SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsThreat-Informed Defense isn't just a buzzword; it's a necessity for effective security posture of your organization.


Cyber Threat Intelligence (CTI) teams often find themselves overwhelmed by the sheer volume of threats. Considering the diversity of business and operational environments, focusing on highest-priority threat mitigation can be difficult, especially for teams with limited resources.
How can such a team effectively identify the most critical threats and build a robust Threat-Informed Defense program? This blog post focuses on linking three core CTI processes into a verifiable process for prioritizing adversary tactics, techniques, and procedures (TTPs) - Priority TTPs (PTTPs) and creating intelligence products at three levels:
Starting with the organization’s PIRs, we can derive priority threat actors (TAP), and work towards prioritizing associated TTPs using the PTTP methodology. The blog post will walk you through the whole process, using the fictional company STELLAR Electric as a tangible example to illustrate how PIRs can be the North Star for your Threat-Informed Defense.
STELLAR Electric is a fictional EU-based electric vehicle producer that established itself as a key player in both the European and Chinese markets. With production and research facilities in both the EU and China, the company is facing a significant challenge: limited battery production capacity that impacted its growth.
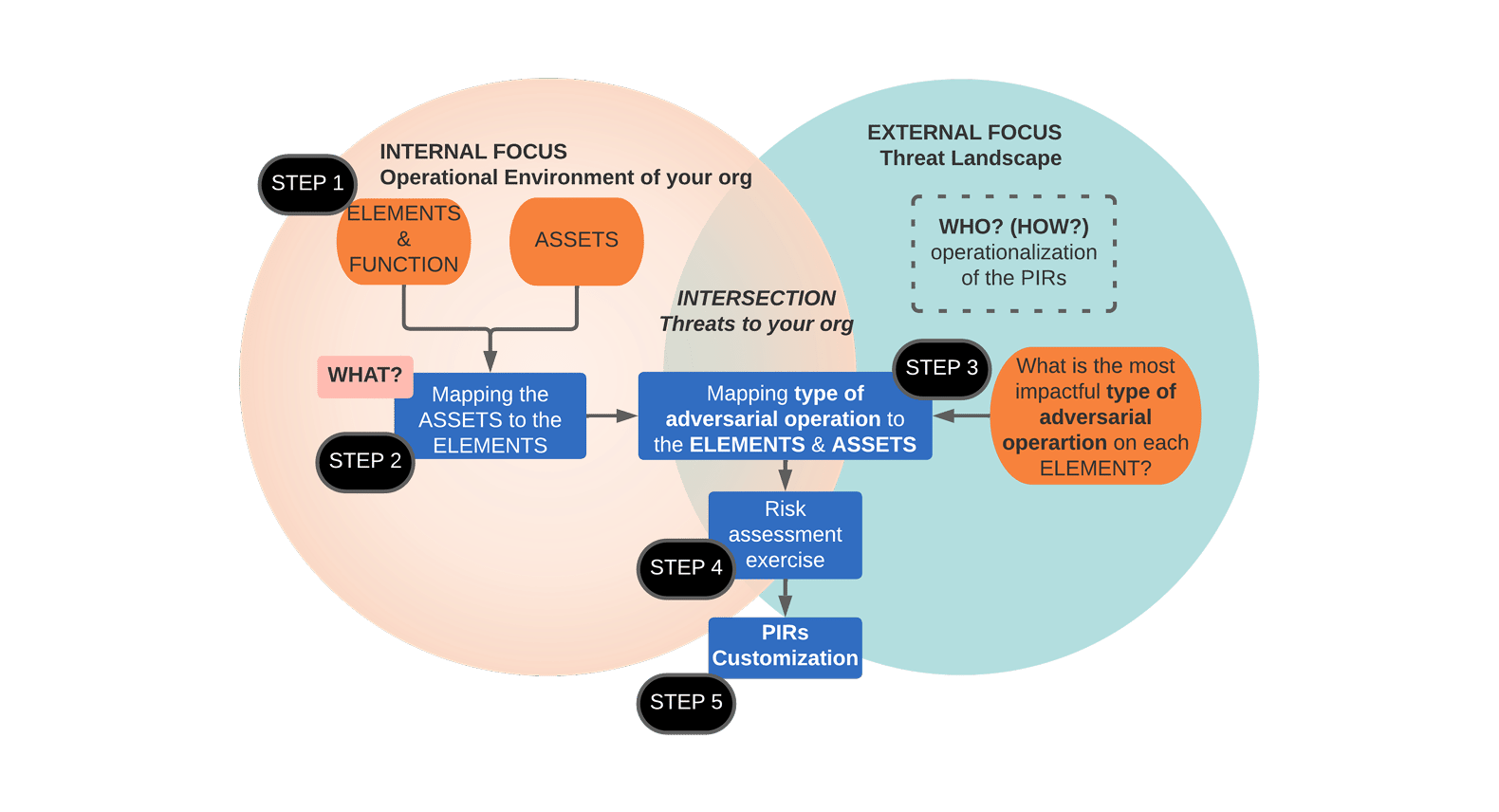
The journey begins with developing Priority Intelligence Requirements (PIRs). While PIRs might sound academic, they function as the "North Star" for many CTI activities, especially for teams with the ambition to move beyond a purely reactive stance. PIRs enable teams stop chasing the “threat of the day” or fulfilling ad-hoc requests (RFIs) and instead adopt a proactive approach. While reactive and proactive approaches can coexist, a well-defined set of PIRs creates a structured expansion of proactive CTI capabilities.
