SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsCIS Released version 8.1 in June, 2024

Last updated: January 6, 2025
This blog was originally published on May 18, 2021 and updated on June 9, 2023.
On May 18, 2021, the Center for Internet Security (CIS) launched version 8 of its controls at RSA Conference 2021. The CIS Controls (formerly known as Critical Security Controls) are a recommended set of prioritized cyber defense best practices. They provide specific and actionable ways to protect against today's most pervasive and dangerous attacks. SANS provides CIS Controls v8 training, research, and certification.
Founded in 2000, CIS is a nonprofit organization whose mission is to improve cybersecurity readiness and response in the public and private sectors. CIS develops resources that help organizations develop cyber safeguards. CIS is most well-known for their CIS Controls and CIS Benchmarks. CIS Controls are safeguards that mitigate common cybersecurity risks, while CIS Benchmarks are configuration guidelines organizations can use to secure their systems and software.
CIS also oversees the Multi-State Information Sharing and Analysis Center (MS-ISAC) and the Election Infrastructure Information Sharing and Analysis Center (EI-ISAC). These organizations provide support, threat intelligence, and resources for state and local governments and election organizations in the US.
CIS released an update to the CIS Controls, version 8.1, in June 2024. This update introduced clearer guidance and alignment with other industry standards. Here’s what changed:
CIS added a "Governance" security function to align with the NIST Cybersecurity Framework 2.0. This update is intended to emphasize the importance of policies, procedures, and processes to an organization’s cybersecurity program.
CIS updated version 8.1 to align with the NIST Cybersecurity Framework 2.0. This creates consistency, improves usability, facilitates reporting and benchmarking, and allows organizations to more easily adopt multiple frameworks.
Asset classifications were revised to make them more consistent. The asset types Devices, Users, Applications, Data, Networks, Software, now include the new “Documentation” category, which covers plans, policies, and procedures. This makes it easier to manage their assets and align them with the Controls.
CIS added detailed definitions for terms like “sensitive data,” “plan,” and “process” to the glossary. For example, sensitive data is now defined as: “Physical or digital data stored, processed, or managed by the enterprise that must be kept private, accurate, reliable, and available.”
Lastly, to ensure the controls guidance is accurate and as actionable as possible, CIS updated the safeguard descriptions to make them easier to follow and corrected typos.
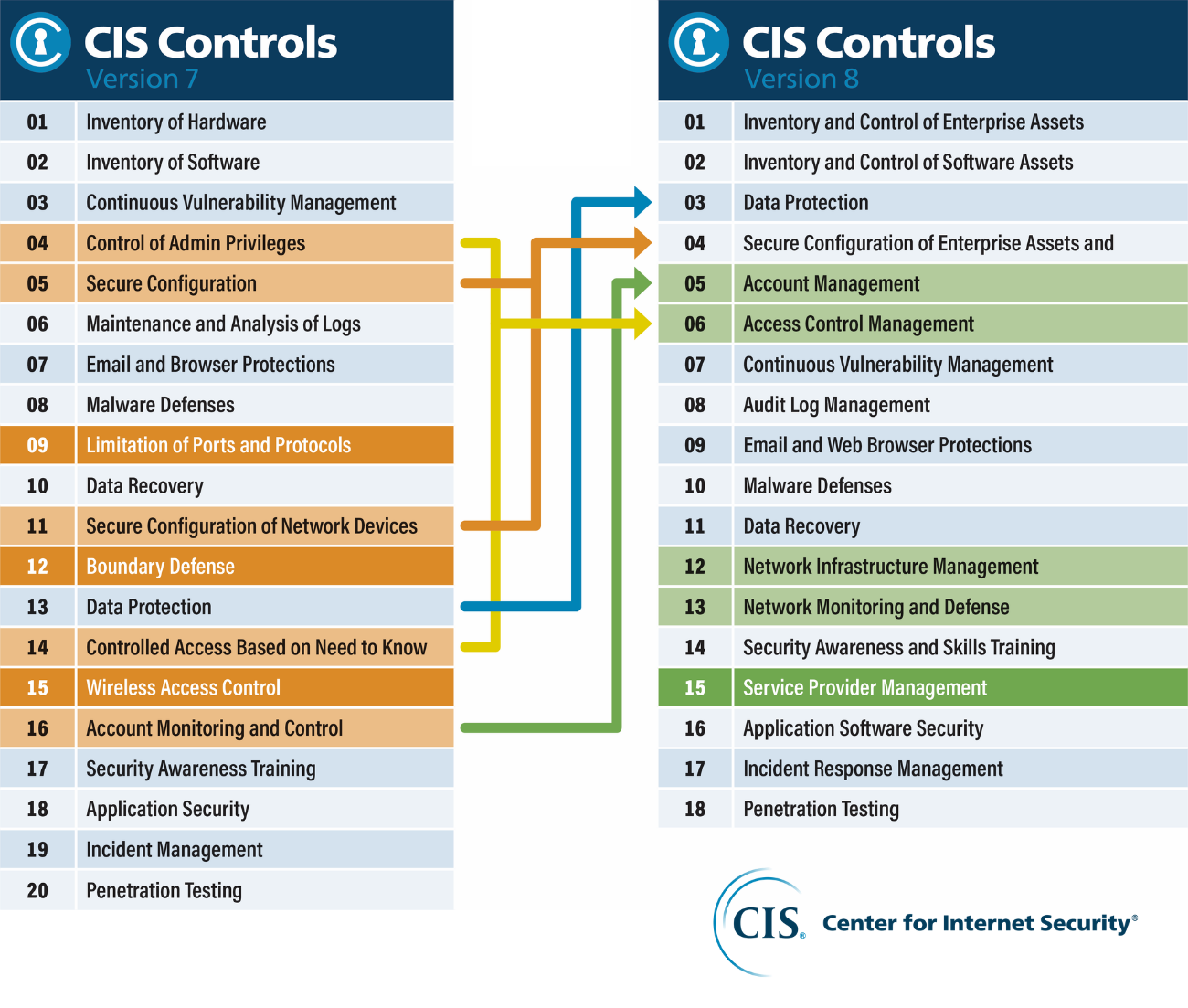
