SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsFree Tool for Regulatory Requirements for Risk Management

At the time of this post, we have identified over 35 international cybersecurity standards that require organizations to utilize a cybersecurity risk management process as a part of their approach to defense. While many of these standards are unclear what they mean when they encourage risk management, it is becoming more common to see regulations requiring organizations to do so. The following cybersecurity standards all a few examples of standards that require organizations to integrate cybersecurity risk management into their overall cybersecurity program strategies:
In addition, there are numerous standards that require risk assessments to be performed against both the organization itself and each of an organization’s critical third-party business partners. The following are some of the more popular cybersecurity standards that also require an organization’s risk management program to include their third-party business partners:
Part of the challenge organizations face when attempting to comply with these cybersecurity standards is understanding exactly what the requirements are asking an organization to accomplish. This becomes even more challenging when organizations are asked to perform a task whose definition is often cloudy. Cybersecurity professionals as a whole often struggle to provide a succinct definition for the word “risk,” therefore, it is not surprising that the authors of cybersecurity standards would have the same challenge.
The following are specific examples of requirements from some of the cybersecurity standards listed earlier and the specific wording from the standard related to cybersecurity risk:
“The organisation should ensure a risk assessment is also carried out for the organisation, development environment, test environment, training environment.” –SCCA (2.3 (1b), v2023)
The most common requirement these cybersecurity standards ask organizations to implement is to regularly perform a cybersecurity risk assessment to validate the implementation of appropriate cybersecurity safeguards. In other words, organizations are being asked to regularly review their cybersecurity safeguards to ensure that appropriate defenses are in place to protect the confidentiality, integrity, and availability of the organization’s information systems.
For organizations looking to perform a comprehensive cybersecurity risk assessment in light of the requirements discussed earlier, an organization may consider different approaches and tools. When attempting to comply with these standards, an organization's main goal is to validate that they have implemented an appropriate set of cybersecurity safeguards. To accomplish this, an organization must first select the baseline of safeguards they want to compare themselves against. Once they have selected their baseline, they can determine which software tool will best meet their needs to record the results of their validation process.
Still today, Microsoft’s Excel tool is one of the most popular tools used by cybersecurity auditors and risk analysts to document the status of their organization’s cybersecurity safeguards. Other tools, such as Governance, Risk, and Compliance (GRC) engines, can also be used for this purpose. However, because of cost and complexity issues, Microsoft Excel is the tool of choice for most of these assessments.
The creators of the Collective Controls Catalog have also created a free cybersecurity risk assessment template that organizations can use to identify gaps in their cybersecurity programs. This template was created in Microsoft Excel and, therefore, is a familiar interface that organizations can use to document the status of their cybersecurity safeguards.
Organizations can download the latest version of this risk assessment template at:
https://www.auditscripts.com/free-resources/collective-risk-project/
Organizations can use this tool to record the status of each of their cybersecurity safeguards and create simple-to-use dashboards to report the status of those safeguards to leadership stakeholders.
In the Collective Controls Catalog Assessment Tool mentioned above, the idea is to answer a series of questions about the status of an organization’s cybersecurity safeguards. The Collective Controls Catalog defines forty cybersecurity domains, each with its own set of specific safeguards. During a risk assessment, the assessor should work their way through each domain and document each safeguard's status.
To begin, the assessor should navigate to the cybersecurity domain they are assessing by clicking on the corresponding tab at the bottom of the Microsoft Excel worksheet. For example, if the assessor wants to assess the topic of “Asset Inventory,” then they should click on that tab, and they will see a screen like the following:

From this tab, there are two questions the assessor must answer for each cybersecurity safeguard listed in the column on the left side of the worksheet. First, they should evaluate the state of the organization’s documented cybersecurity intentions (often referred to as cybersecurity policies). By clicking on the first field, the assessor will see a drop down box similar to the following:

The assessor should then choose the appropriate status option based on the state of the organization’s documented cybersecurity safeguards. The assessor should review the organization’s documentation and answer this question for every cybersecurity safeguard and every domain noted in the workbook.
Next, the assessor should similarly report the status of the implementation of each cybersecurity safeguard. When the assessor clicks on the next box, they will see a drop-down list with options like the following:

