SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsThe SEC502 course doesn’t just refresh the content, it transforms how learners build cloud security skills.

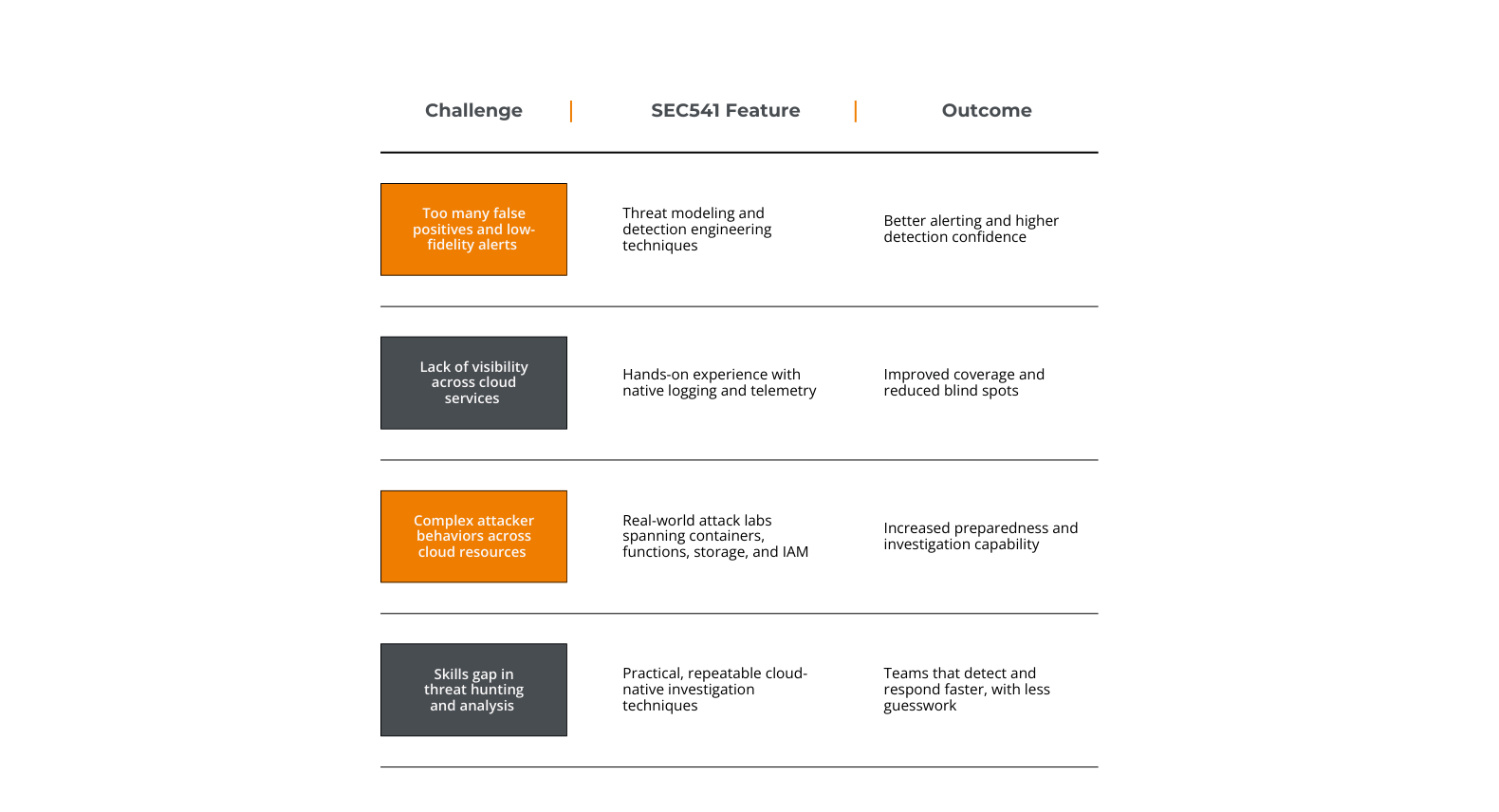
Cloud detection isn't just about spotting alerts, it's about understanding attacker behavior, building meaningful detections, and responding with speed and clarity. As cloud environments continue to grow and evolve, so must our methods for securing them. That's why we've updated the SEC541 course, equipping you with the latest techniques and tools to defend against modern cloud threats.
The newly enhanced SEC541: Cloud Security Threat Detection course is designed to help defenders meet new challenges head-on. Whether you're a blue teamer, detection engineer, or cloud security architect, the SEC541 course now offers deeper insight, more advanced detection strategies, and a practical framework to level up your visibility and response.
