SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsUnderstanding how attacks work is critical for defense. It's a common theme in SANS Purple Team courses: offense informs defense and defense informs.

My previous blog focused on shifting mentality from Penetration Testing to Red Team and Purple Team. This blog post will focus on understanding and communicating how adversaries operate so that you can perform Red Team and Purple Team exercises.
Understanding how attacks work is critical for defense. It is a common theme in SANS Purple Team courses: offense informs defense and defense informs offense. There have been many attempts throughout the years to come up with a common framework for information security teams to speak the same language amongst: Digital Forensics and Incident Response (DFIR) investigating an attack, Cyber Threat Intelligence sharing the information about the attack, Blue Teams defending against the attacks, and Red Teams emulating the attacks.
In 2011, Lockheed Martin published Cyber Kill Chain as one of the first attempts to explain how attacks work. The Cyber Kill Chain covers 7 high level goals, or tactics, attackers perform during an attack. As one can see from the original publication, these 7 steps are very easy to understand and communicate:
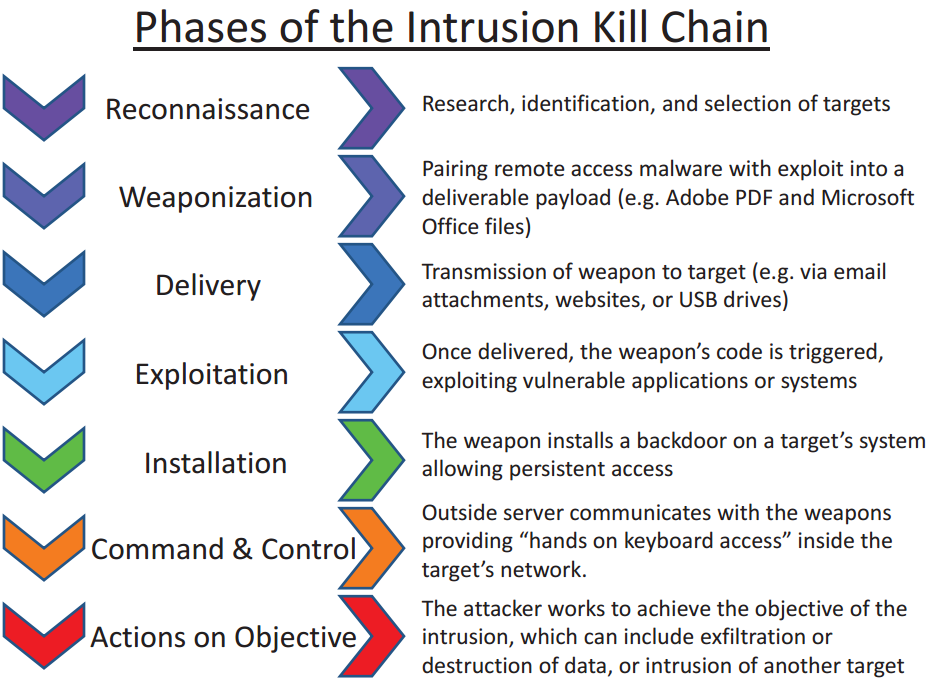
Lockheed Martin did a fantastic job in spreading the Cyber Kill Chain idea to high-level managers and CISOs. It seems that everyone has heard it and can articulate that the Cyber Kill Chain are the steps an adversary takes during an attack. Folks with military background are even quicker to grasp the concept given they are educated in what a Kill Chain is: a military concept which identifies the structure of an attack. Conversely, the idea of "breaking" an opponent's kill chain is a method of defense.
However, the Cyber Kill Chain covers only high level tactics (goals or phases) of an attack. This framework is great for speaking to non-practitioners about a particular attack, how it occurred, and maybe even discussing how the cyber kill chain can be broken by defenders before the attackers are successful.
