The Restricted Bash Shell
The Bash shell is a nearly ubiquitous way to interact with a Linux console. A little know feature is the restricted Bash shell, which you can invoke by calling "rbash" or "bash --restricted". While it isn't something you would normally opt into, it certainly a situation I've been placed in due to strict polices or limited device resources. Here are some of the limitations imposed:
- Setting or unsetting the values of the SHELL, PATH, ENV, or BASH_ENV variables.
- Specifying command names containing slashes.
- Specifying a filename containing a slash as an argument to the . builtin command.
- Specifying a filename containing a slash as an argument to the -p option to the hash builtin command.
- Importing function definitions from the shell environment at startup.
- Parsing the value of SHELLOPTS from the shell environment at startup.
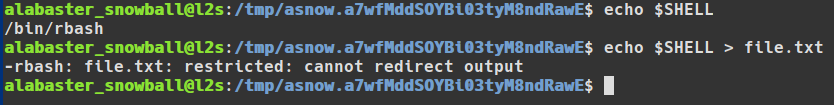
- Redirecting output using the '>', '>|', '<>', '>&', '&>', and '>>' redirection operators.
- Using the exec builtin to replace the shell with another command.
- Adding or deleting builtin commands with the -f and -d options to the enable builtin.
- Using the enable builtin command to enable disabled shell builtins.
- Specifying the -p option to the command builtin.
- Turning off restricted mode with 'set +r' or 'set +o restricted'.
Dotting I's and Crossing Tees
Tee is a wonderful utility that soaks up "stdin" and sends it all to a file along with "stdout". It's just the trick to get around a restricted shell where I/O redirection is being blocked. With "tee" it's possible to bypass "rbash"'s I/O restrictions and send arbitrary data to a file.
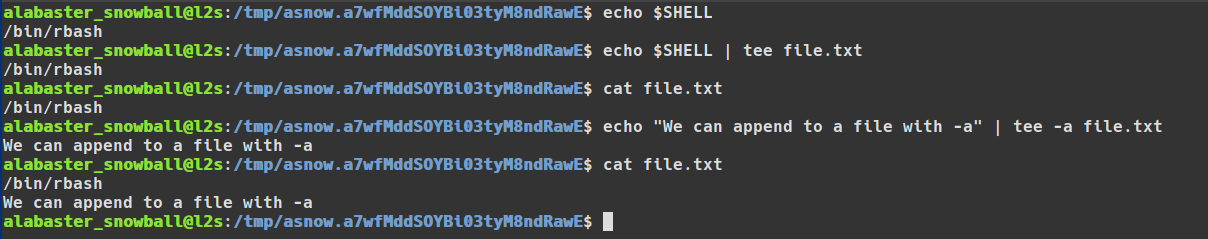
Tee can even be used to append data to a file with the -a flag.
-Daniel Pendolino
Counter Hack
Bash restrictions sourced from gnu.org


