SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsDean Parsons, Certified Industrial Control System instructor, addresses control system cyber defence through teaching the newly updated ICS515 course.

Can your security and engineering teams run your industrial operations and control system operations in manual mode in the case of a ransomware cyber event? How are your facilities conducting remote access, and is it secure? Does your ICS/OT security program monitor control networks with ICS-specific traffic analysis tools to prepare for active incident response and a resilient incident recovery?
Supply Chain attacks are increasingly a viable vector for some adversaries. Malware such as Ryuk, Darkside and Ekans-type ransomware continue to threaten Industrial Control System (ICS) operations. Suboptimal secure remote access will be abused by adversaries on the Internet if multi factor authentication is not deployed. ICS targeted attacks are “living off the land” – abusing and turning legitimate ICS/OT systems and software against the ICS itself to cause impact.
Recent targeting and an intrusion into a water utility in Oldsmar Florida [1] in early 2021 shows an attacker remotely using the Human Machine Interface (HMI) on an operator’s machine to manipulate the process. Specifically, the attacker manipulated set points and increased the amount of a chemical normally used in the water process, Sodium Hydroxide (NaOH). NaOH is normally used in the process of treating drinking water, but in higher than normal amounts it can be very hazardous to humans.
The method of attack is not limited to water utilities. Facilities should ensure remote access, if required, follow the principle of least privilege, should deploy multi-factor authentication to a secure “jump box” in an ICS-DMZ zone with separate authentication than that of a business domain, and always monitor remote connections. Furthermore, ICS networks should always be properly segmented from business networks, between process zones, safety systems and the Internet. Another significate event from 2021 was the effects of Ransomware on an IT network as part of the Colonial Pipeline infrastructure, where the incident did in several ways have impacts on logistics and/or billing of the ICS operations. The incident ultimately lead to a pipeline shutdown as a safety precaution [2].
Cybersecurity in ICS is all about safety 1st! So, those new to managing OT security, or in a recently converged IT & OT environment should know IT practices will need to be adapted for ICS networks to prioritize safety. This means a nuanced discussion on if or where encryption is used, network traffic threat prevention vs. detection, and a growing requirement for “plant-floor” and ICS specific control system network visibility for proactive ICS defence and industrial incident response.
A significant number of adversary tactics, techniques, and attack procedures (TTPs or tradecraft) can be detected by Network Security Monitoring (NSM) of control system traffic. This is crucial to detecting the types of threats briefed here and can also spot "living off the land" techniques seen in recent ICS targeted events such as CRASHOVERRIDE [3] and TRISIS/Hatman [4] - adversaries abusing native ICS protocols. At a minimum, ICS facilities and critical infrastructure operations should work to deploy and maintain the ICS ACDC [5] (Active Cyber Defense Cycle). This means a dedicated team being actively involved with monitoring and responding appropriately to ICS threats, how are specifically trained in ICS/OT control system cyber security and defence. Trained ICS/OT defenders know well how to setup, deploy, and maintain the ACDC cycle for proactive control systems defence. ACDC consists of five parts.
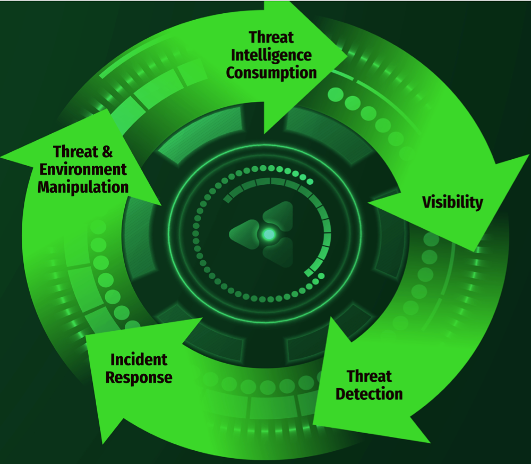
1. Threat Intelligence Consumption. Cyber threat intel is refined information with context on cyber threats and threat groups, which defenders can leverage to detect, scope, or prevent the same or similar attacks previously observed.
2. Visibility. This means having a comprehensive asset inventory and a passive view of the ICS network traffic, utilizing technology that can dissect and properly interpret specific industrial protocols in network.
3. Threat Detection. Detecting threats requires the capability to leverage technology that sifts through data for malicious signs of attack attempts or intruder entry, and trained ICS specific defenders that can hunt for threats.
4. Incident Response. Successful incident response requires having forensic capabilities to execute quick triage and adapting steps of incident response specific to control systems, while maintaining and considering safety, by trained ICS specific defenders
5. Threat and Environment Manipulation. To make the environment less habitable for the threat, defenders need to know how to change the threat during the attack or change the control system to “fight through the attack.” A threat is defined as a malware capability introduced by a threat actor, or human threat actors abusing legitimate operational software or legitimate protocols with malicious intent to cause
ACDC is best deployed after proper ICS network architecture is completed to enable a dedicated team to spot abnormal network activity compared to what’s “normal” for the ICS environment and ICS protocols.
Join Dean in class in Oslo, In-Person March 28 - April 2 for the massively updated ICS515 class – ICS Visibility, Detection, and Response: https://www.sans.org/cyber-sec...
The course has updated ICS case studies with lessons learned applicable to all ICS sectors and critical infrastructure systems. Each student is provided with an industrial lab kit for us in class and to keep after the class for further learning back at their home or work. The newly updated ICS515 course also has more than 25 hands on technical labs and a full day of ICS NetWars activities to apply the course knowledge to attack and defence scenarios.
Dean Parsons B.SC., GICSP, GRID, CISSP, GSLC, GCIA
Certified SANS ICS Instructor | Critical Infrastructure & ICS Cybersecurity Leader
http://linkedin.com/in/dean-parsons-cybersecurity
1. https://www.sans.org/profiles/dean-parsons/ 2. https://www.youtube.com/watch?v=MkXDSOgLQ6M&ab_channel=PinellasSheriff
3. https://www.dragos.com/wp-cont...


Launched in 1989 as a cooperative for information security thought leadership, it is SANS’ ongoing mission to empower cybersecurity professionals with the practical skills and knowledge they need to make our world a safer place.
Read more about SANS Institute