SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact Us
Stop Pulling The Plug!!
Over the past several years, many tools have been released that have focused on memory acquisition from Windows systems. The next step in memory forensics is analysis. Starting with the DFRWS 2005 challenge, memory forensic analysis began a life that went beyond a rudimentary string search or data carve. Analysts were finally able to extract process related data from memory captured from a machine.
In 2008, this culminated with many professionals stating at the SANS Forensic Summit that the day of "pulling the plug" during evidence acquisition is no longer acceptable. In fact, in my discussions with law enforcement, many are already obtaining memory captures during evidence seizure.
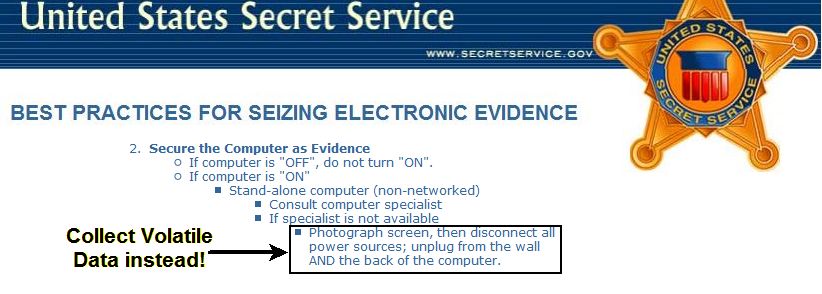
In some cases, it is recommended that the individual seizing the computer system utilize a friendly neighborhood geek computer specialist to help, but it does not specifically state what the specialist should accomplish. Given the relative importance of collecting memory, it should be taught in basic forensic courses.
What I would like to demonstrate in this article is how to acquire memory from a hacked Windows machine and perform an audit of the machine's process listing and network connections using Memoryze and Volatility.
fau dd.exe, Mantech mdd, win32dd, and the recently released Mandiant Memoryze.
I had previously worked with the FAU dd.exe, mdd and win32dd for quite some time so I wanted to explore the capabilities of Memoryze which include both analysis and acquisition capabilities. FAU's dd.exe no longer has a built-in memory acquisition mode.
This year has seen many tools released that allow for memory analysis. Memoryze is a new tool co-written by Mandiant's Peter Silberman and Jamie Butler and provides a wonderful new capability for the incident responder where both acquisition and analysis of memory can be accomplished via a single tool. Memoryze, is derived from the core processing engine of the Mandiant created enterprise product called Mandiant Intelligent Response or MIR for short.
Volatility is another awesome tool that can analyze collected memory images from tools like mdd, win32dd, or Memoryze. Volatility was written by Aaron Walters and can be also downloaded as an intergal part of the SANS SIFT Workstation.
After working with Memoryze and Volatility for a few days, I found myself convinced that this was going to shift responders away from using traditional incident response and forensic process tools. Typically, a responder would use native or sysinternals tools to obtain a listing of running processes and network connections.
What will incident responders use instead? For process and network enumeration, they will probably lean completely on memory acquisition and analysis. Why? It is arguably better for forensic integrity of the live machine. You run a single tool to acquire system memory from a live machine versus running many smaller tools such as pslist and fport to accomplish the same thing but with lackluster results if a rootkit is installed.
To demonstrate: I started with an installation of Windows XP and installed nc.exe and the Hacker Defender rootkit. I added netcat to the startup registry key and had it listening on port 22201 where it would execute a command prompt (cmd.exe) if anyone connected to that port. Before I used the rootkit, I could easily see that I had started a nc.exe process running. Using Hacker Defender, I hid the process, files, and network connections from prying eyes. When hacker defender is running, the process name is called hxdef100.exe.
Using traditional incident response tools, I see the following output from fport and pslist.
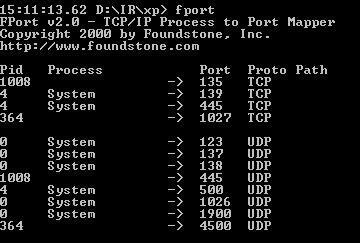
Notice that there is no listening port 22201.
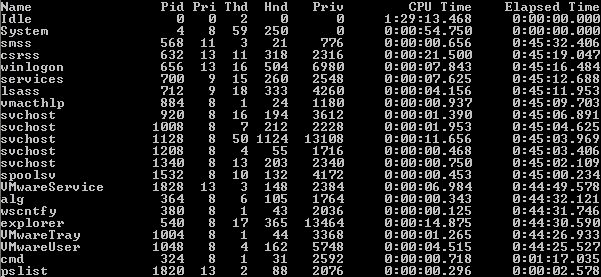
Notice that there are no visible processes called hxdef100.exe or nc.exe.
