SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsAI can not only create resources, but also analyze many forms of data

Note: This blog post is the sixth in a series on AI and how to make the most of it in your Security Awareness, Culture, and Human Risk efforts. This post covers how to leverage AI to analyze various resources such as photos, diagrams, spreadsheets, and documents. You can access the other blog posts from this series below.
Up to now we have focused on Generative AI’s ability to create resources, such as videos scripts, newsletter content, translations, generating customized images, and developing learning objectives for training. However, a feature just as powerful if not more powerful is its ability to analyze just about anything you give it. You can upload spreadsheets, word documents, graphs, photos, and diagrams, and it can not only comprehend but then analyze the material, giving you the ability to then improve the content, summarize it, or dive deeper into its meaning. A blog post like this can only begin to scratch the surface of just how powerful this feature is.
The first step is realizing you can pretty much upload anything you want to AI, and it will analyze it like a subject matter expert. Upload a financial document and AI can help you understand it like a Chief Financial Officer. Upload a flow diagram of a proposed application and it can analyze it like a Senior Software Developer. Upload a chart of your home’s energy usage and it can analyze it for you as if you are talking to the Department of Energy. These capabilities are almost frightening! Note, for the purpose of this blog I’m using OpenAI’s ChatGPT.
Now, before we proceed, a word of caution on privacy and security. Keep in mind that most AI solutions are public. This means anything you upload to the AI solution will not only be analyzed, but it will also remember and train itself on that file. This means your information can potentially be shared with others in the future. In some cases, the actual files you upload can be retrieved by others in their original format. This means you should never upload or share anything highly sensitive or confidential. If you want to use AI to analyze sensitive data, instead of using publicly available AI, use a private or enterprise version. This will protect and isolate any information you upload, ensuring that it is never used to train the AI and is not accessible or shared with others. Another option is to anonymize anything you upload.
This answer is any file you want. I’ll provide some examples in this blog post, but you can literally try virtually any file in any format. If it does not work now, try again next month, as AI is advancing rapidly. Here are just several of my favorite examples.
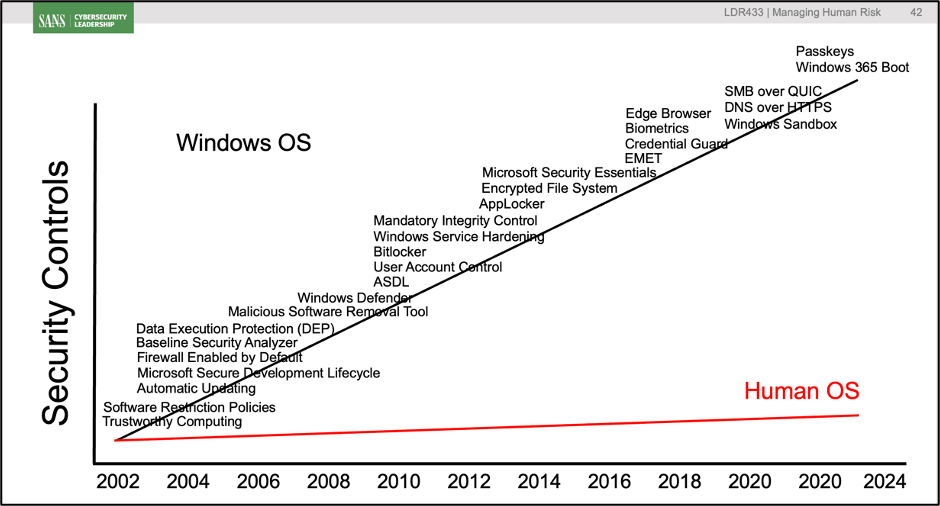
This is one of the most surprising capabilities of AI. You can upload a screenshot of almost anything visual (diagrams, charts, dashboards). For example, I uploaded the screenshot of a slide from the SANS LDR433 Human Risk course, then simply gave ChatGPT the prompt “explain what this slide means” with no other context.
The purpose of the slide is to visually compare just how much we the security community have invested in securing technology vs. securing employees. We do this by visualizing all the different security controls implemented over the past twenty years for the Windows Operating System vs. what the typical security team has done to help secure their workforce (i.e., very little) which we call the Human Operating System. Ever wonder why people are the primary attack vector? Because we have hit the point of diminishing returns by overinvesting in technology and underinvesting in securing people.
