SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsCreative Ways to Keep Your Existing Cyber Talent in Your Organization

After all of the time, effort and work organizations do to attract top quality cyber security talent, the journey of keeping the best of breed talent in your organization is just beginning. As many who are in the field can attest, the day to day role of a cyber expert is ever evolving and the external search for cyber security talent is just as aggressive. Employees put their best efforts forward during their day to day and have come to expect the same out of their employers. When an employee starts to have doubts about their job security, feel overwhelmed or perceived to be unheard, the risk of them going to “better’ pastures increases. Unfortunately, all of the hard work that was done by the company to recruit their cyber superstar has to start all over again. Understanding what some of the top pain points cyber security professionals feel during their employment will allow organizations to get ahead of employee discontent before the employee walks out the door.
I always enjoy talking to cyber security professionals when I interview them about why they are seeking employment elsewhere. It sometimes turns into an exit interview during the on-boarding interview process! I have noticed during this part of the on-boarding interview process, candidates can be thoughtfully candid about why they are thinking of leaving an organization. I appreciate them being upfront because it is also an opportunity for me to better understand how to keep top quality talent on my team as well. Some of the top reasons cyber security professionals are looking to leave their jobs are the following:
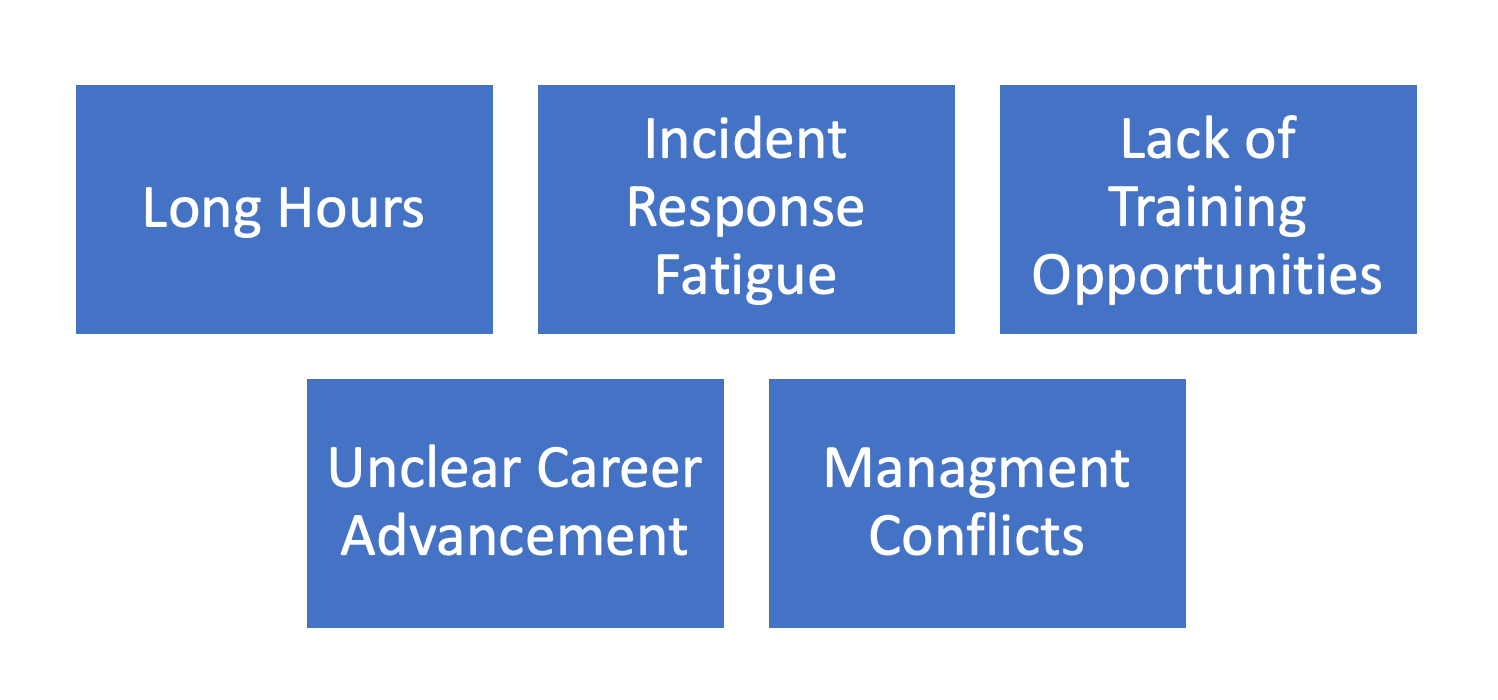
The nature of the cyber security business requires vigilant 24x7 coverage. Whether it is identifying a threat in an environment as quickly as possible to take the necessary triage steps or if it is understand what the new threat of the day that requires an investigation, cyber security professionals need to be on their toes at all times. Unfortunately, these reactionary next steps come at a cost. Work that was slated to be completed by the employee may need to be pushed off. Yet the requirement to complete that work does not go away. In order to complete the new “action required” items plus their existing workload, employees work before and after their shift. Rethinking workloads for the teams is a must in the cyber industry.

