SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsWalk through several new ICS Cheat Sheets to guide the community in answering critical ICS security questions.


Are you wondering which industrial control system (ICS) assets are commonly targeted and where to get critical security logs? Are you planning to conduct an ICS security program assessment at either a strategic or technical level? Maybe you want to map your existing program, or start a new one that aligns with important functions of the National Institute of Standards and Technology (NIST) Cybersecurity Framework to protect your control network. Or perhaps you just want to know more about the technical details of the industrial protocols in use on your ICS network.
We have just published several new ICS Cheat Sheets to guide the community in answering these and other critical ICS security questions. The tri-fold ICS Cheat Sheets are applicable to all ICS sectors. Let’s briefly walk through them together!

This Cheat Sheet is literally the “ABC’s” of the industrial control system security arena. It is a handy collection of the most commonly referenced acronyms used in SANS ICS courses, ranging from security for Operational Technology (OT) to Information Technology (IT). Terminology for critical engineering operations, security models, devices, and assets are covered, as are ICS applications for plant operations, with acronyms for everything from Active Cyber Defense Cycle (ACDC) to Human Machine Interface (HMI), Phasor Measurement Unit (PMU), Remote Terminal Unit (RTU), Safety Instrumented System (SIS), and Cross-Site Scripting (XSS).
Keep this ICS Cheat Sheet in your pocket for a handy reference if you’ve just entered the ICS engineering or security areas.
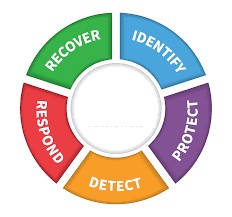
Applicable to any industrial control system sector, this Cheat Sheet covers the basics of using the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF). The Cheat Sheet concentrates on seven NIST CSF areas that help leadership, engineers, and administrators gauge the overall maturity of a new or established industrial security program and identify areas for risk reduction. The seven areas are Policies – ID.GV, Network Segmentation and Isolation – PR.AC, Access Control – PR.AC, Logging and Monitoring – DE.AE, Asset Inventory Management – ID.AM, Incident Response – RS.RP, and Security Awareness – PR.AT applied to the control environment. The NIST CSF is available at https://www.nist.gov/cyberframework.
Use this ICS Cheat Sheet to map key functions of the NIST CSF to what is important for a security program implemented to protect control system environments.

This Cheat Sheet provides basic yet technical considerations to kick-start an ICS security assessment. It covers risk surface evaluations, penetration testing, and red team assessments, and promotes defining the goals of an assessment, key personnel to include, and effective methods to gather the right data for evaluation. Vulnerability identification, network segmentation, and access control – all covered in this Cheat Sheet – are critical areas to understand when assessing ICS risk surfaces and how evaluation may impact operations.
Use this ICS Cheat Sheet to help support a paper-based or technical security assessment to identify general or technical gaps of a security program implemented to protect control environments, while at the same time considering safety and operations as the top priority.

This Cheat Sheet is all about planning industrial site visits by preparing and building relationships with teams before arriving, conducting ethical hacks of the physical security perimeter, discussing cybersecurity and safety discussions on site, and establishing a critical ICS asset inventory process. Organizing direct discussions on security and safety at the facility allows for direct observations and provides operational context for the environment where digital assets are located. For example, IT Security Awareness content is not enough for ICS Security Awareness training programs. This will guide teams to leverage the physical engineering safety culture by drawing parallels between physical safety and cyber “safety” events and sharing lessons learned from real-world ICS case studies such as CRASHOVERRIDE, TRISIS, HAVEX, STUXNET, etc.
Use this Cheat Sheet when preparing for site visits, starting an ICS asset inventory, and initiating discussions around what an impactful cyber event would be like in an environment and how to detect or prevent it.
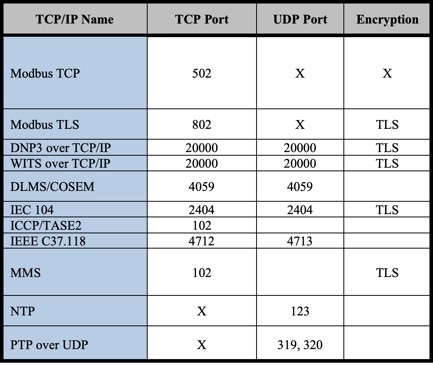
This Cheat Sheet brings together technical details about some of the most commonly used ICS protocols across several ICS sectors and global regions. It covers protocols across Fieldbus, Fieldbus Management, Site SCADA, and Regional SCADA areas, and also includes names, Ethernet types, port numbers, and available encryption capabilities. You can get details beyond what is provided by referring to the associated protocol specifications or vendor specifications.
Use this Cheat Sheet for security incident response, for engineering troubleshooting efforts when putting in place ICS network security monitoring, and for improving understanding of protocol types and usage in control networks.

This Cheat Sheet covers the basics of using Modbus Remote Terminal Unit (RTU) and Modbus Transmission Control Protocol (TCP) (available at https://www.modbus.org/). The sheet reviews their differences and provides an outline of the packet structure for both protocols for easy reference. It includes tables of read-and-write function codes, a primer on how to use a simple tool to interact with Modbus TCP clients on a network, and quick tips on using packet filters for Modbus and related exploit modules.
Use this specific Modbus RTU/TCP ICS Cheat Sheet to help dissect, understand, or troubleshoot Modbus commands on your control network(s).
Start with the ICS Acronyms Cheat Sheet to learn the common and key terminology used for the technologies, security models, critical assets, and processes in your environment. Once you have a foundational understanding, the ICS Cybersecurity Program Maturity Cheat Sheet will help you align a new or established program with the NIST Cybersecurity Framework applied to ICS. For more technical assessments, the ICS Security Assessment Cheat Sheet can be used to identify more technical controls or technology gaps to reduce ICS operational safety risks.
The ICS Site Visit Plan Cheat Sheet will help you will establish and maintain strong relationships to smooth ICS network security monitoring, incident response, and promote the role of ICS security in supporting the safety and reliability of operations. Once ICS-aware network security monitoring is deployed, the ICS Protocols and the Modbus RTU/TCP Cheat Sheets will help you examine network traffic and determine the specific ICS operating protocols in use – which in turn will help guide incident response investigations and engineering process troubleshooting.
Join the conversation in the ICS Community Forum, where more than 4,000 ICS professionals share lessons learned, ask questions, and connect with others passionate about securing our critical infrastructure. https://ics-community.sans.org.
The ICS Cheat Sheets, ICS Blogs and other ICS resources are available at https://www.sans.org/industrial-control-systems-security/
To learn more about Dean Parson's please check out his Biography and ICS Contributions.


Dean Parsons, CEO of ICS Defense Force, teaches ICS515 and co-authors ICS418, emphasizing ICS-specific detection, incident response, and security programs that support OT operations—aligning practitioners and leaders on clear, defensible action.
Read more about Dean Parsons