This isn't a minor content refresh. We added modern attack techniques, introduced more advanced tools for detection and investigation, and expanded the training to show you how to build and mature your own detection engineering program.
You won’t just write detection rules; you’ll build a complete cloud detection engineering program. You’ll learn to:
From designing a strategic plan to deploying detections in CloudTrail, KQL, or GuardDuty, this course delivers practical, applicable skills.
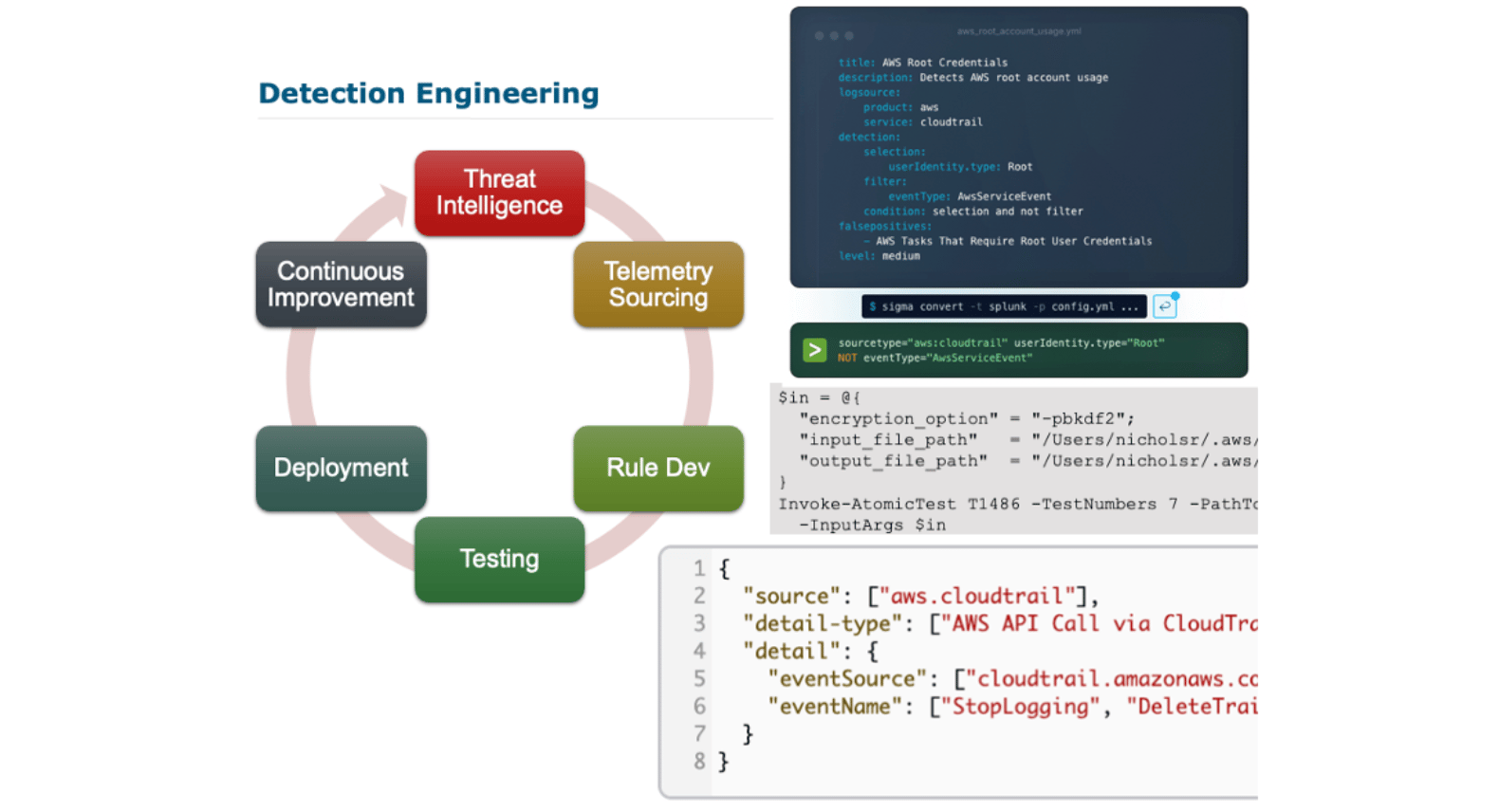
“We added structure and maturity to the detection process. Students leave this course understanding how to build detections that matter—and how to prove they work.” — Shaun McCullough, SEC541 Lead Author
We’ve updated our case studies and attack chains to reflect what defenders are encountering right now in the wild:
You'll investigate attacker activity across identity, storage, compute, and control planes—and hunt them across logs, alerts, and behaviors.