In 2013, David Bianco, a SANS instructor, authored The Pyramid of Pain which covers the different forms of Cyber Threat Intelligence provided by Digital Forensics and Incident Response (DFIR) teams after an incident. The bottom of the pyramid focuses on Indicators of Compromise, while the top focuses on the most important part for Red Teams and Purple Team exercises: Tactics, Techniques, and Procedures.
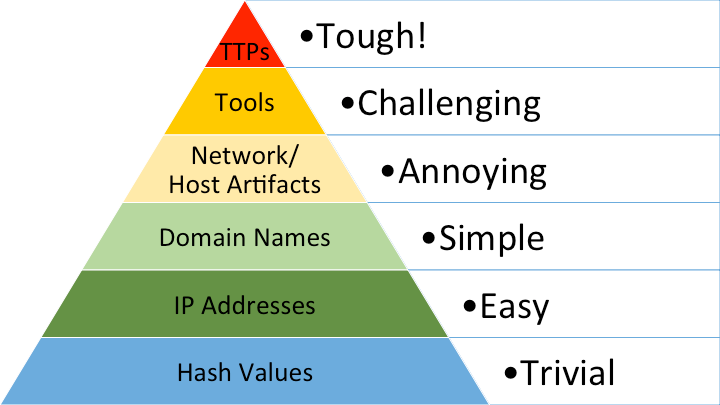
David published Tactics, Techniques, and Procedures (TTPs) as a single grouping and stated “at the apex are the TTPs. When you detect and respond at this level, you are operating directly on adversary behaviors, not against their tools. For example, you are detecting Pass-the-Hash attacks themselves (perhaps by inspecting Windows logs) rather than the tools they use to carry out those attacks. From a pure effectiveness standpoint, this level is your ideal. If you are able to respond to adversary TTPs quickly enough, you force them to do the most time-consuming thing possible: learn new behaviors.”
The focus on Tactics, Techniques, and Procedures (TTPs) is the mentality shift I spoke about when I blogged about shifting mentality from Penetration Testing to Red Team and Purple Team.
In 2015, MITRE released ATT&CK: Adversary Tactics, Techniques, and Common Knowledge. This is the current industry standard and most used framework for understanding and communicating how attacks work. It goes a step further than the Cyber Kill Chain by expanding the attackers' high level goals to 14 different tactics. It also covers the techniques and sub-techniques used by the attackers to achieve those goals. As of this writing, there are 188 techniques and 379 sub-techniques.
ATT&CK has grown significantly since 2015 thanks to community contributions and industry adoption. Today, it can map techniques to groups, software, and data sources for detection. It has really become the common language that allows Digital Forensics and Incident Response (DFIR) teams to share the adversary behaviors they saw during an incident, the Cyber Threat Intelligence teams to share the behaviors, the defenders to see if they have data sources and capabilities to detect and respond to those behaviors, and the offensive teams to emulate those same behaviors for testing during Red Team and Purple Team exercises.
