SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsAn introduction to the Purdue Enterprise Reference Architecture (PERA), additional reference models, and best practices for secure ICS architectures.


In Part One of this series, we reviewed the unique lineage of industrial control systems (ICS) and introduced some of the challenges in securing ICS. In Part Two, we will introduce readers to the Purdue Enterprise Reference Architecture (PERA), additional reference models and publications dedicated to ICS cybersecurity, and architectural and administrative best practices for securing these crucially important systems.
In our overview of the “inherently insecure” nature of ICS, we identified the challenge of securing these systems with their high availability requirements and lack of intrinsic security features. Before operators and security practitioners wrestled with these challenges in Operational Technology (OT) environments, Information Technology (IT) administrators faced similar challenges. Administrators of first-generation IT networks addressed the challenge of security first at the perimeter, implementing the first firewall devices to segment their trusted local area network from untrusted wide area networks (and later, the Internet).
Securing ICS requires us to do the same thing: create a defensible environment. In this case, however, the IT/business network component of the organization represents the same untrusted zone to ICS/OT as the Internet represents to the IT network. Once again, segmentation is required, but along what lines? The Purdue Enterprise Reference Architecture helps answer that question.
Created in the early 1990s at Purdue University, the goal of the Purdue Model was to define best practices for the relationship between industrial control systems and business networks (or to use the interchangeable terms, between OT and IT). In its first iteration, there were three components:
Over time, the model grew to include guidance for physical systems architecture and introduced the six network levels of the environment, depicting the systems and technologies that reside at each level:
PURDUE LEVEL | DESCRIPTION | EXAMPLES |
Level 5: Enterprise Networks | Corporate-level services supporting individual business units and users. These systems are usually located in corporate data centres. | Servers providing:
|
Level 4: Business Networks | IT networks for business users at local sites. Connectivity to Enterprise wide area network (WAN) and possibly local Internet access. Direct Internet access should not extend below this level. |
|
IT/OT BOUNDARY (DMZ) | ||
Level 3: Site-Wide Supervisory | Monitoring, supervisory, and operational support for a site or region. |
|
Level 2: Local Supervisory | Monitoring and supervisory control for a single process, cell, line, or distributed control system (DCS) solution. Isolate processes from one another, grouping by function, type, or risk. |
|
Level 1: Local Controllers | Devices and systems to provide automated control of a process, cell, line, or DCS solution. Modern ICS solutions often combine Levels 1 and 0. |
|
Level 0: Field Devices | Sensors and actuators for the cell, line, process, or DCS solution. Often combined with Level 1. |
|
Generally speaking, as you move down the hierarchy (from Level 5 to Level 0), devices have more access to critical processes but fewer intrinsic security capabilities. Devices at lower levels are therefore more reliant on network and architectural defenses, and those found in the upper levels, to protect them.
At this point, it’s important to note that PERA was never intended to be a cybersecurity reference model. It was conceived to depict best practices for managing the segmentation between the enterprise and industrial segments of networks in industrial sectors. Nevertheless, it has remained prevalent as a conceptual framework in IT/OT security because it shows where security measures can be added.
A key aspect of PERA is the boundary point between the ICS/OT systems represented at Levels 0-3 and the IT systems of the enterprise network at Levels 4 and 5. Historically, the way administrators protected the ICS systems was by minimizing, or even eliminating, any interconnects between the two environments. Subsequently, the boundary between OT and IT was often referred to as the “air gap” for architectures in which no interconnect existed between the two. As demands for more data from the OT side have increased, administrators have had to connect these two levels through firewalls that carefully control access with demilitarized zones (DMZs). The firewalls mediate all communication between IT and OT, with the goal of eliminating direct communication between the two environments.
A popular saying in cybersecurity circles is: “all models are wrong, but some are useful.” This certainly applies to the Purdue Model, which undoubtedly has limitations when considering how technology has evolved since the 1990s, prompting business goals and risk tolerances to change as well. As discussed in Part One of this series, technological advances and cost efficiencies have motivated organizations to pull more data from their ICS systems (residing in Levels 0-3 of PERA). For example, remote connections into ICS can lower both operator labour costs and response times. Additionally, information from ICS enables key business functions such as trending, optimization, and billing, helping to drive efficiencies but at the same time increasing ICS exposure to attack.