PIRs benefit a wide array of CTI activities:
The path from PIRs to a robust threat-informed defense isn't always straightforward, but it's a journey worth taking.
While many CTI frameworks emphasize the importance of PIRs, few offer concrete guidance on how to develop them. Fortunately, there are publicly available methods and vendor-supported services:
The Red Hat PIR process recognizes the need for a "north star" to guide the proactive CTI efforts. The process aims to:
A fundamental step is defining the organization's ELEMENTS; keywords, topics, or short sentences that capture the organization’s strategy, mission, and vision. These can be gleaned from annual reports, CEO presentations, or "About Us" sections of a company website.
For STELLAR Electric, ELEMENTS might include "range-boosting technology" and "limited battery production," reflecting their core business and potential vulnerabilities. Additionally, their threat profile is defined by the countries they operate in and position in the supply chain.
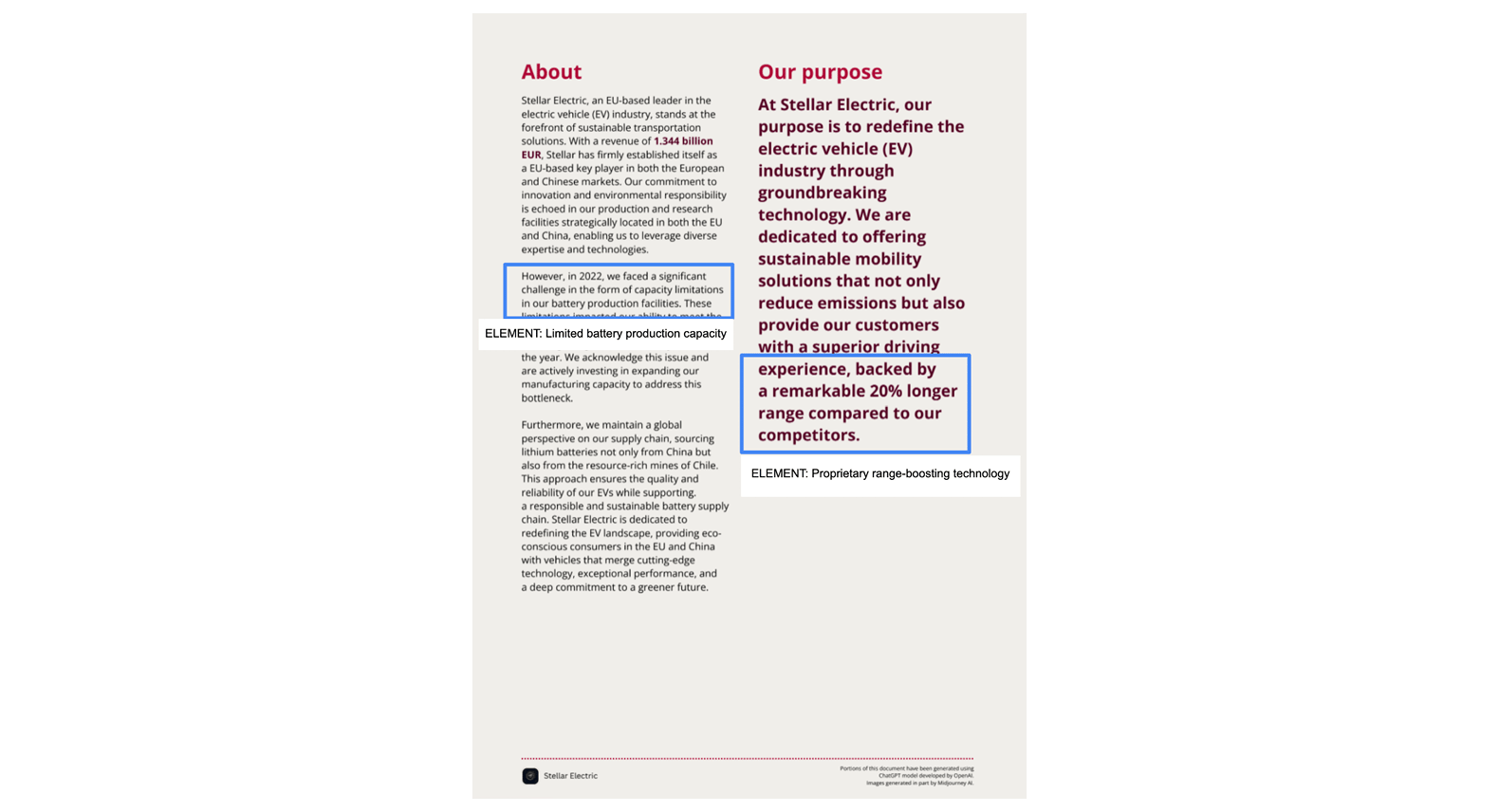
While beyond the scope of a brief overview, the Red Hat PIR process is publicly available on a GitHub.
The output is a set of short, company-specific PIRs, often including likely "type of attack." It's worth noting that formats vary: some methods provide a list of questions, while others provide a list of keywords in areas such as malware, adversarial tactics or vulnerabilities (as in Intel471's methodology).
