SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact Us
Welcome to part two of my FTK v3 review. If you have not read the first post, it can be found here. Forensic suites are notoriously difficult to review because of the sheer number of features they include. We are lucky within the computer forensic community to have multiple vendors operating in a highly competitive environment. As such, the core forensic suites continue to add functionality. I have chosen to highlight a few of the new(er) features within Access Data's Forensic Toolkit (FTK). I interact with a lot of folks who are building forensic capabilities within their organizations, often with a limited budget. With the new additions to FTK, I find myself recommending it more and more. For the typical forensic shop it really does have a lot of bang for the buck. Here are two additional "value-adds" that I didn't have room to cover in my first post:
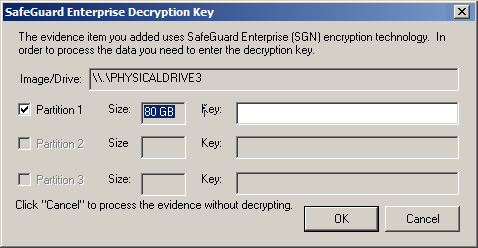
With more and more organizations mandating full disk encryption (FDE), a new headache has emerged for corporate forensicators. One quick and easy option is to image the encrypted disk and decrypt via your forensic suite. While this may have a performance penalty (if you have metrics please share!), it provides some nice benefits like leaving the drive encrypted for transport purposes and simplifying acquisition. FTK v3 added support for a few new vendors and now decrypts Utimaco Safeguard, McAfee Safeboot, PGP, Symantec Guardian Edge, as well as file-specific encryption technologies from Credant and Microsoft Encrypted Filesystem (EFS). One notable absence in this group is Microsoft Bitlocker which is making a big play for the enterprise. I was pleasantly surprised at how easy the identification and decryption process was and that support extended not only to image files but also to physical disks added to a case. In the latter example, I utilized a write-blocker to preview a drive with FDE and was able to use FTK to decrypt it on the fly.
Memory analysis is no longer a niche and is unfortunately not being included in as many exams as it probably should be. FTK now includes a "Volatile" tab, which integrates memory analysis into the GUI. This initial effort isn't likely to replace dedicated tools like Mandiant Memoryze, but allowing memory analysis to take place together with other host-based evidence moves it further along into the mainstream and leverages some interesting parts of the forensic suite.
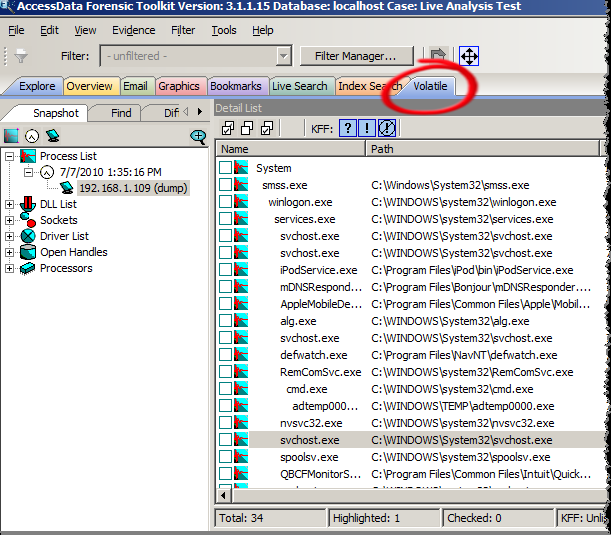
FTK will parse out the usual suspects from the memory image, providing information on running processes, sockets, drivers, and open handles. Each process can be drilled into to see its associated DLLs, network connections, and handles. Processes can also be extracted from the memory image for offline analysis. Where things get really interesting is when you consider the advantages of employing all of the other tools in the suite. File carving, string searching (with hits tied to a specific running process), fuzzy hashing, and dumping strings in memory to feed into a password cracking dictionary are all possible within the FTK interface.
With this first release, it feels like memory analysis is not completely baked into the product, impacting the expected workflow. A few examples include the inability to bookmark memory artifacts, memory search not leveraging FTK's indexing capabilities, and the requirement to add the memory image into the case twice to perform actions like file carving (once to parse processes for the Volatile tab and once to have the image recognized as an evidence file). That being said, it is an exciting addition, and the marriage of memory and host-based evidence analysis in one product puts FTK ahead of the curve. For you EnCase fans, it should be noted that Takahiro Haruyama has built a set of third-party Enscripts to perform some similar memory analysis tasks in that platform.
With FTK version 3, Access Data has justified the sweeping product changes they started in version 2. The console is intuitive and responsive; case management is well integrated into the back-end database; and with quad-core processors the norm, the hardware requirements are no longer onerous.
How are you using the latest version of FTK? Did I miss any new features that you have found useful?
Chad Tilbury, GCFA, has spent over ten years conducting computer crime investigations ranging from hacking to espionage to multi-million dollar fraud cases. He teaches FOR408 Computer Forensic Essentials and FOR508 Computer Forensic Investigations and Incident Response for the SANS Institute. Find him on Twitter @chadtilbury or at http://ForensicMethods.com.


As a Special Agent with the Air Force Office of Special Investigations, Chad served on the national computer intrusion team and helped expand counter-espionage techniques. At SANS, Chad is a senior instructor and co-author for FOR500 and FOR508.
Read more about Chad Tilbury