Some critics contend that PERA envisions the control system network as being separate from everything else, and that the increased demands for real-time OT data and the incorporation of cloud-based systems and services dispels the notion of a completely closed-off system with a rigid hierarchy. An excellent discussion on this topic took place at the 2019 S4 conference featuring Joel Langill and Brad Hegrat, viewable here. The topic of the discussion was “Is the Purdue Model Dead,” and Mr. Hegrat took the position that the Purdue model is essentially dead because “convergence killed it1.” On the other side of the debate, Mr. Langill acknowledged that while “the architecture, from a network perspective, is probably dead,” the model was among the first to show “how these pieces are supposed to be layered and interoperate,” and “if we lose sight of that, we’re going to lose sight of why we created hierarchy in the first place2.” Langill contended that while the model was never conceived as a security reference architecture, it nonetheless incorporates some risk ideas that help security practitioners understand how information flows organizationally and thereby helps identify and address potential attack vectors.
While the presumed “air gap” between IT and OT (between Levels 3 and 4 of the hierarchy) rarely applies to present-day architectures, the core components of industrial environments have not changed; they still include equipment with sensors and actuators connected to controllers that relay their data up a chain of systems in the organization. Additionally, while the advent of Cloud technologies may blur the lines geographically, the Purdue Model always segmented networks by function, which can still be applied to OT/IT environments with significant Cloud integration.
Both sides of the debate make valid points, but the consensus at the SANS Institute is that PERA remains a useful conceptual framework because it was among the first to classify control system components according to a well-defined taxonomy. Even if its hierarchical layers can no longer be uniformly applied to modern architectures, sorting ICS and IT devices and systems into distinct functional layers helps administrators and security practitioners determine where to apply security measures effectively.
The SANS ICS410 Reference Model
Expanding on the Purdue Model and some of the ICS cybersecurity frameworks that we will discuss in the next section, SANS created the ICS410 Reference Model for ICS410: ICS/SCADA Security Essentials. The ICS410 model is a publicly available, foundational reference architecture that adds explicit enforcement boundaries to the Purdue Model, helping to situate ICS devices and cybersecurity controls in a secure network architecture.
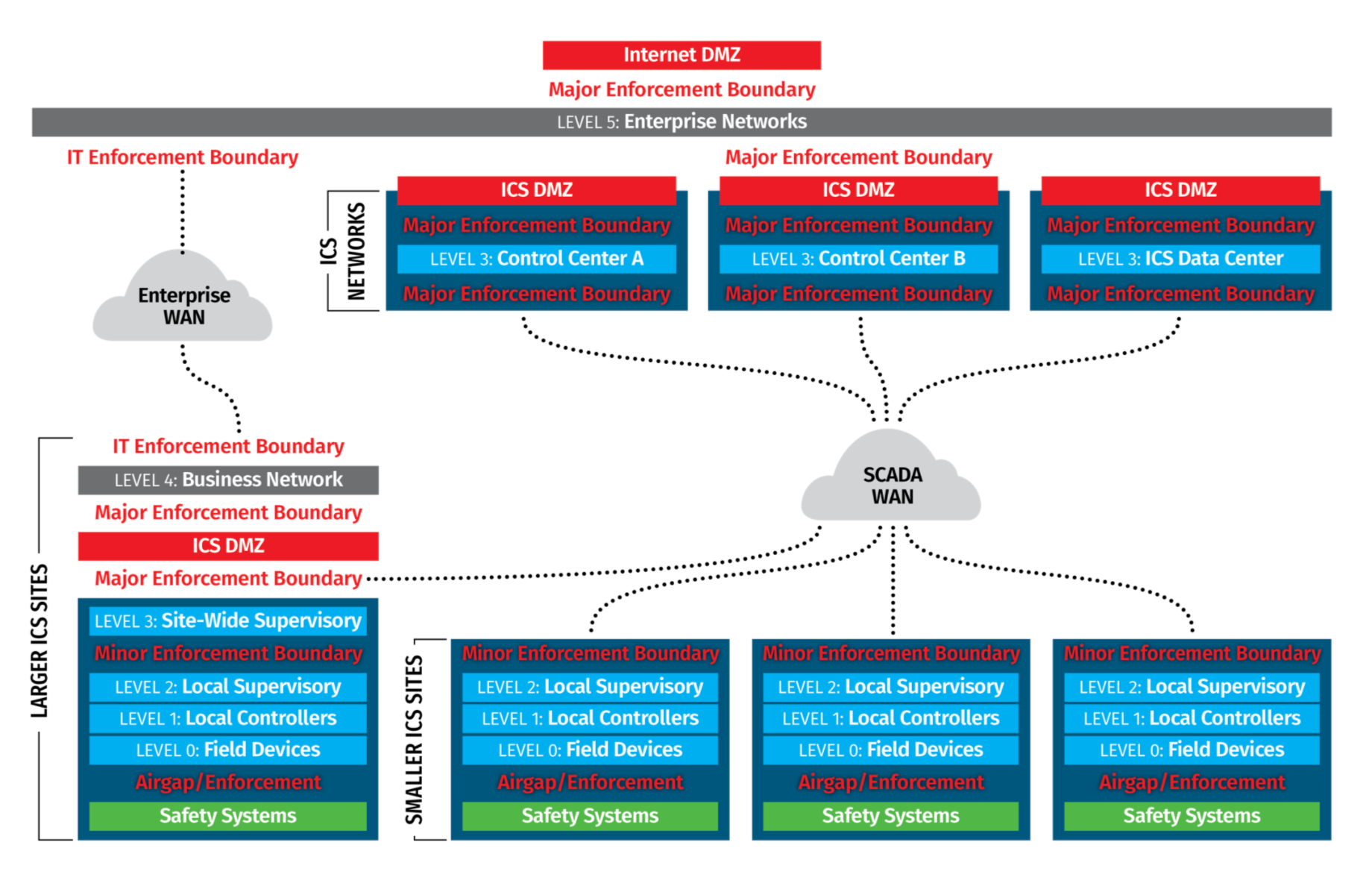
In general, the ICS410 Reference Model offers the following advantages:
The ICS Reference Model also offers more details on the enforcement boundaries between network segments by:
Finally, the ICS410 Reference Model offers clear guidance for securing remote access, a critical capability.