Once PIRs are defined, the next step is operationalizing them.
One of the initial steps in operationalizing PIRs is enriching them with keywords that define each PIR. For example, Stellar Electric’s PIR #1 is “Proprietary range-boosting technology: 20% longer range compared to competitors,” the keywords could be: industrial espionage, proprietary information, confidentiality, automotive, car industry, battery technology etc. These keywords can be integrated in a Threat Intelligence Platforms (TIPs) or used for alerts on threat landscape events relevant to your organization. While this requires careful tuning, it's a highly effective way to leverage your PIRs for proactive monitoring.
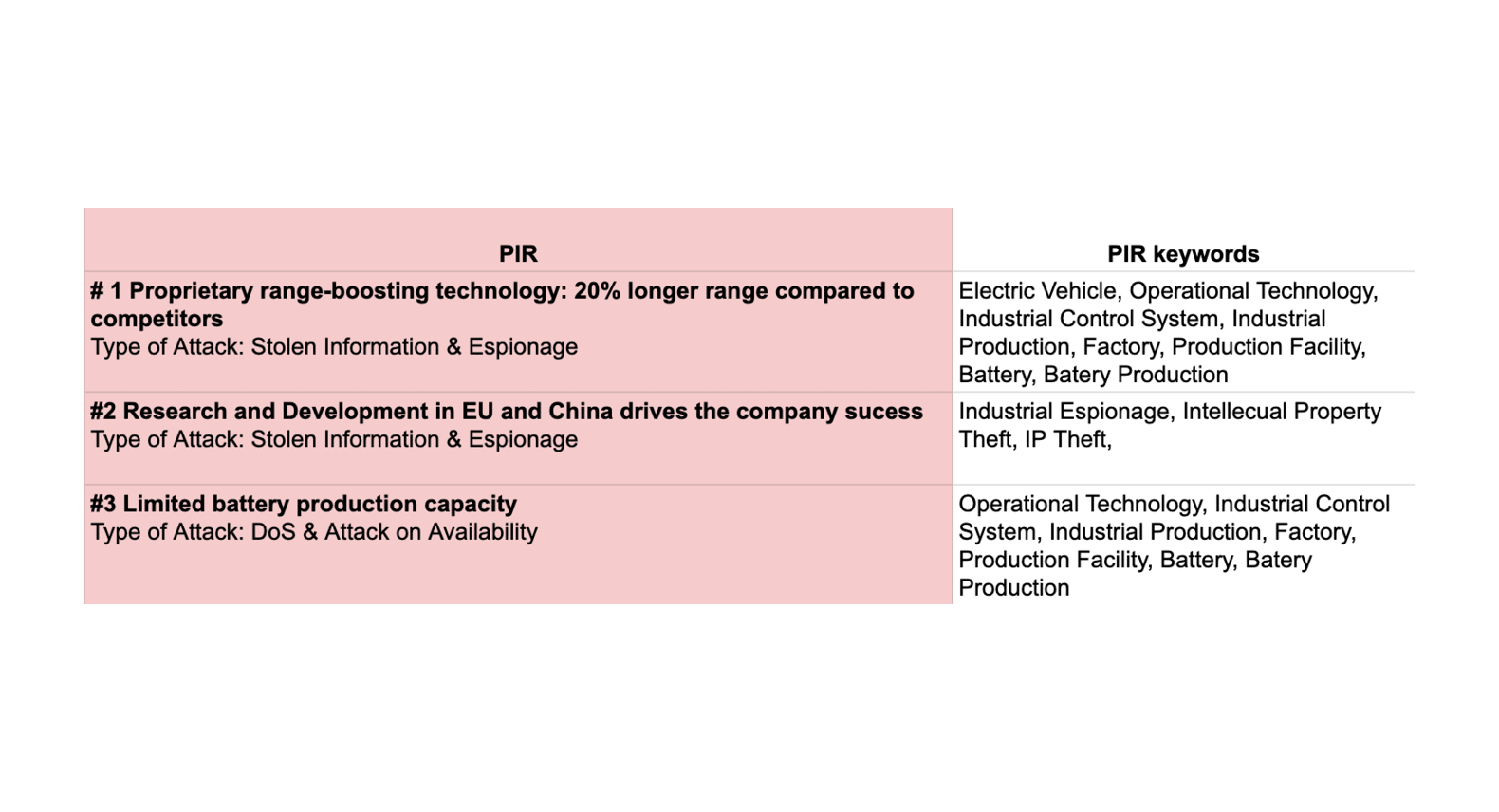
However, the journey often involves further exploration. After the initial keyword-based alerts, a common challenge is translating PIRs into more specific, actionable intelligence. This is where the concept of Threat Actor Prioritization (TAP), also called cyber threat profiling, comes into play.
Once you have your PIRs and their associated keywords, you're in a much better position to ask:
This is true even for organizations that experienced a major security breach and have primarily dealt with a single, known adversary or a narrow set of adversaries. While it's natural to focus on the immediate threat, a comprehensive TAP helps prevent tunnel vision, ensuring you don't overlook other active or emerging threats. To avoid the bias of solely gravitating towards your well-known adversary, actively seek out intelligence on a broader range of threats. This includes looking at industry-wide attack trends, intelligence from peer organizations, and reports from threat intelligence vendors that cover a wider spectrum of actors and their activities.
The approach to TAP can draw on established methodologies, though even a well-crafted Google search using your PIR keywords can provide valuable insights. For initial brainstorming, even AI tools can be a starting point, though they shouldn't be relied upon solely.
So, you have a list of priority threat actors. Again, "So what?" A list of names, while analytically satisfying, has limited standalone value. The true power emerges when you connect these actors to their Tactics, Techniques, and Procedures (TTPs), to effectively inform organization’s defenses and drive impact in most critical areas.
Adversary groups can be mapped to practical elements like atomic indicators, malware, campaigns or, more importantly, TTPs. This is where the MITRE ATT&CK Navigator becomes an indispensable tool.
For each of your priority threat actors, you can create a separate layer in the MITRE ATT&CK Navigator, pulling data directly from the Navigator itself, your CTI vendor, or other public sources.
