SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsThe Network and Information Security Directive (NIS2) is currently being translated into national legislation by European Union (UE) member states. In this series, we ask SANS instructors and seasoned cybersecurity experts about the implications of NIS2 for organizations.

The Network and Information Security Directive (NIS2) is currently being translated into national legislation by European Union (UE) member states. In this series, we ask SANS instructors and seasoned cybersecurity experts about the implications of NIS2 for organizations. Carlos Fragoso is a digital forensics and incident response subject matter expert Maltego and SANS instructor for SEC401 and SEC504.
NIS2 is the successor to the 2016 European Network and Information Systems Directive (NIS). The first version aimed to improve the cybersecurity posture and risk management of critical infrastructure and digital service providers in all member states. "We all remember 2020 being a very disruptive year with the COVID pandemic," said Fragoso. "The lockdowns as well as the many data breaches like the SolarWinds attack caused a quick digital transformation and evolution of the threat landscape causing a significant impact on supply chains and essential services. The EU noticed inconsistencies in how member states applied the first directive, so they devised an enhanced and extended directive in January 2023. This NIS2 directive is currently being shaped into each member state's national legislation, which must be done by October 17th, 2024. The goal of this new directive is to increase resiliency and reduce inconsistency in the internal EU market."
The NIS2 directive increases the number of sectors that must comply to 18. Eleven of them are highly critical, comprised of companies called essential entities and seven industries called critical, where organizations are labelled important entities, (see the Which Organizations Are Essential or Important? section below). "An organization can identify if they fall under NIS2 if they operate in one of the mentioned sectors or provide digital services like domain name registration or operations, cloud computing, online marketplaces, or search engines," said Fragoso. "It is still too early to discuss criteria or benchmarks because all member states are still developing national legislation. However, I assume there would be some levels or certifications that will show they are compliant."
NIS2 requires organizations to apply cybersecurity controls that are mapped to the new regulation. "This could have a considerable impact on those organizations that were not in the scope of NIS1, especially if their current cybersecurity governance or maturity level is not high. They will have to increase the bar quickly to be compliant,” Fragoso said. This also goes for companies that may not directly fall under the scope of NIS2, as that directive has some precise demands on supply chain security. "In the past, we have seen that not all companies can properly identify how others could impact them. So, the new directive wants organizations to identify all components and their providers that could impact the organization within the product or service it provides. Organizations then need to establish the risk of those components and act accordingly."
Another new NIS2 requirement focuses on cybersecurity incident notification, explained Fragoso. "You will need to notify your reference cybersecurity incident response team (CSIRT) within 24 hours when there is an incident with significant impact." The new directive also mentions a specific network for coordinated cyber crisis management: EU CyCLONe. "I don't yet have the details of this specific element of the directive," said Fragoso. "However, I would guess this would mean a coordinating body to ensure a cybersecurity crisis can be managed across all EU member states. We already have an EU cybersecurity agency, the European Union Agency for Cybersecurity (ENISA), so I am assuming at this moment that ENISA will probably take some of these coordination roles because they already have the mandate of the EU to do this kind of thing."
In terms of preparing for NIS2, Fragoso believes that while there's not currently many details regarding the controls organizations must have in place to comply, companies can always enhance their current cybersecurity posture. "All organizations should start a project to review NIS2 and national legislation as soon as this is made public by national governments, to map their cybersecurity controls. Most of the required controls may already be in place but need adaptation," said Fragoso. He pointed out companies that meet industry security standards like ISO will probably already have many of the required controls. "However, we may see some things shift from being optional to mandatory under the NIS2 legislation." At the same time, Fragoso said, organizations should start preparing their teams with skills development and cybersecurity training, considering standards such as the European Cybersecurity Skills Framework (ECSF) and related US frameworks like those from NIST and NICE.
