SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsThe Dark Web's anonymity attracts a variety of users. Explore the various techniques used to identify the individuals behind these sites and personas.

On April 5, 2023, the FBI and Dutch National Police announced the takedown of Genesis Market, one of the largest dark web marketplaces. The operation, dubbed "Operation Cookie Monster," resulted in the arrest of 119 people and the seizure of over $1 million in cryptocurrency. You can read the FBI’s Warrant here for details specific to this case, but it seemed like a good opportunity to write about how OSINT Tools can assist with dark web investigations.
The Dark Web's anonymity attracts a variety of users, from whistleblowers and political activists to cybercriminals and terrorists. When attempting to identify the individuals behind these sites and personas, various techniques are used.
While not considered OSINT, there have been instances when technical vulnerabilities have existed in the technology used to host dark websites. These vulnerabilities may exist in the software itself or be due to misconfigurations, but they can sometimes reveal the site’s true IP address. Often these require pen-testing tools and techniques such as using Burp Suite to induce error messages containing the site’s true IP address. Vulnerabilities such as these are uncommon and rarely utilized.
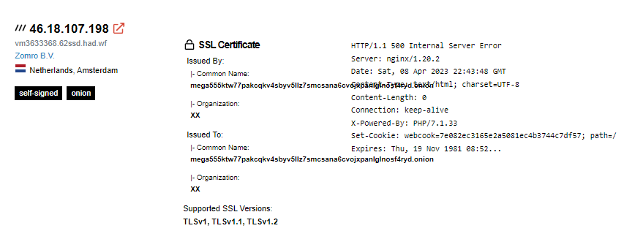
There have also been instances when dark website operators have used SSL certs or SSH keys, which can be tied to their true IP address using services like Shodan or Censys.
Transactions on the dark web often involve cryptocurrency in exchange for illegal goods and services. This opens up the possibility of identifying individuals with the help of blockchain analysis tools.
I can’t go to the bank and open an account using the name “anonymous” due to laws designed to prevent money laundering. These requirements are often referred to as “Anti Money Laundering & Know Your Customer” or AML/KYC and require customers to provide government-issued IDs to prove their identity. Many countries have put similar requirements on cryptocurrency exchanges as well.
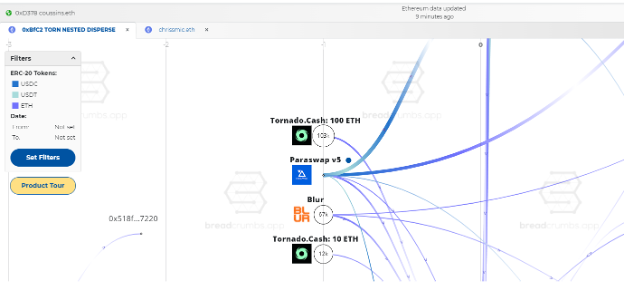
For several years, companies have provided blockchain analysis tools that attempt to tie cryptocurrency addresses to specific exchanges, such as Coinbase or Binance. Once a cryptocurrency address is tied to a specific exchange, law enforcement and/or financial investigators with legal authority can request that the exchange provide them with the identifying information for the owner of that account.
Historically these blockchain analysis services have been cost-prohibitive for individuals to purchase, but recently, a site called Breadcrumbs was launched at https://www.breadcrumbs.app/, which provides much more affordable prices, including a free plan.
In my SANS SEC497 Practical OSINT course, we discuss the dark web on the afternoon of Day 5. That placement was on purpose; I’ll explain why in this section.
Imagine you run a food truck constantly forced to change locations due to a city ordinance that you can never be in the same spot more than twice a month. How would you try to build brand loyalty and let prospective customers know where you were located that day??
You would likely try to get customers to connect with you on Facebook, follow you on Twitter, visit your website, etc., so they can know where to find you. Believe it or not, there is a very similar dynamic on the dark web.
What the dark web provides in anonymity, it lacks stability and security. Major markets such as Silk Road, AlphaBay, Hansa, Wall Street, and now Genesis have all been taken down by law enforcement. Denial of Service attacks have become a major problem on the Tor network, as evidenced by the popular “Dread” forum recently being down for several months due to such attacks. Can you imagine trying to run a business and achieve a stable income in that environment?