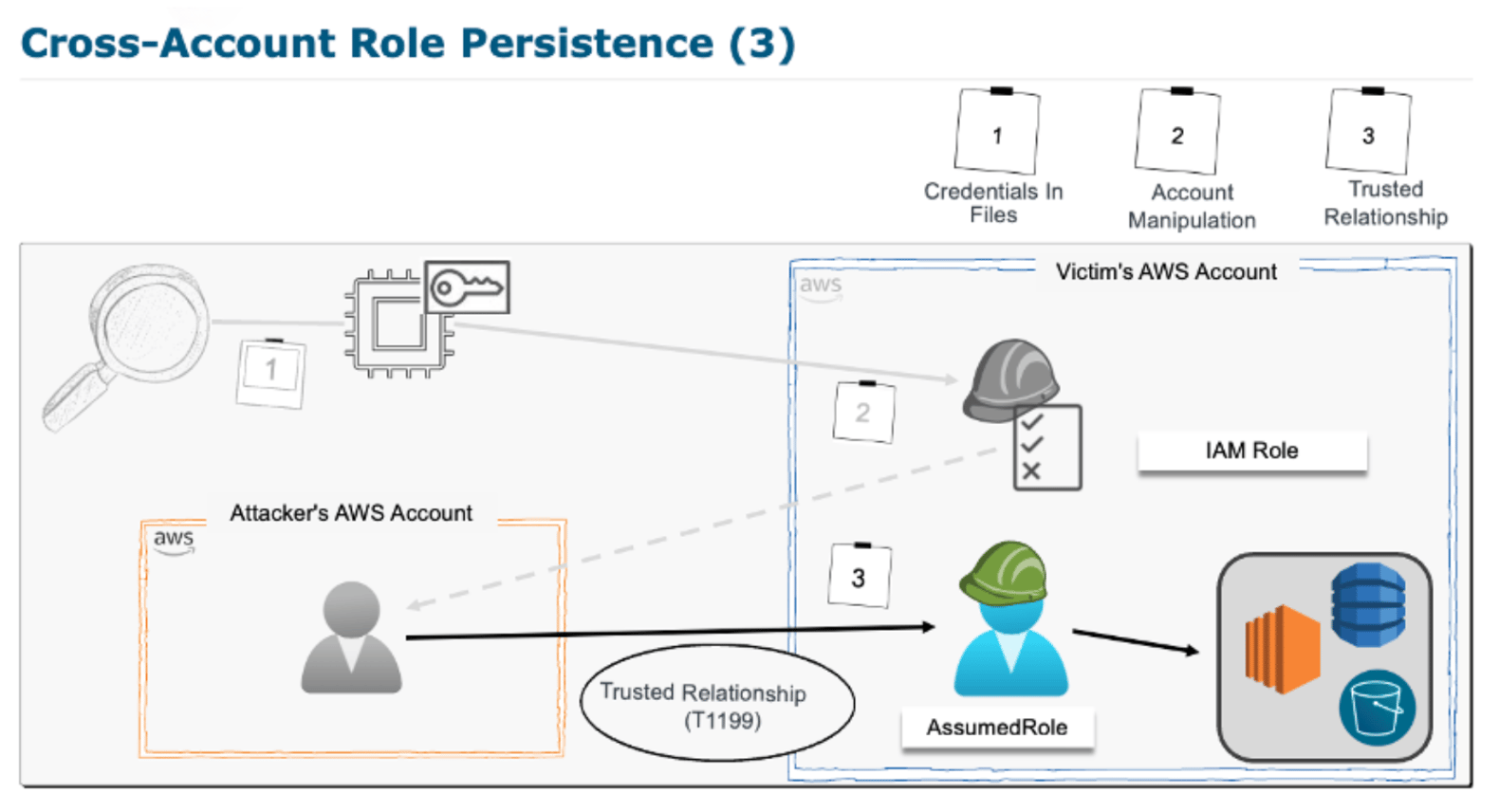
The SEC541 course includes 22 hands-on labs in live cloud environments, where you'll use tools like:
Whether you’re deploying decoys, enriching alerts, or running investigations, this course teaches you how to build a real detection toolkit.