As with other frameworks and reference models, the ICS410 Reference Model will require updates to accommodate the new devices and communication paths necessitated by increasing cloud connectivity and additional IIoT devices in ICS networks.
If PERA laid the foundation for ICS cybersecurity with effective taxonomy and classification, then a series of other frameworks and publications have built upon that foundation with guidance specifically geared toward securing industrial control systems. Examples include:
Along with industry specific guidance in:
Published by the National Institute of Standards and Technology (NIST), the NIST CSF is central to much of the U.S. government’s guidance for critical infrastructure protection. This is evinced in the NIST CSF’s formal title: “Framework for Improving Critical Infrastructure Cybersecurity.” Similarly, the TSA provides guidance for pipeline operators using categories aligned to the CSF3.
The influence of the Purdue model on these guidelines and publications is evident in how they all promote effective segmentation and segregation of systems in the industrial network environment and require security controls at the boundaries between them. NIST 800-82, for example, articulates this concept as follows:
The standards cited here all share many core concepts including:
In our final section, we will expand on some of these concepts and examine how to convert these guiding tenets into specific administrative tasks.
As we discussed in Part One of this series, it can be difficult to secure ICS networks for many reasons including the need for continuous and deterministic operations, interoperability in multi-vendor environments, the variety and age of devices, and their lack of intrinsic security capabilities. As a result of these constraints, the best opportunity to secure ICS environments is with strong architectural defenses which start at the network layer and feature prominently in the guidance provided by the standards and frameworks mentioned above.
A strong network architecture improves ICS security and provides a foundation on which additional security measures can be implemented over time. The Purdue Model, NIST SP800-82, IEC 62443, and the SANS ICS410 Reference Model all place a heavy emphasis on network segmentation and the control of communication between segments.
Just as perimeter firewalls are universally deployed to protect enterprise environments from internet-based attacks, ICS environments should have protection at their many enforcement boundaries. Although industrial processes are at lower levels in the Purdue Model, the most sensitive data and points of control are typically at Level 3, which is also where most attackers first access the ICS network from the business network.
Fundamentally, ICS systems should use dedicated infrastructure that is completely independent of the business network. With effective segmentation in place, a firewall between Levels 3 and 4 can control network communication into and out of the ICS network. This firewall should block all communication in and out of the ICS network and explicitly permit only the minimum required communication.