Cyber security professionals have to investigate types of events and incidents that come their way. Unfortunately, some of these investigations expose the worst parts of humanity. Working through these incidents can take a serious mental toll on a cyber professional. As leaders and HR professionals, it is important to be proactive with employees to ensure they have the company’s support and backing as they work through these investigations.

The best cyber security professionals understand one of the keys of attempting to get ahead of a bad actor is stay abreast of the latest TTPs (tactics, techniques and procedures) bad actors are utilizing. However, between the long hours many professionals put in for the BAU (business as usual) work and the extra work on incidents, having time to take training can seem like a luxury. Additionally, unless management specifically allocates budget for training, a professional may have to ask for a specific training. Unfortunately, many employees may not feel comfortable asking for an organization to pay for their training even though they really wanted to take a training. This may make the employee look around at other employers who make it a point to consistently send their employees to training. Employees who want to continue to develop their skills want to know their employer supports them on their journey.

Many cyber professionals want to continue to build upon their careers in the industry. Career advancement will look different to everyone, however much of the advancement is based on their growing technical knowledge and/or responsibility. Employees should have the opportunity to showcase not only the great skills they have now but also the even stronger skills they will have in the future. However, without understanding what each individual wants out of their career, it is hard for an employer to set the employee up for success. Often, employees may find this conversation to be an uncomfortable topic to bring up to their managers as well. The lack of communication may make the employee believe they will never have a chance at growing in the organization they are in and they may start looking elsewhere for their career advancement.

Almost always when I talk to people looking for another job, the conversation about how they are unhappy with their management seems to pop up somewhere in the conversation. Individuals want to work for an organization that supports them, fosters their growth and makes them feel like a valued asset. In particular, if they perceive their direct manager conflicts with that balance in any way, an employee is going to start looking around outside of the company.

Employees are our most important assets in any organization. Employees also count on an employer to help foster their growth in an organization and to be recognized for their efforts. Listening to employees and their needs can help managers and HR professionals work together to help slow the revolving door of cyber security professionals in this competitive cyber workforce landscape.
1. Listen to the corresponding webcast here.
2. Read the rest of the Blog series here:
Kevin Garvey is the US IT Security Manager for an international bank responsible for overseeing incident response, vulnerability management, cyber threat intelligence, as well as the security operations center (SOC). Previously, he worked at New York Power Authority, JP Morgan and WarnerMedia (formerly Time Warner). Kevin has always had a passion to hunt down the adversary and has loved tackling the risk and threat challenges his responsibilities have thrown at him. Kevin teaches SANS MGT512: Security Leadership Essentials for Managers. Read Kevin's full profile here.


Kevin is the IT Security Manager for an international bank, responsible for overseeing incident response, vulnerability management, cyber threat intelligence, as well as the SOC. He has worked at New York Power Authority, JP Morgan and WarnerMedia.
Read more about Kevin Garvey