This blog was written by - Tim Conway with contributions, edits, and research from Ted Gutierrez and Kevin Perry

Looking at the Ukraine cyber-attacks through the various lenses of NERC CIP
Following the cyber-attacks which impacted the Ukrainian electric system on December 23, 2015 there were a number of public statements and discussions asking if the North American electric system was susceptible to similar targeted cyber-attacks and the impact such an attack would have. Now the electric sector is again facing more questions following the CBS news report on December 21, 2016, of yet another possible cyber-attack on the Ukrainian electric system and statements in the report suggesting that a targeted US electric grid attack would be even worse to those experienced in the Ukraine.
Similar to the discussions of a year ago, it is likely that two camps will emerge with numerous variations of familiar themes:
Position 1) This type of an attack would not work against the US system, due to the protections in place under the NERC CIP regulations and reliability focused investments over the past decades.
Position 2) The US electric system is more susceptible as it is highly automated and would suffer a longer outage period if manual restoration efforts were required.
The reality is more complicated than either of these positions and must take into consideration multiple variables, and like all things associated to NERC CIP, you must start the debate by saying "it depends." I will focus on providing some thoughts to consider when discussing these two positions.
The CIP that saved the world (aka Position 1)
The North American Electric Reliability Corporation (NERC) performs a number of key roles in ensuring the reliability of the electric system. These responsibilities range from standards development, events analysis, compliance audits, penalty enforcement, and operating the Electricity - Information Sharing and Analysis Center (E-ISAC). While NERC has developed many standards focused on the operation and planning of the Bulk Electric System (BES), I will focus only on the NERC Critical Infrastructure Protection (CIP) standards.
The CIP Standards have existed in one form or another for over a decade, with NERC enforcement authority going back to 2007. The CIP standards have been routinely included in the top ten lists of most violated NERC Reliability standards of all time. It indicates the challenges in implementing a balanced CIP program defined by appropriate cybersecurity controls and compliance approaches that capture and demonstrate performance and management of the program. The CIP Standards have changed and matured significantly over time and industry efforts continue to highlight those benefits and the overall strength of the regulation. The topic of shifting from compliance focused standards to a balanced regulation addressing reliability, cybersecurity, and compliance is featured in a November 3, 2015 SANS webcast titled "How NERC and CIP are making a difference". Following the Ukraine event, the topic of NERC CIP effectiveness was covered in a March 24, 2016 blog post, where Ted Gutierrez mapped the CIP controls that may have helped an organization in defending against a similar targeted attack. Later, in a May 25th, 2016 industry meeting Kevin Perry from the SPP Regional Entity delivered a presentation titled: "Would CIP Standards Have Saved the Ukraine". I have attempted to summarize the great work conducted by both individuals in the graphic below.
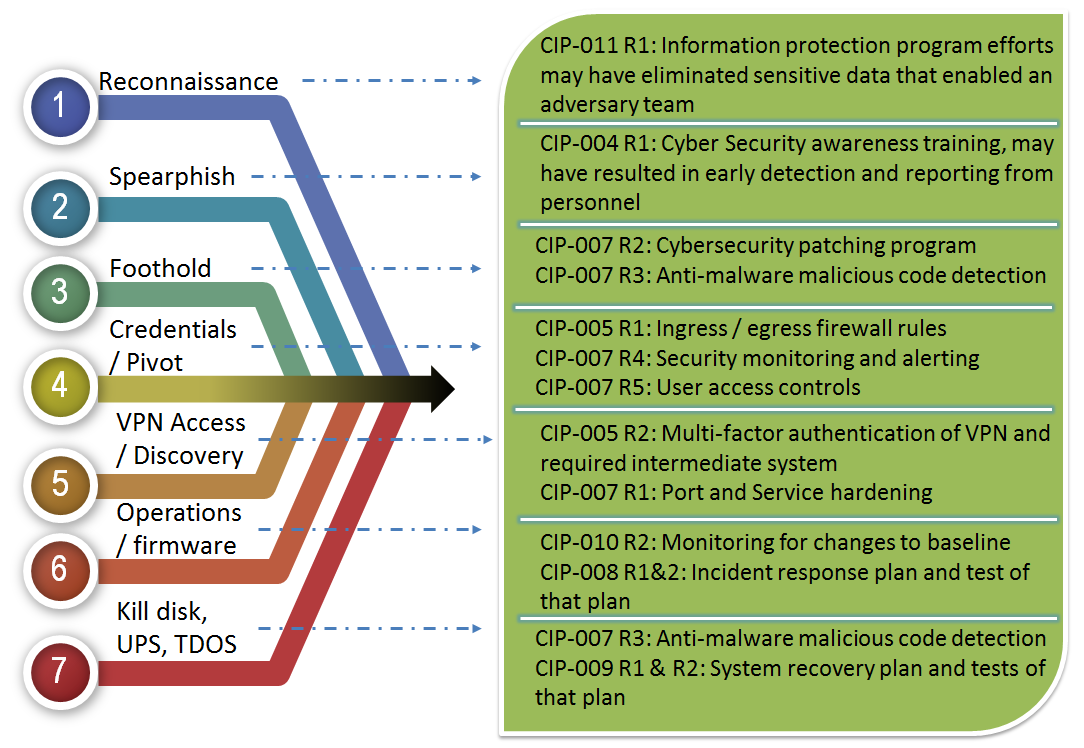