The assessor should then review the implementation status of each of the organization’s cybersecurity safeguards and report the status using this field in the worksheet. Via interviews and direct observation of safeguards, the assessor should work with the organization to honestly report the status of each safeguard until the entire list of safeguards has been evaluated.
When an assessor has finished documenting the status of each of the organization’s cybersecurity safeguards, the risk assessment template will automatically analyze the data inputted into the tool to give the assessor specific feedback on the status of the organization’s safeguards. To view the aggregated results, the assessor should click on one of the dashboard tabs listed at the beginning of the Microsoft Excel workbook.
On the first page of the workbook, the template will report an overall maturity score for the organization in addition to domain-centric scores for each of the forty domains listed in the Collective Controls Catalog. First, the assessor will see an aggregate maturity score for the organization, that appears as follows:
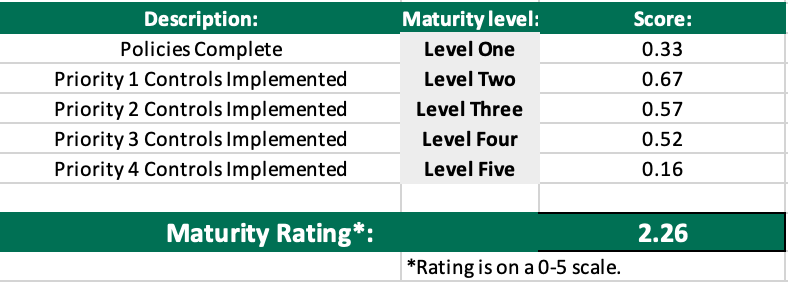
Next, the assessor will see graphs representing the aggregate scores for governance-related domains defined in the Collective Controls Catalog in a graph like the following:
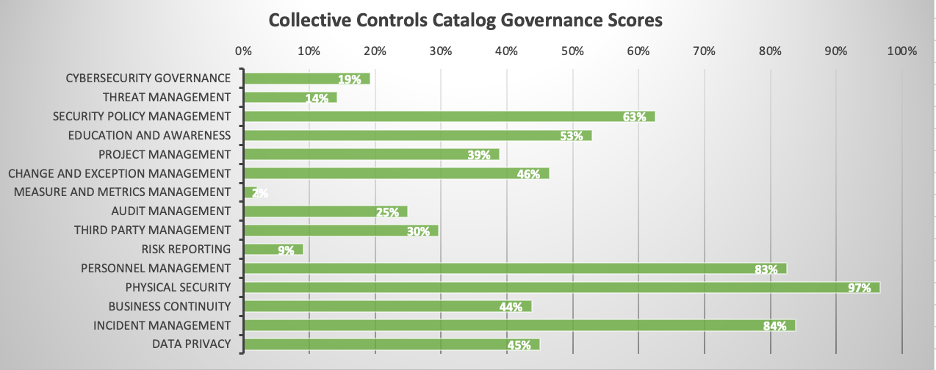
Also, the first page of the workbook will report the aggregate status of technical domains defined in the Collective Controls Catalog in a graph like the following:

This tool will report on the status of cybersecurity safeguards based on the domains defined in the Collective Controls Catalog. In addition, it also has built-in dashboards for reporting safeguards against other popular cybersecurity standards, such as the NIST CyberSecurity Framework (CSF), ISO27002, and CIS Controls.
In conclusion, we trust that the risk assessment template shared in this post will be valuable in your cybersecurity toolkit and help you and your organization achieve the risk management requirements defined by many of the recent cybersecurity standards. In addition, the template illustrated above was designed to streamline the safeguard validation process and help organizations identify gaps in their defenses. We encourage you to customize this template to suit your specific needs and make cybersecurity risk assessment a regular, integral part of your organizational strategy to secure your information systems and help your organization achieve its mission.
In addition, if you would like to learn more about how to perform cybersecurity risk assessments practically, you may also want to consider the SANS course, LDR419: Performing A Cybersecurity Risk Assessment.
James Tarala is a principal consultant with Enclave Security based out of Venice, Florida, and a SANS Senior Instructor. As a consultant, he has spent the past several years designing large enterprise security and infrastructure architectures, helping organizations to perform security assessments, and communicating enterprise risk to senior leadership teams. He is the author of the brand new LDR419: Performing a Cybersecurity Risk Assessment, as well a number of previous SANS courses. Learn more about James Tarala.


James is a managing partner at Cyverity, specializing in cybersecurity risk and governance. A SANS instructor for 20+ years, he holds 14 GIAC certs including the GSE, and has helped author the CIS Controls, CRF resources, and courses like LDR419 and LDR519.
Read more about James Tarala