Fragoso advised organizations to commence cybersecurity exercises if they are not being done regularly. "This should be done as part of incident readiness. Obviously, when applying controls to better protect, early detect, and better react to any potential incident, you need to test those. The best way to do this is by doing cybersecurity exercises. In the past, many of those exercises were at a very tactical or operational level, but seeing as NIS2 now also makes management liable for the organization's cybersecurity, it is essential to conduct these exercises on a broader level." This also applies to training all staff within the organization. All staff, not just the people on the shop floor or the IT and security staff, must comply with the new regulations. This includes management and top-level executives, as they will be liable for any significant incident according to NIS2. "Organizations need to step up their game regarding cybersecurity knowledge, skills and ability," said Fragoso.
NIS2 does not explicitly apply to entities in areas such as defense, national security, public security, or law enforcement, however, the scope indirectly impacts them as governments try to enforce and ensure NIS2 compliance. "So, most member states must not only locally translate NIS2, but also have the knowledge and understanding of how to do it and be able to advise on implementation and strategy. And the must of course get involved in cyber-attack investigation when notified by victim organizations that fall under NIS2. Government agency, retainer, or contractor digital forensics and incident response (DFIR) teams must understand the aspects that need to be considered for preparation, such as cybersecurity exercises and proper response, including coordination and notification,” Fragoso said.
Fragoso couldn’t say for certain whether NIS2 will make the lives of DFIR experts easier or more difficult. "I don't think NIS2 will affect DFIR as a discipline because we have already adapted the discipline to response and investigative processes. Dealing with cybersecurity isn't something we started yesterday," Fragoso said smiling. "We've been doing it for quite some years now. So, in the short term, NIS2 may cause a work overload for governance, legal, and security teams to ensure the organization has a plan and implements the required controls. In the middle term, there may be a period to clarify ambiguities and fix anomalies or incorrectly implemented aspects of the plan. But my guess is their lives will be easier in the long term because having a framework and security controls ultimately helps everyone." The framework in place may help DFIR teams enforce cybersecurity controls within the company more easily. "It gives them more power, authority, and visibility."
One of the most important things organizations can engage in at this time is a discussion with their government bodies to get relevant information about the local NIS2 implementation as early as possible. "Also, it's probably wise to hire an advisor, some external body, to help understand what controls need to be in place and how to best comply with the new legislation. Someone outside your company can be more neutral when you try to get things done internally," explained Fragoso. Last but certainly not least, Fragoso urges companies to ensure they are incident-ready by testing their organization against cybersecurity exercises. "Some organizations are already doing this as part of another regulation, but they may only do one annual exercise because they are mandatory. I advise companies to do them periodically, at least twice or thrice yearly so you can have an indecent readiness program covering the proper processes, technology, and people."
NIS will be a continuous improvement process. Fragoso predicts that this second version of the directive will also prove to have inconsistencies between member states or elements that need to be clearer. "And then we can probably expect NIS version 3 as an improvement on this current directive, as when it comes to cybersecurity, we will never be fully finished in protecting EU organizations and improving their cybersecurity posture."
Which Organizations are Essential or Important?
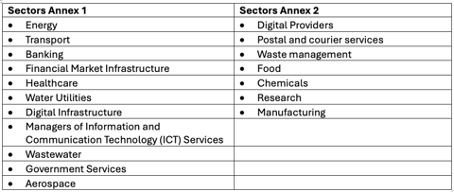
Essential Entities: Large organizations operating in a sector from Annex 1 of the NIS2 Directive.
Key Entities: Medium-sized organizations operating in an Annex 1 sector and medium and large organizations operating in an Annex 2 sector.
An organization is considered large based on the following criteria:
An organization is considered medium-sized based on the following criteria:
In this series on NIS2, we highlight the new directive from different angles so that CISOs and their organizations can gain insight into how to deal with NIS2.
Achieving NIS2 compliance is a significant milestone for any organization. Let SANS be your guide, with our comprehensive learning paths, certifications, and resource center tailored to your needs. Embark on your compliance journey at here.
As SANS maps out industry preparedness for the new EU Commission's NIS2 Directive, your insights are invaluable. Please take a moment to complete the NIS2 survey to contribute to our research. Your feedback will help us provide the guidance and resources needed for this and future directives.


Carlos is Principal Subject Matter Expert at Maltego Technologies with over 22 years of professional experience in information security: incident response, digital forensics, and threat intelligence/hunting.
Read more about Carlos Fragoso