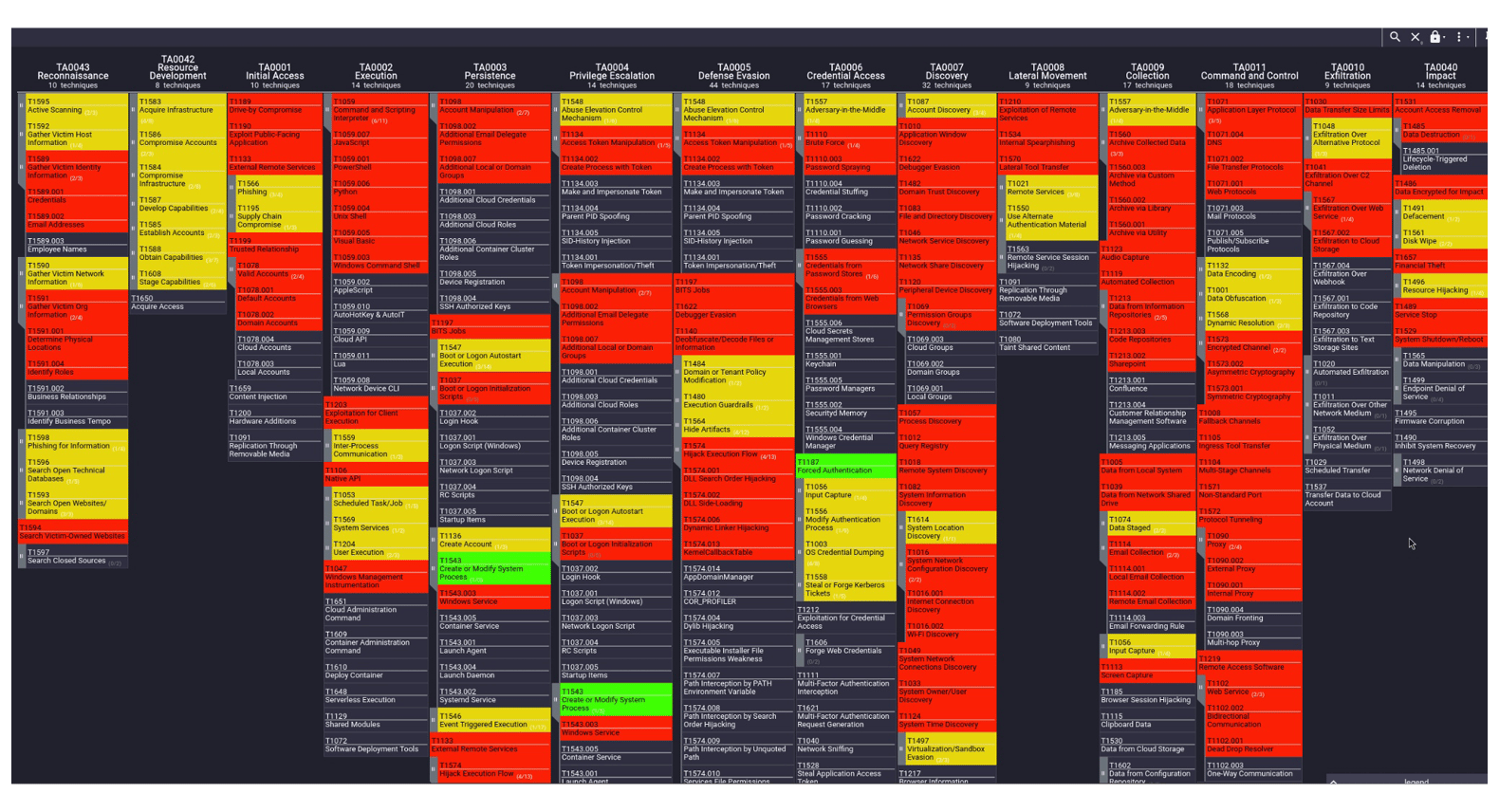
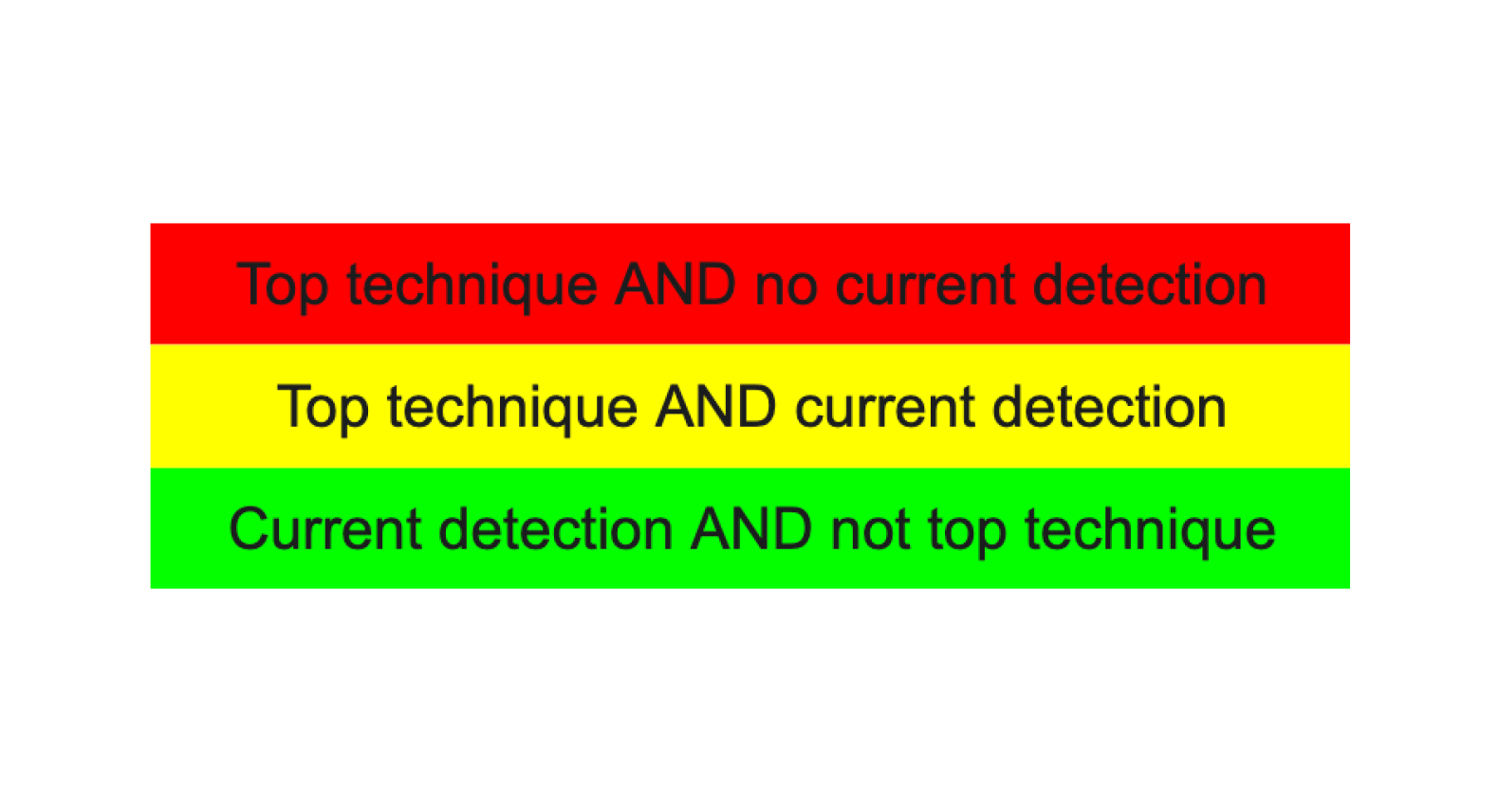
Once you have individual layers for each priority threat actor, the next step is to combine them into a heatmap, where darker colors indicate techniques used by multiple threat actors.
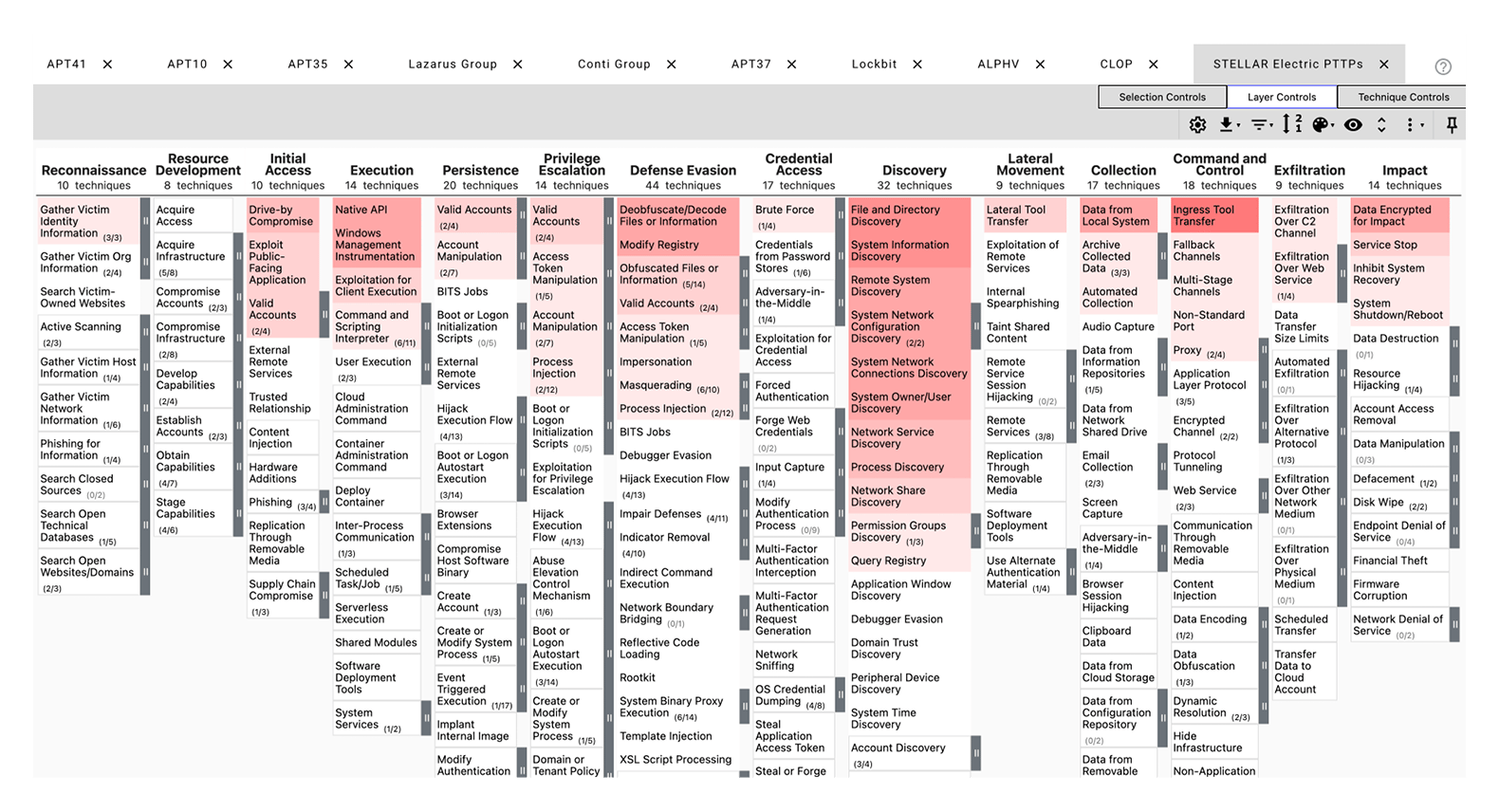
While we initially experimented with a more laborious approach, manually extracting TTPs from relevant threat reports of priority threat actors, this proved to be inefficient. A significant overlap (around 85%) with effortlessly available MITRE ATT&CK data made the manual effort less worthwhile. At the same time, if you want to have the dataset under your full control and understand what data goes in, you can collect the data manually. You can extract lists of MITRE ATT&CK T-codes only from reports that are relevant for your industry or organization. Unlike in the case of the available MITRE ATT&CK data where you have no control of the data age, you can work only within a time period of your choice. The heatmap is a good tool to show in blog posts and in executive slideshows, but it can be difficult to work with directly. In response to this The Red Hat CTI team created a tool that makes generating the report easier.
Now that you have a ranked list of Priority TTPs (PTTPs) you can again ask "So what?". How helpful is it to actually have PTTPs?
A simple list of top techniques, or a heatmap, is a good starting point. You can decide on the practical number of top techniques to focus on - top 10, top 25, or any other relevant figure.
These PTTPs become the actionable intelligence that drives various security functions:
Threat Detection Priorities: Compare the MITRE T-codes of your existing detections with the recommended detections based on PTTPs. This helps you focus your efforts on developing new detections for critical, uncovered PTTPs. Directly guide your detection engineering efforts, using frameworks like DeTTECT or MITRE D3FEND to build robust capabilities.