What really impressed me is when I uploaded the file, not only did the AI quickly pick up on the diagram’s intent and explain its meaning to me, but it also read, identified, and explained in more depth each of the technical controls listed in the order provided. If I wanted, I could then go in deeper and have AI explain in more detail each of the technical controls. Have a phone or electric bill you don’t understand? Take a screenshot of the part you are confused about, upload it, and have AI walk through the bill with you. Have a child struggling with their biology homework and don’t fully understand the diagram of a cell? Upload a screenshot and you now have your own subject matter expert that can explain it to your child in detail in a simple language that they can understand.
AI can read and analyze just about any text-based document you give it (MS Word Document, PDF, etc.). I find the two biggest benefits for this to be the ability for AI to review a document and provide feedback on how to improve it or summarize it for me. Examples of improving a document include:
Not only can AI provide recommendations on how to improve the wording, it can also increase (or decrease) the grade level at which the document was written, translate the content into another language, or rewrite the wording in a new voice, e.g., “rewrite the document but act like Shakespeare.”
Another powerful feature is AI’s ability to summarize. Perhaps there is a fascinating report on a security breach you want to read about, or a new analysis of the latest in cyber threat actor tactics and techniques, but you simply don’t have time to read the entire document. Or perhaps the document is too technical, and you just want to understand the key points. Provide AI the document (or the link to the document) and it will summarize it for you. It will also summarize a video. If there is a long video on YouTube you want to learn from, but the video is too long, download the transcript from the video, paste the transcript into AI, and have it summarize it for you.
Hate analyzing numbers? Having a hard time figuring out what that spreadsheet means or why the numbers don’t add up? I do all the time. With AI you can have your own personal Chief Financial Officer or Data Scientist do all the work for you. In most cases you can upload the spreadsheet with little to no context, as long as the columns and/or rows are somehow named or described. AI will analyze the spreadsheet and then explain its purpose and what each row or column represents. Then you can begin to ask it questions based on the data, such as the average costs per month or the percentage of increase/decrease over time. It can also help you find anomalies, such as which phishing simulation had the greatest click rates, or which department had the highest phishing simulation report rates.
This one is pretty simple, just upload a picture (any picture) and AI will explain what is happening in the picture. This may sound silly at first, but it can be quite useful. Let’s say you need to replace a part in your car or bike, but you have no idea what the part is called. Upload a picture of it and AI can analyze the image and the part for you. In addition, AI can explain how to replace the part and the tools you will most likely need. Or perhaps there is an amazing cake you would like to make, but you only have a picture of it. Upload the picture of the cake and AI can generate the recipe to make it. Or perhaps you have a picture of a car you like or a plant you would like to grow, but you don’t know the name of it, AI to the rescue! In addition, AI can decode and translate any text in the image, such as a poster written in a foreign language in the background of the picture. Features like these can also be useful for Open-Source Intelligence (OSINT) analysis of images.
We are literally just scratching the surface of what AI can analyze. If you can upload it, AI can handle it. What I’m looking forward to trying out is using AI to analyze future surveys. One of the traditional challenges of using surveys is asking open ended questions. It is extremely difficult to normalize, analyze, and categorize thousands of different responses from thousands of different people, (this is why surveys traditionally use the Likert 1-5 rating scale). With AI, we may be able to ask more open-ended questions and gain far richer data sets and insights into what we want to understand, like with the annual SANS Security Awareness Report.
With all that said, the best way to learn is to try. Remember, you cannot offend or wear out AI. It is happy to try its best to answer any request you send, as many times as you send. And again, be sure you are aware of the sensitivity of the files you upload. For sensitive files, either don’t upload them, sanitize them, or use private/enterprise AI solutions designed to protect the privacy of your data.
Interested in reducing your organization’s human risk? Check out my course LDR521: Security Culture for Leaders and sign up for a FREE course preview here.


Lance revolutionized cyber defense by founding the Honeynet Project. At SANS, he has empowered over 350 organizations worldwide to build resilient security cultures, transforming human risk management into a cornerstone of modern cybersecurity.
Read more about Lance Spitzner