With v8, CIS enhanced its Controls to address modern threats to systems and software. Increases in cloud-based computing, virtualization, mobility, outsourcing, work-from-home, and changes in attack tactics prompted the update. CIS Controls address security of enterprises as they increasingly move to cloud and hybrid environments and utilize mobile technology.
CIS Control Safeguards have been segmented into implementation groups (IGs), IG1, IG2, and IG3. IG1 defines basic cyber hygiene and is the minimum standard of enterprise information security. IG1 is a set of 56 Safeguards that every enterprise should implement to guard against the most common attacks. IG2 builds upon IG1, while IG3 is composed of all controls and Safeguards.
Each Safeguard provides a single, focused task (when possible), details measurable actions, and defines metrics. The Safeguards are written in plain English to avoid misinterpretation.
A role-based controls focus is a thing of the past. Version 8 combines and consolidates the CIS Controls by activity, rather than by who manages the devices. Physical devices, fixed boundaries, and discrete islands of security implementation are less important; as reflected in version 8’s revised terminology and Safeguard groupings, resulting in reducing the number of Controls from 20 to 18.
Formerly called SANS Critical Security Controls (SANS Top 20), then “CIS Critical Security Controls,” the consolidated Controls are now officially called the “CIS Controls.” And while SANS transferred maintaining and improving the controls list to CIS in 2015, SANS continues to be a member of the CIS Controls editorial board.
The updated CIS Controls work in concert with and point to existing independent standards and security recommendations when available. CIS controls map to more than a dozen industry standard frameworks, including SOC2, HIPAA, MITRE ATT&CK, NIST, PCI DSS, and more. CIS provides a Controls Self Assessment Tool (CIS CSAT) to help organizations assess, track, and prioritize implementation of their CIS controls.
Whether you use the CIS Controls or another control framework to guide your security improvement program, it is critical to understand that a controls list is simply the starting point. With the release of version 8, CIS has also added new tools and guides to the CIS Controls ecosystem to help organizations:
Version 8 of the CIS Controls provides backwards compatibility with previous versions and a migration path for users of prior versions to move to v8.
The SANS Training and GIAC Certification focused on the CIS Controls, each has undergoing major updates to be in line with the new CIS Controls v8. Learn more about them here:
What's New with the CIS Controls v8?, Randy Marchany
Measuring Risk Using the Open, Collective Risk Model (CRM) , James Tarala, June 10, SANS webcast
What is Cloud Security Compliance?


Launched in 1989 as a cooperative for information security thought leadership, it is SANS’ ongoing mission to empower cybersecurity professionals with the practical skills and knowledge they need to make our world a safer place.
Read more about SANS Institute