Tags:

Today’s issue of NewsBites, like many over recent weeks, focused on the growth of attacks targeting the millions of employees who are working from home. One NewsBites item captured the key points to focus on:
[[10]] Joint Advisory on COVID-19-Related Phishing Attacks
(Published April 8, 2020)
The US Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) and the UK’s National Cyber Security Centre (NCSC) have issued a joint advisory warning of an increasing volume of cyberattacks exploiting the spread of COVID-19. Cybercriminals have been sending phishing emails that pretend to come from the World Health Organization or claim to be offering medical equipment.
[Editor Comments] [Pescatore] The joint advisory covers 4 vectors of observed attacks taking advantage of the current coronavirus situation: (1) Phishing; (2) Targeted Malware; (3) Registration of phony domain names; and (4) Attacks against VPNs, RDP and remote access in general. There are individual news items in this issue of Newsbites on each area with more detailed comments, but the overall theme should be: crank security up a notch – now is the time to risk more false positives until your organization’s work and IT processes/temporary architectures have stabilized. SANS continues to add resources to the free Security Work-From-Home Awareness Deployment kit and there are daily webcasts as well.
Most security professionals are familiar with the defined phases of incident response – but the pandemic has really thrown us more into crisis response than the typical security incident response.
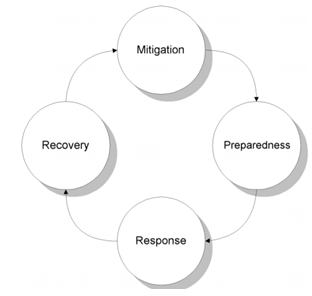
Source:FEMA Crisis Management
Most businesses and government agencies are still in response mode to the immediate need to support large scale remote work. The joint advisory from the US DHS and the UK CSC point out the attackers are also in response mode – there are many tactical things to work on now to prevent the attackers from succeeding.
However, transitions that inevitably follow business damaging events often provide an opportunity to make advances in security:
- Malware decimating Windows IIS servers in 2001 caused Microsoft to radically improve security in Windows 2003 and beyond.
- Terrorist attacks causing New York City’s Twin Towers to be destroyed caused the movement of backup data centers to be further apart. Hurricane Katrina caused such widespread damage that the separation recommendation was increased.
- The movement from Windows 7 to Windows 10 allowed many organizations to make leaps in security progress by ratcheting up privilege and applications controls.
- Zoom’s CEO announced a security push after “Zoombombing” and other exposures hit the news as skyrocketing remote work caused an exponential increase in Zoom use for sensitive purposes.
Most of the above examples are reactive, just as we see major changes after every mega-breach. Unfortunately most progress is made after significant business damage occurs.
However, the security gains many companies made when going from Windows 7 to Windows 10 are a good example for what can happen as part of the transition back to more normal operations as the economy emerges from the virus impact. Those gains in work at home flexibility and security should be maintained and enhanced with maintainability, visibility and backup. Advances in two-factor authentication, enhanced endpoint protection and more secure cloud services should also be part of the recovery plan.
Think of this event as similar to a huge forest fire – after the fire is out, growth begins and if done right we end up with a beautiful new landscape that is also much less likely to erupt in widespread flash fires in the future.