One way that sellers try to achieve stability and resiliency is to sell on multiple marketplaces and to provide methods to contact them directly. This makes a lot of sense but is incredibly useful for OSINT practitioners since now we have these contact methods, or “selectors,” which we can use to find them on the internet and bring all of our knowledge, experience, and resources to bear. Look at the example below where we’re able to take an email address from a dark website and tie it to a site on the internet using Google.
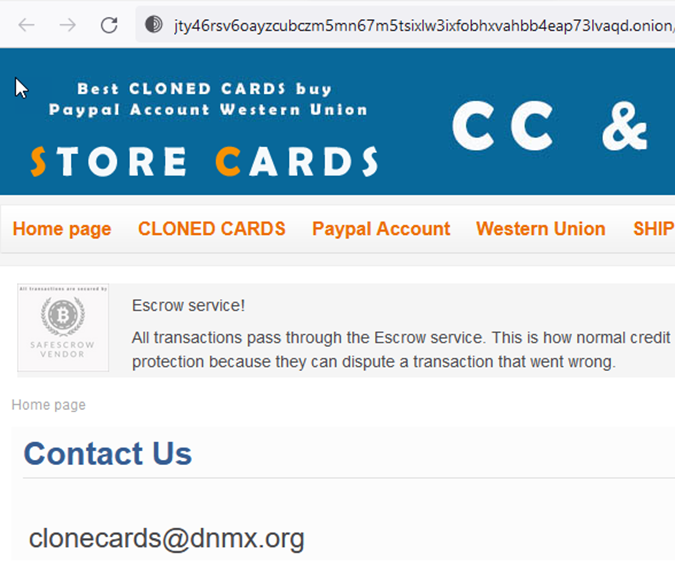
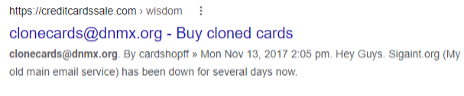
Once we’ve tied the individual(s) to resources on the internet, we have numerous options to deanonymize them. Some of my favorite options include:
Domain registration information, such as WHOIS records, can provide helpful information about the owner or operator of a website. In some cases, criminals may inadvertently expose their identity or location using inaccurate or incomplete privacy protection measures. Even if the WHOIS information for a site is currently anonymous, oftentimes, there was a point in the past when it was not. I’ve seen gaps as small as four days where a site privately registered before and after gave away its owner’s true identity.
Individuals in this space often participate in forums to communicate, answer questions, etc. They may inadvertently reveal information that can help OSINT practitioners learn more about their true identities. The language they use or unique sayings can be extremely useful.
Even if an email is tied to an anonymous service, the user may have used it on other sites, including forums and social media. If you’re legally and morally able to use breach data in your investigations, you may be able to tie an online persona to a real name, physical address, etc.
An example of a leak that has proven helpful for some investigators was the 2021/2022 leak of 10GB of data from several VPN providers, including SuperVPN, GeckoVPN, and ChatVPN. This data contained full names, billing details, and potentially unique identifiers about the devices used, including the IMSI of mobile devices.
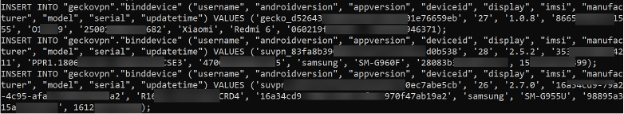
These topics and numerous others are covered in the SEC497 course before the dark web so students can easily understand the options we have once we bring a selector acquired on the dark web back to the internet.
Future dark web market takedowns will use the methods discussed here but will no doubt incorporate some emerging technologies. The most obvious development is using Artificial Intelligence (AI) and Machine Learning (ML) in OSINT.
For example, AI can help build web scraping tools that can quickly gather and analyze data from multiple sources, while ML algorithms can be trained to identify patterns and relationships in the data. These advancements have the potential to save investigators significant time and resources, allowing them to focus on other aspects of their investigations.


Matt Edmonson, Senior SANS Instructor, STI faculty, and Founder of Argelius Labs, authored SEC497 and SEC587. An industry veteran with 11 GIAC certifications and OSCP, he draws on 20 years of investigations to deliver accessibly, real-world OSINT training.
Read more about Matt Edmondson