25th, but wasn't posted until October 4th. We hope you enjoy this content and that Matt Edmondson continues to give freely of his knowledge to the blog.)
Password cracking is one of my favorite parts of information security. Many of us have built computer systems designed specifically for this task. We use tools like John the Ripper for quickie password cracking efforts and Hashcat for larger tasks but we usually sick these tools on cryptographic password hashes we obtain from hashdumps, database tables and tools such as Responder. One of the lessons we've learned from high profile breaches such as Sony is that it's extremely common for users and organizations to also store passwords in document formats such as Microsoft Word and Excel.
In this post we'll talk about why we use video cards instead of our CPUs to crack passwords and how we can use these same tools and techniques to help us get into password protected office documents and archive files that may contain a user's complete list of passwords or other juicy information.
John the Ripper is often the first tool that information security practitioners play with. It's free, easy to use and even tries to automatically detect what type of hashes you're attempting to crack. John is available for Windows, Linux and OS X and is built into several Linux distributions like Kali. If you've never used John before and are using a Windows system, you can download it from http://www.openwall.com/john/ . I would recommend the "jumbo" windows binaries. The jumbo version of John supports more cryptographic hash formats than the regular version of John does as well as a few extra features. The windows binaries require zero setup outside of just extracting the files to a directory.
There is a blog post at https://www.tunnelsup.com/getting-started-cracking-password-hashes/ which gives a very quick overview of using John and has links to some password hashes as well as wordlists for use in password cracking.
After you start cracking passwords, you'll probably get a strong, strong desire to start cracking them faster. The most common solution to this is to use a system with one or more graphics cards (GPUs) and use the GPUs to crack passwords instead of the computer's CPU. While the jumbo version of John does support GPUs, the most popular tool for GPU password cracking is Haschat. It's very well supported, constantly updated, free and can be downloaded from https://hashcat.net/hashcat/ . As long as your video card drivers are up to date, Hashcat should automatically detect your GPU and use it for cracking.
Underneath the surface, password cracking requires a lot of math. Graphics cards are able to perform math functions like these at extremely high rates of speed. Because of this, a tool which utilizes GPUs can crack passwords MUCH faster than a CPU can. How much faster? I made a password protected .RAR file for a quick comparison.
Utilizing John the ripper and my CPU to crack the password, I was making 174 guesses per second. This may sound like a lot but for password cracking, this is as slow as molasses.
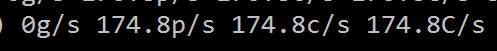
The laptop I'm typing this post on has an integrated graphics card. These types of cards are usually the least powerful type of GPU for these purposes. Even so, Hashcat was able to use the card to make 1,432 guesses per second or over eight times faster than the CPU.
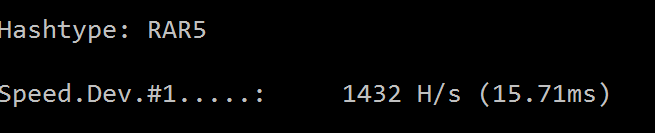
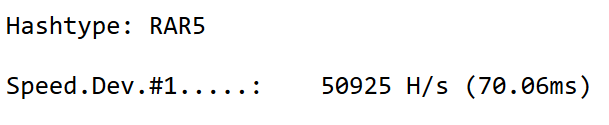
With a powerful video card, the speed increase is usually extremely large. A GTX 1080 Ti video card (currently over $500 on Amazon) is able to make over 50,000 guesses a second which is almost 300 times faster than CPU alone.
Getting started using GPUs to crack passwords is easy, but not necessarily cheap. If you have a system with a powerful graphics card, you already have everything you need. If you have a desktop computer sitting around you can probably buy a graphics card to put in it but you may have to upgrade the system's power supply as well as high end cards tend to be power hungry.
If you're on a budget you can buy a midrange video card like a GTX 1060 and still get a lot of bang for your buck. If money is no object, you can chain together multiple video cards and crack even faster. The Hashcat forums at https://hashcat.net/forum/ are a great place to check for performance benchmarks and ask advice.