This is where tools such as Memoryze or Volatility are indispensable in the incident response/forensic world. Simply acquire the memory image and analyze offline.
After I installed Memoryze on a USB key, I plugged in the USB key and acquired memory using the batch script called Memorydd.bat which is included with Memoryze.
You could also use mdd or win32dd to acquire memory. All three memory images could be analyzed using the analysis tools in Memoryze and Volatility.

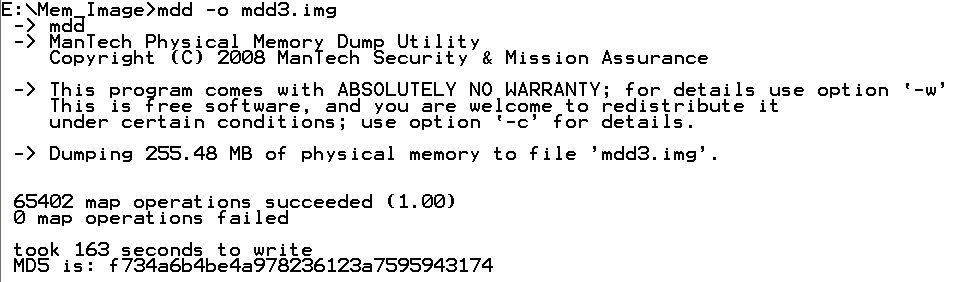
Once I acquired the memory image, I performed some additional analysis against it. This enabled me to look at the processes in memory similar to the output in fport and pslist by using another batch script included with Memoryze called process.bat that can be executed on a WinXP analysis machine.
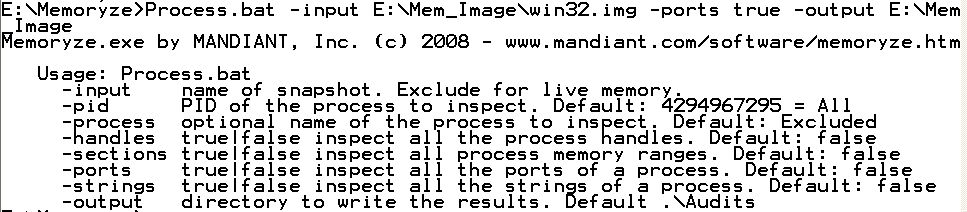
Once I executed process.bat, I saw that it created an xml based output file which is not easy to read by itself. Luckily, the output file is easily imported into Excel 2007 where the results can be examined.
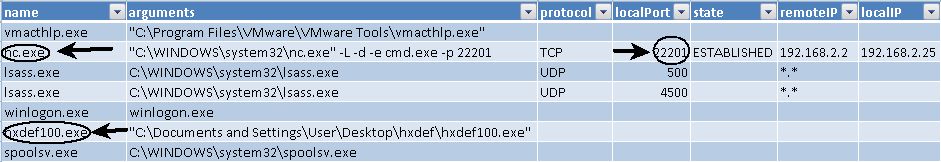
Notice the nc.exe process listening on port 22201. Also notice the hxdef100.exe process. Compare that to the previous process list by pslist where those same processes were not listed.
Again utilizing the same memory images, you can use the Volatility installed with the SANS SIFT Workstation.
First we run Volatility examine the process list from any of the memory images.
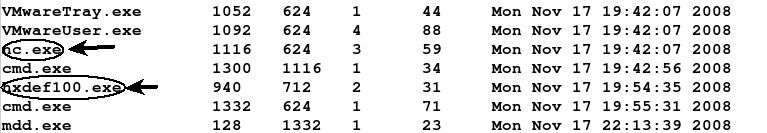
The output from the command above shows the two processes that were hidden by the Hacker Defender rootkit.
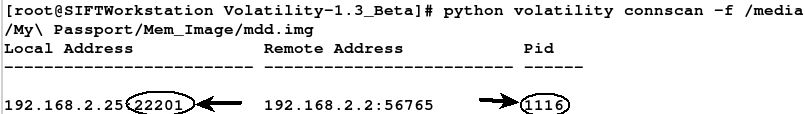
And finally using Volatility to show the nc.exe process has an open connection listening on port 22201.
It is a good idea to obtain memory for several reasons:
Tools such as Memoryze and Volatility are helping analysts and crime fighters win the argument about why it is important to acquire memory before pulling the plug. Analysts now have both a means of acquisition and a means of analysis. I could go on about what else you could do with these tools as there is more... much more to be shared next time.


Rob T. Lee is Chief AI Officer and Chief of Research at SANS Institute, where he leads research, mentors faculty, and helps cybersecurity teams and executive leaders prepare for AI and emerging threats.
Read more about Rob T. Lee