Attacks can also originate from remote sites, especially in widely distributed environments. For this reason, a secondary enforcement boundary should be configured between Levels 2 and 3 to protect management systems from attacks from the field, and to protect individual field sites from each other. These enforcement boundaries are often implemented using router access-lists to avoid having critical process communication pass through firewalls that could impede legitimate communication.
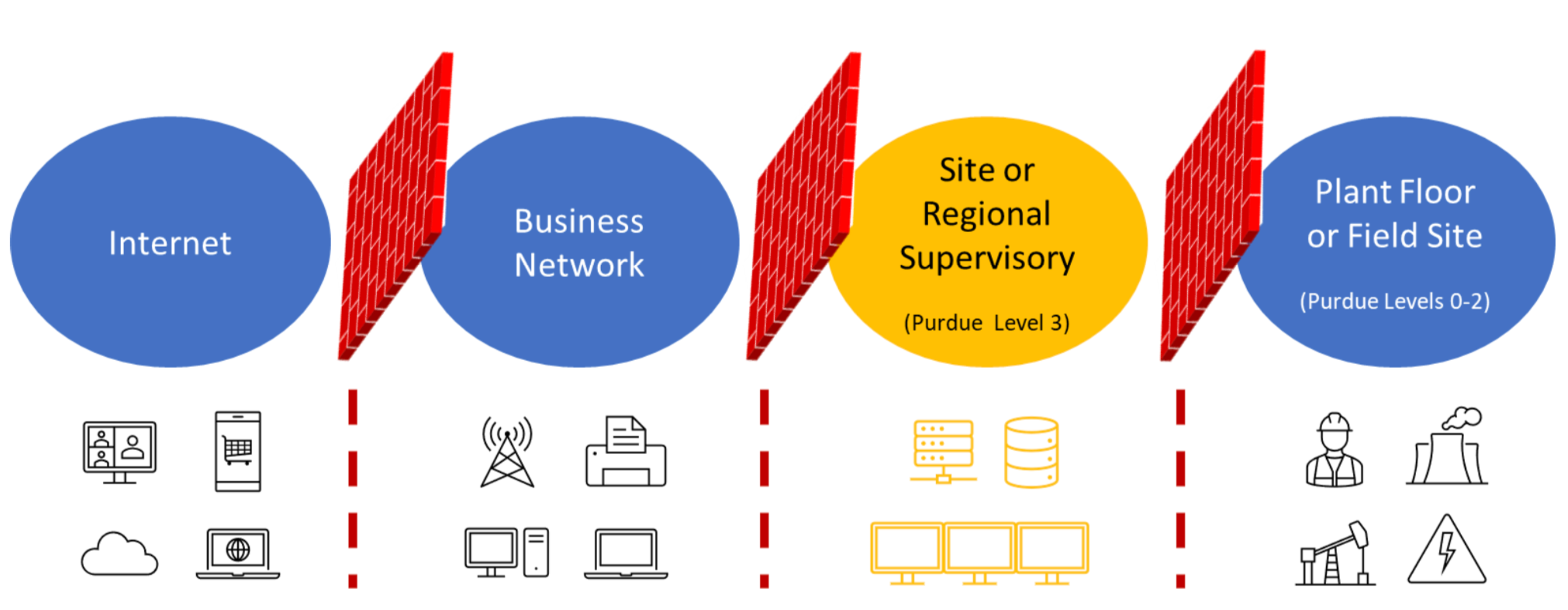
There are many different types of systems required for full functionality of an ICS network including operator workstations, HMIs, engineering workstations, management servers, database servers, historians, alarm servers, and many other specialized systems. Each system has a well-defined role and requires specific network access to other systems. Therefore, each level should be further segmented into multiple networks where systems with common roles can reside with an enforcement boundary controlling their communication with the rest of the network.
Multiple DMZs, each with a dedicated purpose, should be created to facilitate communication between the ICS network and the business network. Remote access, cloud access, and Internet access can also be mediated through dedicated DMZs. The implementation and configuration of DMZs will be explored in more detail in a future blog post.
Not only do enforcement boundaries control the communication between different classes of systems, but they also serve as natural network “choke points” where network traffic can be monitored and saved for later analysis. The logs generated by firewalls, combined with raw packets captured from the network, are a rich source of information. Since ICS networks are relatively static, a baseline of “normal” communication can be created and then used to detect anomalies and threats.