In the graphic above, the various adversary elements that were demonstrated during the Ukraine events of December 23, 2015 have been mapped to a mitigating control that is required in the current NERC CIP regulation. Based on this view without any additional context it would appear that CIP would have saved the day or at a minimum would have resulted in forcing the adversaries to utilize different capabilities or attack vectors. Now we will consider some of the nuances of this position that are important to understand during the discussions.
You must be this tall to ride
With the authority granted to NERC under the Federal Power Act, NERC governs the Bulk Power System (or Bulk Electric System (BES) of North America. The definition of BES has lots of inclusion and exclusion elements, however for simplicity consider transmission facilities operating at 100kV and above, generation resources, and Control Centers to be in scope. The lower voltage facilities are generally categorized as distribution level assets in the overall electric system. While the 2015 attacks in the Ukraine did target some substation environments operating at 110kV, the majority of the impacted substations were below 110kV and the way the Electric system is segmented in the country places those facilities under the control of the distribution operator not the bulk power system transmission operator (i.e. essentially the 110 kV circuits impacted were considered distribution-level assets).
The majority of the US electric distribution system (similar voltage level to most of the targeted Ukraine assets in 2015) does not fall under the NERC CIP regulations. The exception to this in North American are specific distribution elements (under frequency load shed, under voltage load shed, remedial action schemes, special protection systems and facilities associated with blackstart resources) that are subject to NERC CIP regulation consideration because of their potential impact on the BES.
For this reason, much confusion arose in discussions surrounding the effectiveness and sufficiency of NERC CIP to prevent a similar attack against the US electric system. If an adversary with similar capabilities selected three target North American organizations and attempted a copycat attack against distribution only level assets, they may never encounter an asset that was subject to the NERC CIP Standards. Just for the sake of clarity, this is not a surprise; the NERC Standards have always focused on protecting the most critical components of the electric system and enforcing requirements based on the Federal authority delegated to the ERO. Most distribution systems fall under state-level authority for any requirements or regulation.

Fifty shades of CIP
The next major nuance to include in the discussion around position 1 is the understanding that you need to specify which NERC CIP you are talking about. During the "old days" of CIP versions 1-3 if an asset was in scope and subject to CIP as an identified Critical Cyber Asset, then it was subject to the majority of the requirements - an everything for everything approach. CIP versions 5/6 introduced the concept of criteria based impact ratings as well as a systematic approach to grouping assets. This new paradigm resulted in the applicability of certain requirements to systems that are at a High impact rating criteria, fewer requirements for those systems at a Medium impact rating, fewer still for those at a Medium impact without external routable connectivity, and the least amount of requirements for those systems categorized as Low impact (again just for the sake of saying it - this is not a surprise. More requirements for the assets that by definition pose the greatest risk to the reliability of the electric system and fewer requirements for assets that pose a lower risk). Therefore, in a discussion about NERC CIP controls and the effectiveness of those controls in mitigating specific attacker capabilities or attack vectors, it is essential to establish an understanding of which CIP you are talking about.