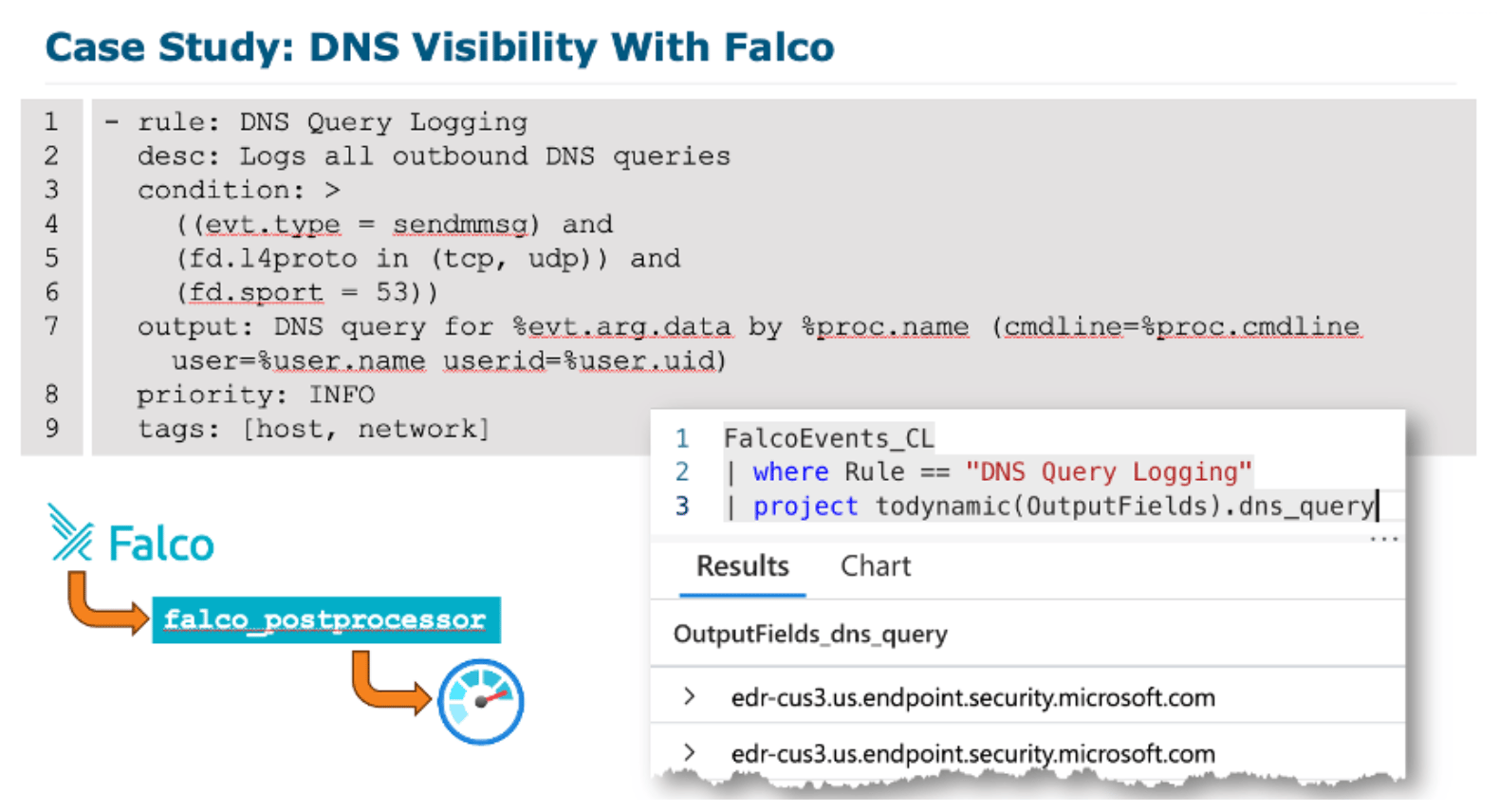
The SEC541 course is built for defenders who need to move beyond security information and event (SIEM) dashboards and into the details of cloud adversary behavior.
You’ll perform:
“Class instruction was easy to follow and provided the right amount of detail. It was clear how each lab and section related to our purpose and the big picture.” — Antoinette Bongiorno, FM Global
The threats have changed; so, has this course. Explore the Updated Course or Register Now.
The SEC541 course is a cornerstone in two SANS Cloud Security Journeys:
These learning paths guide professionals through the essential skills, tools, and knowledge areas needed to specialize in defending cloud environments. Whether you're focused on cloud forensics, detection engineering, or advanced SOC operations, the SEC541 course provides the depth, strategy, and hands-on learning to advance your career.


Shaun McCullough spent 20+ years at the NSA working in cyber operations as a software engineer and technical director of Blue, Red, and Hunt teams. He is currently a staff level Cloud Security Engineer at GitHub.
Read more about Shaun McCullough