A detailed break-down of a complete network architecture is beyond the scope of this blog, however there are several important best practices to follow:
As more and more vendors leverage cloud-based management systems, practitioners need to evolve their ICS architectures. Devices that must communicate with the Cloud should be placed in separate, dedicated zones that restrict their network access to only their cloud-based controllers and the on-premises systems that they must communicate with.
The guidance offered here presents only a fraction of ICS cybersecurity best practices. There are several controls beyond architecture standards for security practitioners to consider as well, and with new functionality demands and new technologies continuously entering the equation, the field of ICS cybersecurity will keep evolving. Nevertheless, the venerable Purdue Model has stood the test of time, offering ideas about risk and a common vocabulary that inform many of the publications and models gaining traction today.
As our series on ICS cybersecurity continues, we’ll delve deeper into specific security measures including best practices for implementing and configuring demilitarized zones at enforcement boundaries.
Glossary of Terms
Customer Relationship Management (CRM) | A CRM system is a central repository in which businesses can store customer and prospect data, track customer interactions, and share this information with colleagues. It allows businesses to manage relationships with customers, thereby helping the businesses grow. |
Security Operations Center (SOC) | A dedicated, centralized site where enterprise information systems (web sites, applications, databases, data centers and servers, networks, desktops, and other endpoints) are monitored, assessed, and defended. |
Human-Machine Interface (HMI) | A Human-Machine Interface (HMI) is a feature or component of a certain device or software application that enables humans to engage and interact with machines. In ICS, HMIs are typically screens or touchscreens that connect users to machines, systems, or devices. |
Programmable Logic Controller (PLC) | A solid-state control system that has a user-programmable memory for storing instructions for the purpose of implementing specific functions such as I/O control, logic, timing, counting, three mode (PID) control, communication, arithmetic, and data and file processing. |
Remote Terminal Units (RTU) | Typically deployed in industrial environments, a remote terminal unit (RTU) is a multipurpose device used for remote monitoring and control of various devices and systems for automation. It serves a similar purpose to programmable logic circuits (PLCs) but to a higher degree. An RTU is considered a self-contained computer because it shares the same core components: a processor, memory, and storage. Subsequently, it can be used as an intelligent controller or master controller for other devices that, together, automate an industrial process. |
Intelligent Electronic Device (IED) | Found everywhere industrial control systems such as such as supervisory control and data acquisition (SCADA) or distributed control systems (DCS) are used, IEDs are devices added to ICS to enable advanced power automation. IEDs are a part of the power regulation used in many industrial processes like control circuit breakers, capacitor bank switches and voltage regulators. These settings are controlled by way of a settings file. The creation and testing of the file are part of the largest tasks involved in IEDs. |
Industrial Internet-of-Things (IIoT) | The sensors, instruments, machines, and other devices that are networked together and use Internet connectivity to enhance industrial and manufacturing business processes and applications. |
Sources
1 Peterson, Dale. Unsolicited Response Podcast: Is the Purdue Model Dead (S4 2019 Main Stage Panel Discussion). https://dale-peterson.com/2019/02/11/is-the-purdue-model-dead/. February 11, 2019.
2 Peterson, Dale. Unsolicited Response Podcast: Is the Purdue Model Dead (S4 2019 Main Stage Panel Discussion). https://dale-peterson.com/2019/02/11/is-the-purdue-model-dead/. February 11, 2019.
3 As a result of the ransomware incident suffered by Colonial Pipeline, the TSA issued Security Directive Pipeline-2021-01 requiring pipeline owner/operators to assess their current practices against the guidelines, identify gaps and remediation measures, and report these to the TSA.
4 Stouffer, Keith; Falco, Joe; Scarfone, Karen; Special Publication 800-82: Guide to Industrial Control Systems (ICS) Security, National Institute of Standards and Technology (NIST), U.S. Department of Commerce, June 2011.
Introduction to ICS Security Series:
Read Part 1 here.
Read Part 3 here.
Check out Stephen's bio, ICS contributions, and upcoming ICS410 course teaches here.
Learn more about SANS ICS410: ICS/SCADA Security Essentials course here


With more than 25 years of experience in IT and OT security, Stephen Matezar has led major security initiatives, including the re-architecting of OT networks for a multi-billion-dollar oil and gas company.
Read more about Stephen Mathezer