When considering an assessment of the requirement by requirement applicability variations across the High, Medium, and Low impact criteria and what each set of required controls in a CIP program would look like, I considered an exercise we performed in our SANS ICS 456 course. In this exercise we leveraged an established and implemented framework for determining an entity's cyber capabilities and maturity, the ES-C2M2 (Electricity Subsector Cybersecurity Capability Maturity Model). Using this model we ran assessments against the CIP v5/6 Standards themselves, and developed capability and maturity reports for the requirements applicable at a High impact facility, a Medium impact, Medium impact with no ERC, and a Low impact system. These assessment reports help to quickly identify the variations in controls and effectiveness across the version 5/6 CIP programs.
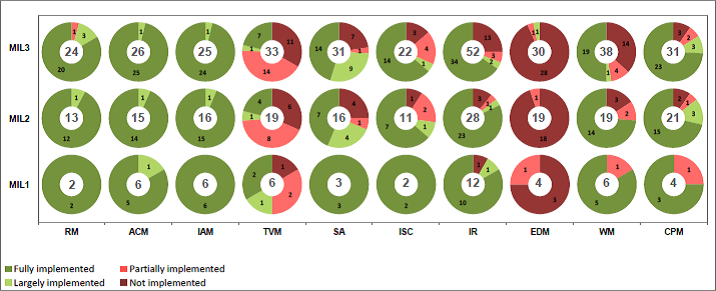
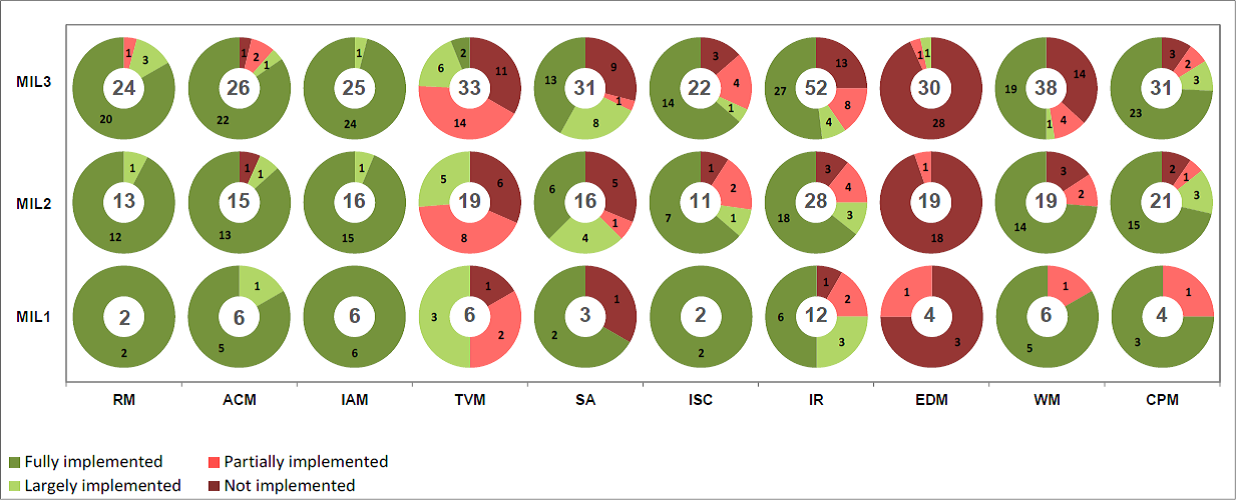
I have provided the resulting ES-C2M2 assessment reports of the CIP Standards for High, Medium, and Low impact programs. At a quick glance you can see which domains have coverage across the Maturity Indicator Levels, and which ones have gaps. The legend in the bottom left of the image indicates whether a control is Fully Implemented, Largely Implemented, Partially Implemented, or Not Implemented. Keep in mind this is an assessment of the Standards themselves, so it is really indicating the degree to which a control is required across the High, Medium, and Low impact ratings of NERC CIP and how that aligns with the MIL 1, 2, and 3 levels of ES-C2M2
First, the results of the High impact evaluation, including supporting information from the ES-C2M2 reports to help understand the output.