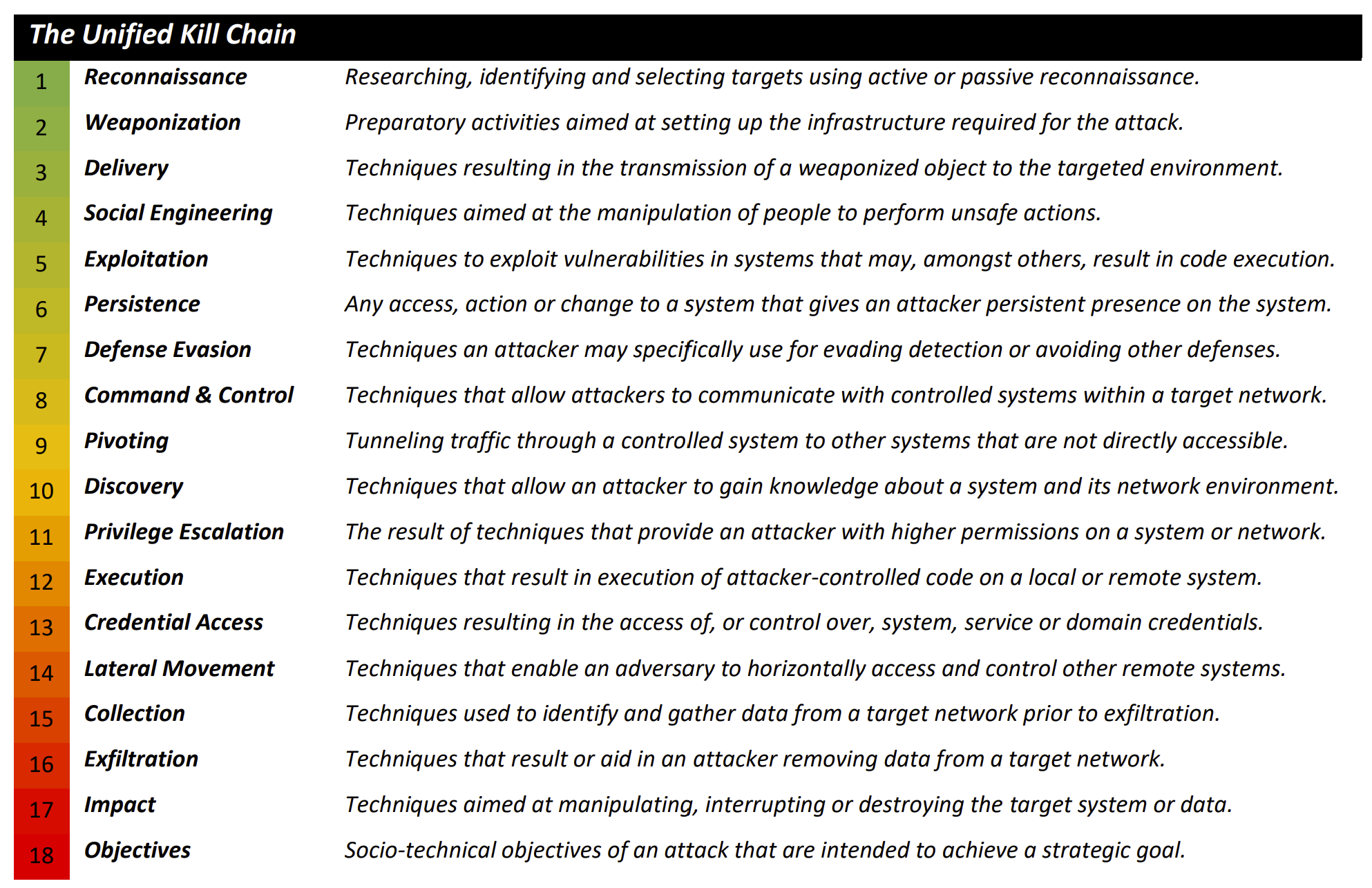
In 2017, Paul Pols published the Unified Cyber Kill Chain to overcome and expand on the Cyber Kill Chain. The Unified Cyber Kill Chain was originally a university paper bringing together a number of Cyber Kill Chains by various industry contributors such as Laliberte, Nachreiner, Bryant, and Malone, but the real focus was on Lockheed Martin Cyber Kill Chain and MITRE ATT&CK. The Unified Kill Chain takes from all of these frameworks and proposed 3 high level steps attackers take:
These three high level steps of an attack are even easier to understand for non-practitioners. Each high level tactic then dives into the techniques:
In 2022, Christopher Peacock from SCYTHE, published the TTP Pyramid. It builds on David Bianco’s Pyramid of Pain to break down Tactics, Techniques, and Procedures into their three individual categories:
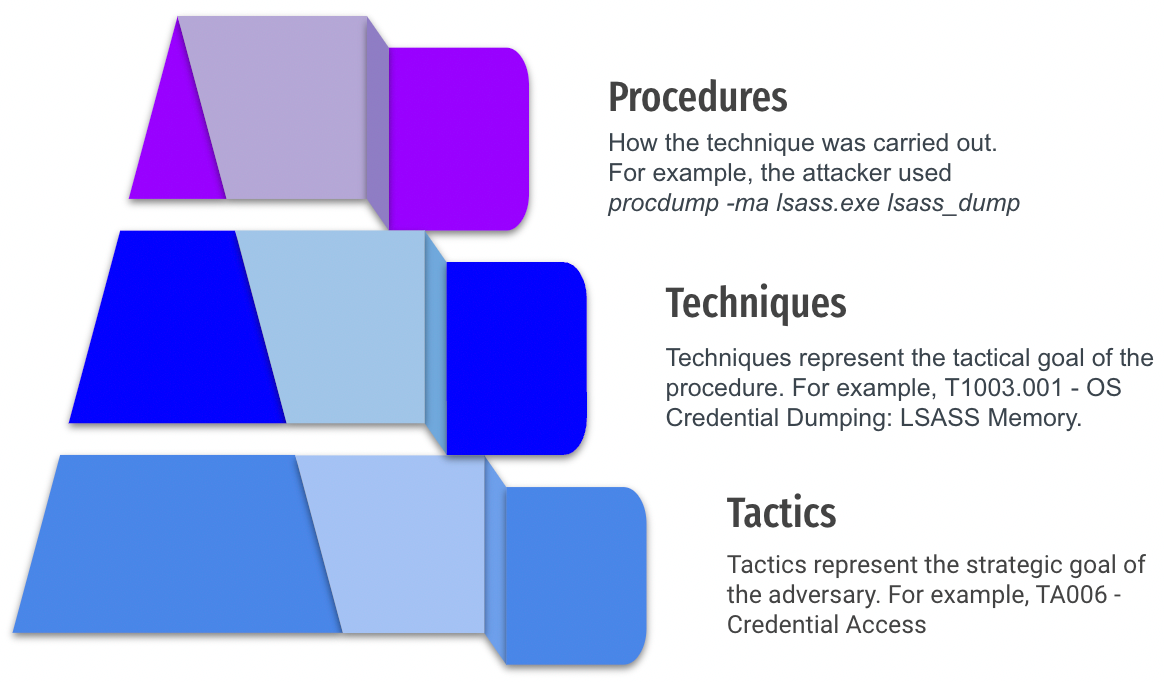
For Red Team and Purple Team Exercises, the procedures are the ideal level of intelligence we have on adversary behaviors. Of course we can still use the Cyber Kill Chain to explain the high level goals to non-practitioners and MITRE ATT&CK to have technique IDs mapped to groups, software, and data sources but to really emulate and