Volume Shadow Copies (VSCs) can contain a treasure trove of information - so much information that if not treated correctly, they can become too cumbersome for many investigators. (Note: if you are unfamiliar with VSCs, Rob Lee has a great write-up about the subject.) One way to make the examination of VSCs a little less burdensome is by automating the process. After all, no one wants to get a 1 TB Vista image and find that it has 30 or more VSCs that need examined.
To begin, you need to figure out what VSCs are on the system. Harlan Carvey's blog post talks a lot about how to access these areas. For me, I have EnCase's PDE module available, so I use that to mount my forensic image as a physical disk on my Windows 7 forensic machine. From there, open a DOS command prompt with administrator rights so that you can find out what VSCs are in the forensic image.
C:\>vssadmin list shadows /for=M: > "C:\VSC_Exam\VSCs.txt"
This command sends the output to a text file on your forensic machine. The default output is to your screen, so if you want to leave it as the default, just eliminate the ">" and everything after it. M: is the drive letter that has been assigned to the mounted forensic image. Change M: to the appropriate drive letter of your mounted image.
After seeing how many VSCs are in the forensic image, a batch file is created to mount every VSC as a symbolic link. The command to mount each VSC is:
C:\>mklink /d "C:\VSC_Exam\Mounted_VSCs\Shadow7" \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy7\
You can find the path of the VSC (\\?\GLOBALROOT\...Copy7\) from the VSCs.txt file that was created in the previous step (see the screenshot below). The path has been outlined in red.
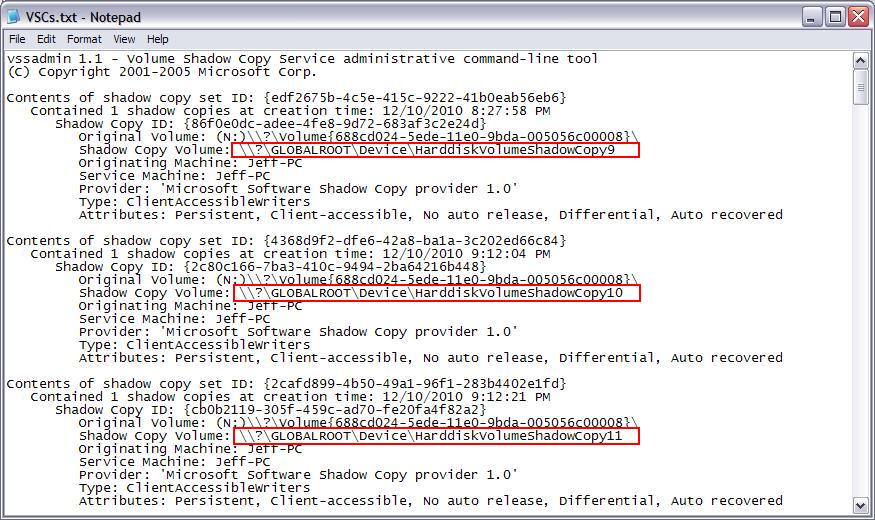
Replace Shadow7 and HarddiskVolumeShadowCopy7 (from the example command) with the appropriate VSC number. The trailing \ in the VSC path is important. Without it, you will not have the proper permissions to access the files within the VSC.
Now that the VSCs have been mounted as symbolic links, how do you know what is in the VSC without browsing through the folders? Easy. LogParser will allow you to grab the metadata for all the files within each VSC and export the metadata to CSV. The LogParser command to do this is:
C:\>logparser -i:FS -o:CSV -preserveLastAccTime:ON "Select HASHMD5_FILE(Path),CreationTime,LastWriteTime,LastAccessTime,Name,Path,Size into 'C:\VSC_Exam\LogParser\Shadow7.csv' From 'C:\VSC_Exam\Mounted_VSCs\Shadow7\*.*'"
The "-i:FS" option is the input type for LogParser. In this case, it is a file system. The "-o:CSV" is an output type of CSV. By default, LogParser will not keep the last accessed time of the folders and files that it touches, so I use "-preserveLastAccTime:ON" to keep these times intact. The other items that I collect are the MD5 hash of the file, creation date and time, last written date and time, last accessed date and time, name of the file, path of the file, and the size of the file.
From here, you can import the CSV for each VSC into MS Access (or the database of your choice) and run queries against the data. Having the exact file paths for every file will allow you to create additional batch files for exporting any files you may need, running RegRipper (rip.exe) against the registry files, or giving you peace of mind for just knowing what is in each VSC.
The last step, after you are finished with the VSCs, is to unmount them. Again, creating a batch file makes this much simpler. The command to unmount each VSC is:
C:\>rmdir "C:\VSC_Exam\Mounted_VSCs\Shadow7\"
LogParser tends to make analysis a little easier for examiners who are unfamiliar with what may or may not be inside a Volume Shadow Copy. Having a directory structure available - complete with dates and times, names and sizes of files, and MD5 hashes - can be very beneficial for setting up a game plan for the remainder of the VSC analysis. Remember, it is all about working smarter, not working harder.
Stacey Edwards is a forensic analyst at Vestige, Ltd. She has earned her GCFA and is a member of the Association of Certified Fraud Examiners (ACFE). Her forensic interests are in Fraud cases and dabbling in the development of EnScripts.