Next, the Medium Impact with ERC evaluation report:
And now the Medium Impact without ERC:
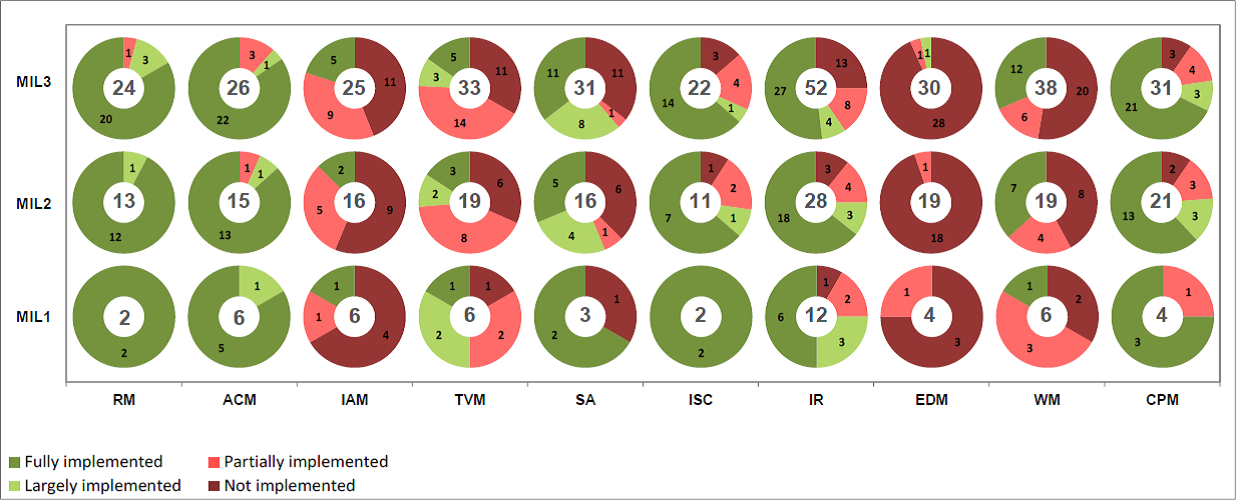
And last, the Low Impact evaluation:
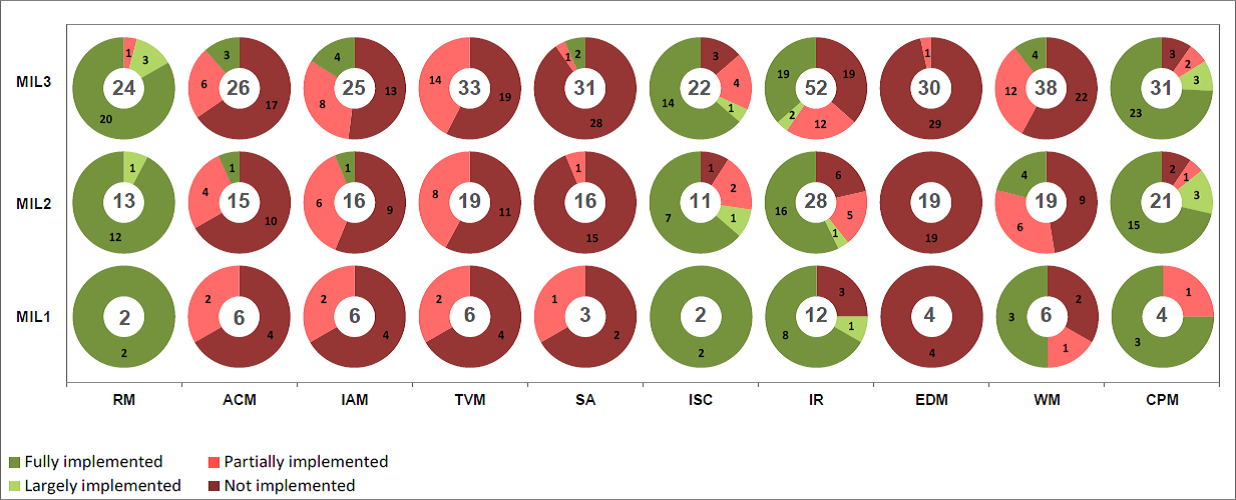
Based on the ES-C2M2 evaluations, a couple of things become immediately clear:
- We definitely need to change our discussions around the protections provided by NERC CIP, as there needs to be more specificity around which CIP you are talking about and something that may have been true in versions 1-3 may no longer be true in versions 5/6.