In summary, threat-informed defense can be effectively guided by a cascading logic process:
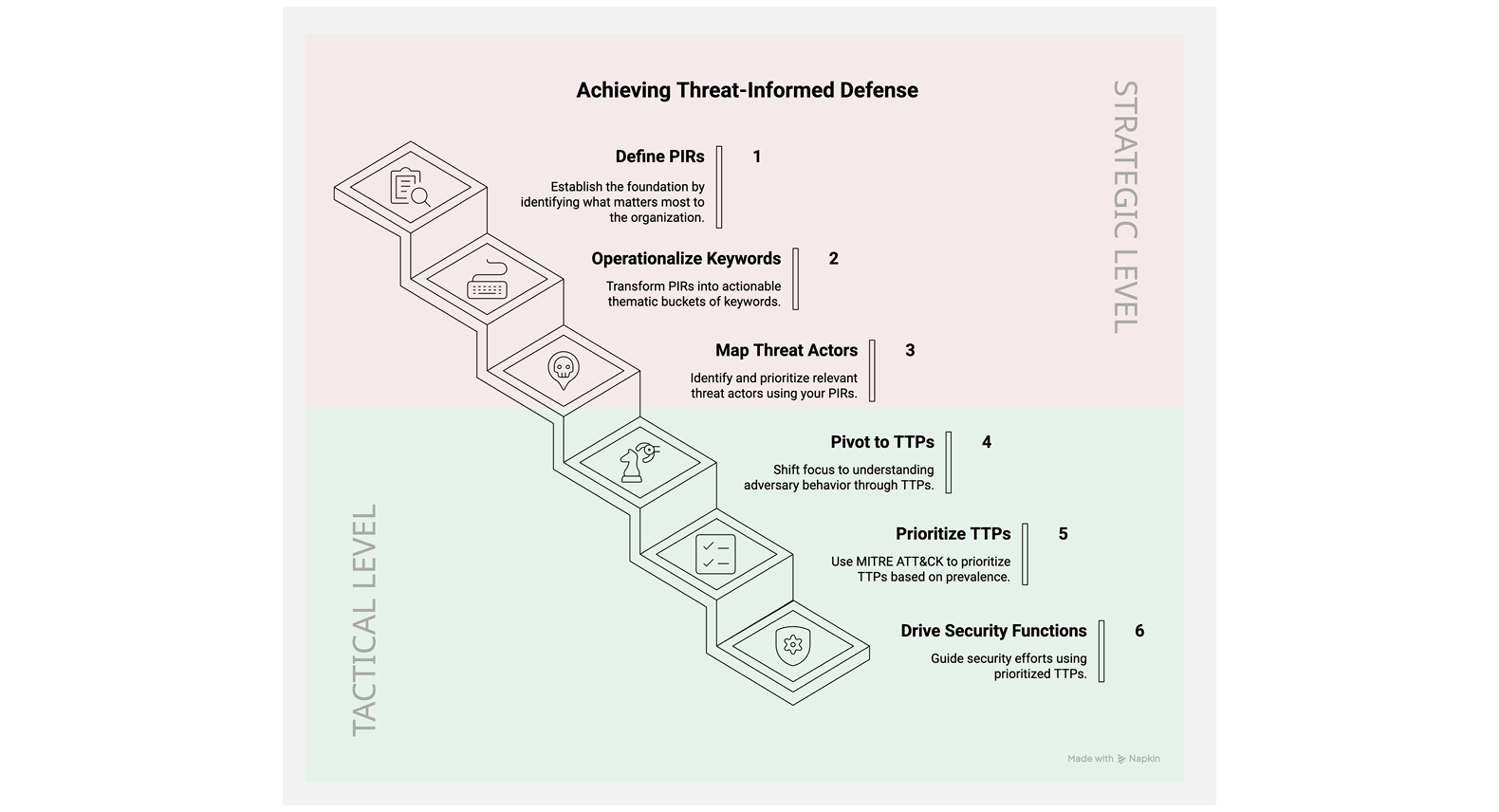
Threat-Informed Defense isn't just a buzzword; it's a necessity for effective security posture of your organization. And, as we demonstrated, at its heart can be a cascading logic process that begins with PIRs. Think of your PIRs as the bedrock of a truly proactive CTI program. They define what matters most to your organization, acting as thematic "buckets" for your intelligence gathering. From there you can get to priority threat actors and TTPs.
A crucial point to remember is that while TTPs linked to known threat actors are vital, they shouldn't be your only input for a Threat-Informed Defense. The threat landscape is vast, and not all malicious activity can be attributed to a recognized group. And when it is, it is often done by different vendors and analysts, with attribution and activity clustering under different naming conventions (e.g., Mandiant vs Microsoft vs CrowdStrike). A holistic view is essential. By grounding your defense in the strategic process we've outlined, you'll be well on your way to a more robust, intelligent, and truly threat-informed security posture. CTI teams can maintain focus amidst the noise, direct technical teams with actionable intelligence, and effectively bridge gaps across detection, response, and governance functions, transforming generic threat feeds into custom-fit security actions.
Ready to make a real-world impact with your strategic intelligence? FOR578: Cyber Threat Intelligence teaches how to build and operationalize a threat-informed defense using PIRs, threat actor profiling, and prioritized TTPs.


Ondra Rojcik is a Principal Cyber Threat Intelligence Analyst at Red Hat's CTI team, where he provides intelligence analysis and strategic perspective to the program and its analytical outputs.
Read more about Ondra Rojcik

Keith has 10 years of IT experience, and previous security experience in Incident Response, Vulnerability Management, and Compliance in private sector and federal contracting roles.
Read more about Keith Swagler