SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsThis blog post series offers a primer on continuous adversary emulation.

With this blog post series, I am excited to share my personal experiences and insights related to the intriguing concept of adversary simulation. Additionally, I will delve into practical applications of adversary simulation within your organization. Join me as we explore the fascinating realm of cyber security and discover how this approach can enhance your defensive strategies.
Last year, I had the privilege of developing the SANS course SEC598. Within this comprehensive course, a significant portion is dedicated to the exploration of adversary emulation and its practical implementation. It was an enlightening journey that expanded my understanding of this powerful technique and its potential benefits.
In the ever-evolving landscape of cybersecurity, organizations face an increasing need to proactively assess their defenses against advanced threats. Adversary emulation has emerged as a powerful technique to simulate real-world cyberattacks and evaluate an organization's security posture.
Adversary emulation has emerged as a powerful technique to simulate real-world cyberattacks and evaluate an organization's security posture.
Adversary emulation and penetration testing are two distinct approaches used in the field of cybersecurity to evaluate the security of an organization's systems and infrastructure. While they share similarities, there are key differences between the two methodologies:
Let’s try to see what are some of the key differences between adversary emulation and penetration testing:
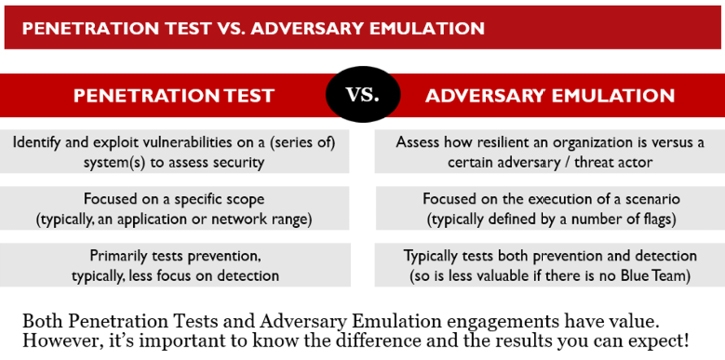
Both adversary emulation and penetration testing play crucial roles in assessing an organization's security posture. Adversary emulation provides a broader understanding of potential attack vectors and behaviors, while penetration testing offers targeted insights into specific vulnerabilities. By combining these approaches, organizations can strengthen their overall security defenses and better prepare for real-world cyber threats. Both have their own objectives and are beneficial toward improving your security posture. The focus of this blog post series is automation for offensive techniques; this is naturally more linked with adversary emulation and how you leverage automation to continuously assess your defenses against real-world threat actors.
When considering adversary emulation, it is often associated with mimicking specific adversaries and their tactics and techniques. However, conducting adversary emulation in a continuous manner requires a more systematic approach.
To begin, it is important to define the objectives and goals of your adversary emulation program. Determine what you want to achieve, whether it is enhancing incident response capabilities, identifying vulnerabilities, or testing the effectiveness of security controls.
An effective use of adversary emulation also involves understanding the threat landscape that is specific to your industry and organization. Research and analyze the tactics, techniques, and procedures employed by real-world threat actors who target organizations similar to yours. This understanding will aid in designing realistic and relevant adversary emulation scenarios.
Identify specific attack scenarios that align with your organization's risk profile and priorities. Consider different types of adversaries and the methods they are likely to use when attempting to compromise your systems. These scenarios should be tailored to reflect the real-world threats faced by your organization.
To support your efforts, there are valuable online resources available. For instance, the SANS Purple Concepts poster released in 2022 provides insights into known adversaries and how to emulate their techniques.
Another useful and very well-known resource within the cyber security world is MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge). It is a globally recognized framework that provides a comprehensive and structured knowledge base of adversary tactics and techniques. It offers a standardized way to describe and categorize the behaviors and actions of threat actors during different stages of an attack. The MITRE ATT&CK framework is organized into matrices that represent various platforms and environments, such as enterprise, mobile, and cloud. Each matrix consists of multiple techniques that adversaries may employ to achieve their objectives. Techniques are further categorized into tactics that represent the broader goals of an attacker. MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) is a globally recognized framework that provides a comprehensive and structured knowledge base of adversary tactics and techniques. It offers a standardized way to describe and categorize the behaviors and actions of threat actors during different stages of an attack.
The MITRE ATT&CK framework is organized into matrices that represent various platforms and environments, such as enterprise, mobile, and cloud. Each matrix consists of multiple techniques that adversaries may employ to achieve their objectives. Techniques are further categorized into tactics that represent the broader goals of an attacker.
Another useful resource is the Center for Threat Informed Defense GitHub repository, which offers plans for emulating advanced persistent threats (APTs) and micro-emulation plans for common techniques.
Once you have identified relevant threats, you can begin creating playbooks or scripts that outline the step-by-step actions to be performed during adversary emulation exercises. These playbooks should include the necessary tools, techniques, and procedures to simulate the chosen attack scenarios. At NVISO, we have developed playbooks that enable us to easily rerun specific simulations, validating the effectiveness of defenses and assessing how changes in the environment impact prevention and detection capabilities for various adversaries.
All resources mentioned above are also being covered in the SANS SEC598 course, we will start with explaining some example of techniques, how they are being used by adversaries, and how you can simulate a certain threat. Several labs are included to write your own playbook, or stay tuned and use some of the tools we will discuss in the next series of our blogpost. One of the tools will be how to setup MITRE Caldera and how you can simulate standard adversaries but also techniques with customized payloads.
This post is an introduction to continuous adversary emulation. It is important to define objectives and understanding the specific threat landscape to conduct effective adversary emulation exercises. By tailoring attack scenarios to align with organizational risks and leveraging resources like the SANS Purple Concepts poster and MITRE ATT&CK framework, organizations can develop realistic simulations and playbooks. These playbooks enable the systematic replication of real-world threats, enhancing defenses and assessing the effectiveness of security measures.
The upcoming blog posts in this series will delve further into techniques, tools, and automation, including the setup of MITRE Caldera and customization of payloads. By embracing adversary emulation and leveraging these resources, organizations can continuously assess and improve their security posture, staying ahead of evolving threats in the dynamic cybersecurity landscape.


Jeroen is the security architecture team lead and incident manager at NVISO where he specializes in security architecture, cloud security, and continuous security monitoring.
Read more about Jeroen Vandeleur