- All impact rating evaluations show strong capabilities in the Risk Management, Information Sharing and communications, as well as in Cybersecurity Program Management.
- All impact rating evaluations indicate weakness in Threat and Vulnerability Management as well as Supply Chain and External Dependencies Management domains.
- Regardless of associated impact rating level (H, M, or L) there is a tremendous amount of Cyber Assets that are now "in scope" of NERC CIP that previously were not included under entity defined Risk Based Assessment Methodologies. Many of these newly in scope Cyber Assets are at a Low impact level and as such there is a large number of electric entities that now have CIP programs due to the identification of Low Cyber Assets.
- The ES-C2M2 assessments shown above were performed on the CIP Standards directly. Meaning, the assessment output reports are a "perfect world" evaluation of the requirements not an entity implementation, which may not adequately or completely be performing what the requirement states.
Our similarities are greater than our differences (aka Position 2)
This position is largely based on a couple of basic theories;
- The engineering, architecture, and operation of the US electric system is not tremendously different than the systems found in the Ukraine.
- The amount of automation, communications inter-dependencies, and associated attack vectors in the US are similar or greater when compared to the impacted Ukrainian sites.
- The ability to roll vehicles, to dispatch personnel, and to perform manual operations may take longer in the US than it did at the impacted Ukrainian organizations due to the significant centralization efforts of dispatch and field personnel that has taken place here.
- There are far more potential target facilities and organizations to choose from in the US.
- With an understanding of an entities protections and controls in place, even at the highest NERC CIP impact level, there is an expectation that an adversary would bring appropriate tools and capabilities to counter those protections and controls to achieve its objectives.

Why CIP from a sub-requirement when you can gulp from a standard
Personally, I tend to sit in the position 2 group, however I am greatly encouraged by the voluntary efforts that organizations are pursuing to implement CIP beyond the specific applicable requirements. While there is likely not a definitive right or wrong position in this discussion, I believe it is important to make sure all parties engaged in this debate have a firm understanding of the scope and variations that exist amidst the CIP world.
It should also be recognized that a NERC Registered Entity can always choose to implement controls that go beyond what is required within the standards. This approach has been demonstrated by some North American entities who have internally implemented a common CIP Internal controls program across all systems regardless of the individual impact rating requirements for each system.
As CIP continues to grow and expand into areas previously not in scope, I anticipate an ever increasing set of standards that reaches the highest levels of capability and maturity across all domains. As many countries and other sectors look to CIP as a goal, CIP continues to raise the bar and move the goal post to ensure the reliability of the electric system we all rely on.
*Note - if you are interested in obtaining the ES-C2M2 worksheets developed in the CIP H, M, & L assessments, I will post the files in our ICS forum.
Tim Conway
If you're interest in attending ICS456: Essentials for NERC Critical Information Protection, I'm teaching at these upcoming events. http://www.sans.org/u/osf
To view all our upcoming courses and events, click here.
Free Stuff Reminder
- Download the "What Will Your Attack Look Like" poster here
- Get the latest ICS resources here
- Join the conversation in the ICS Community Forum where ICS professionals share lessons learned, ask questions and connect with others passionate about securing our critical infrastructure.