determine if we have detection and response, the detailed procedures is the lowest, most technical level we can get while still leveraging frameworks that allow us to speak a common language.
With a good understanding of all the different frameworks for speaking a common language among information security teams, how do we actually run a Purple Team Exercise? For that, yours truly, with collaboration from the community and SCYTHE, have published the Purple Team Exercise Framework, a free and open-source step by step guide for running a Purple Team Exercise.
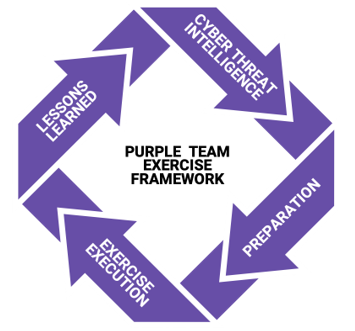
Our next blog posts and webcast will dive into running Purple Team Exercises leveraging the frameworks we have discussed in this post and go deeper into practical and actionable steps you can take to build out a successful Purple Team program.
SANS offers multiple 6-day courses covering the frameworks we have discussed in this post. For formal training, check them out:


Jorge Orchilles currently serves as a Senior Director at Verizon, where he leads the Readiness and Proactive Security Team. His team specializes in Exposure & Vulnerability Management, Penetration Testing, Red Team, Purple Team, and AI Red Team.
Read more about Jorge Orchilles