These are all great options but we're burying the lead here. If we point Hashcat at a RAR file to crack, it will look at us confused and politely let us know that it doesn't see any hashes in the RAR file. There are isolated tools out there that will try to crack specific file types but we didn't build a GPU password cracking rig to not use its power to crack so how do we get a hash from the RAR file? The answer is John the Ripper. Well, not John himself, but his friends.
In the latest version of John the Ripper there are approximately sixty add on applications and python scripts in the run directory designed for you to be able to point at a file for it to generate a hash.
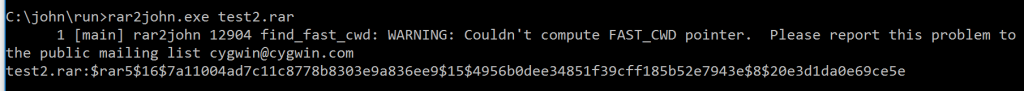
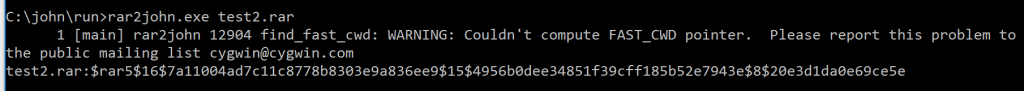
I've tried a few different file formats over the years and have had relatively good luck. Here is file from winrar:
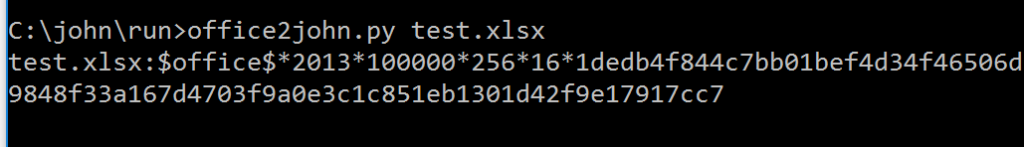
From excel 2013 (not that anyone stores their passwords in an office document):
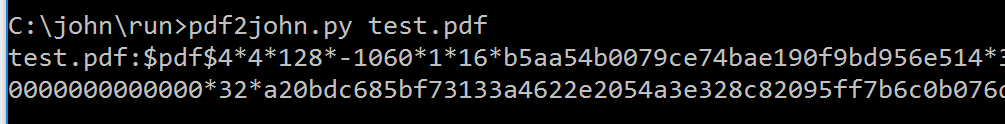
And a PDF:
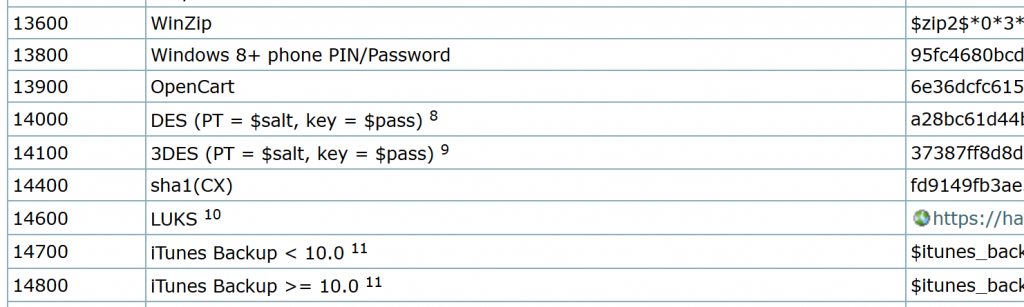
Once we have the hash we can then use Hashcat or any other tool we want to try to crack the password. If you're curious what the hash for a specific type of file should look like, the Hashcat wiki has a great entry of example hashes at https://hashcat.net/wiki/doku.php?id=example_hashes.
So while a lot of us have gone away from using John the Ripper in an effort to take advantage of the power of GPU password cracking, we can still use him when we're trying to get into password protected files that we commonly encounter on engagements.
There is a lot of overlap between the different realms of information security and one of the things I love most about teaching the SEC504: Hacker Tools, Techniques, Exploits, and Incident Handling for SANS is getting a chance to look at techniques from both an offensive point of view as well as a defensive perspective. Utilizing a GPU to access password protected documents can provide the keys to the kingdom on a penetration test, or a vital piece of information while performing digital forensics work.
Matt Edmondson
SANS Instructor
Twitter: https://twitter.com/matt0177



